|
|
This publication, and this picture page, wrap up a long work. It all began in 2007, when one of the authors went to the Moscow State University to test how a single-photon detector might react to a bright light:
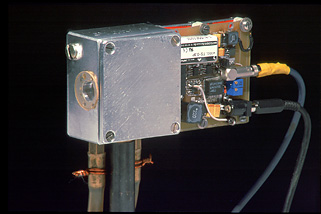
That modest experiment hinted at a new security problem in quantum cryptography. The work went on, and in early 2009 we were ready to go to Singapore and try our teeth on a real quantum key distribution system. Before flying there, a colorful suitcase was prepared to house an eavesdropper:
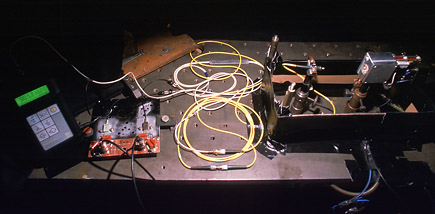
Once in Singapore at the Centre for Quantum Technologies, we first confirmed in the lab that their receiver Bob was controllable by our eavesdropper Eve, which meant the vulnerability to exploit was there:
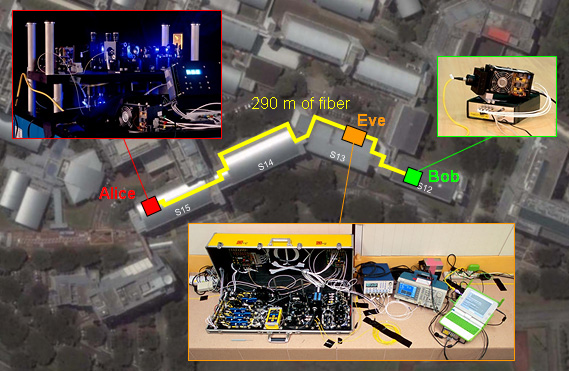
Then, we decided to demonstrate the eavesdropping full-scale, targeting the fully-developed quantum key distribution system previously built in Singapore (by the way its software was open-sourced). All the local researchers who built this system worked hard to tune it into perfect operation:
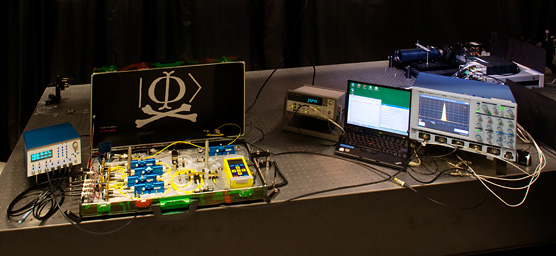
Together with the folks in Singapore, a full eavesdropper was built, in a larger suitcase:
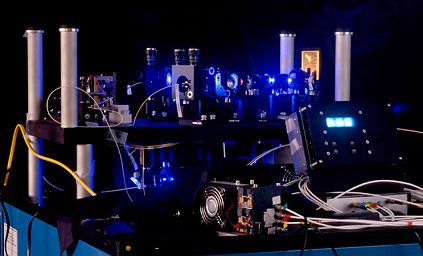
The entire experiment was rehearsed in a lab:
Then Alice, Eve and Bob were moved to separate locations:
Qin and Ilja worked to set up the quantum and classical parts of Eve:
After two nights of the final experiment and data recording, everyone was tired but happy:
In this experiment done in July 2009, the full secret key was eavesdropped by Eve on a running quantum key distribution link, without alerting the legitimate users Alice and Bob. To our knowledge, this was the first such full implementation of Eve. We reported preliminary results of this experiment at conferences; video recordings of two 50-minute talks are available on YouTube: one given at Hacking at Random 2009, and another at Chaos Communication Congress 2009.
Shortly after this experiment, we discovered that the same vulnerability existed in commercial quantum key distribution systems, allowing in principle to crack them as well. This was published in Nature Photonics in 2010. However, no eavesdropper was built for the commercial systems and thus no secret key extraction was done there, which made possible a faster publication.
The work presented on this page and now published in Nature Communications took longer to finish. Here we postponed till after the experiment a substantial amount of programming and processing of the recorded data, to verify that the complete secret key extraction took place. The classical part of the quantum key distribution protocol which Eve had to crack using the recorded data was not simple, so programming this took extra time. We hit a few unexpected snags in the process, and eventually cleared them. The key extraction has been implemented twice by two independent sub-teams among the authors, to verify that our results and claims are correct. As a supplementary to both the journal article and the preprint, we’ve made available a sample of eavesdropped data and a script used to extract the secret key from it (74 MiB ZIP archive; its content is described in the article). Don’t worry, the key extraction script runs fast and could be used in real-time; it has just taken us long to polish it.
What next? Havind done perfect eavesdropping, we’re now working on a perfect countermeasure to it, to secure once and for all against any device imperfections. This will take some effort, too.
Selected press coverage
in English:
Physics World |
BBC |
InformationWeek |
Slashdot |
The Register |
computing.co.uk |
Photonics Spectra |
in Norwegian:
digi.no |
ABC Nyheter |
in Spanish:
ALT1040 |
in Polish:
Gazeta.pl |
in Russian:
Компьюлента |
Лента.Ру.
Page authored by Vadim Makarov.
| |  |
|